
Threat analysts have discovered a new obfuscation technique used by the Hive ransomware gang, which involves IPv4 addresses and a series of conversions that eventually lead to downloading a Cobalt Strike beacon.
Code obfuscation is what helps threat actors hide the malicious nature of their code from human reviewers or security software so that they can evade detection.
There are numerous ways to achieve obfuscation, each with its own set of pros and cons, but a novel one discovered in a an incident response involving Hive ransomware shows that adversaries are finding new, stealthier ways to achieve their goal.
Sentinel Labs analysts report on the new obfuscation technique, that they call “IPfuscation”, and which is yet another example of how effective simple but smart methods can be in real-world malware deployment.
From IP to shellcode
The analysts discovered the new technique while analyzing 64-bit Windows executables, each containing a payload that delivers Cobalt Strike.
The payload itself is obfuscated by taking the form of an array of ASCII IPv4 addresses, so it looks like an innocuous list of IP addresses.
In the context of malware analysis, the list may even be mistaken for hard-coded C2 communication information.
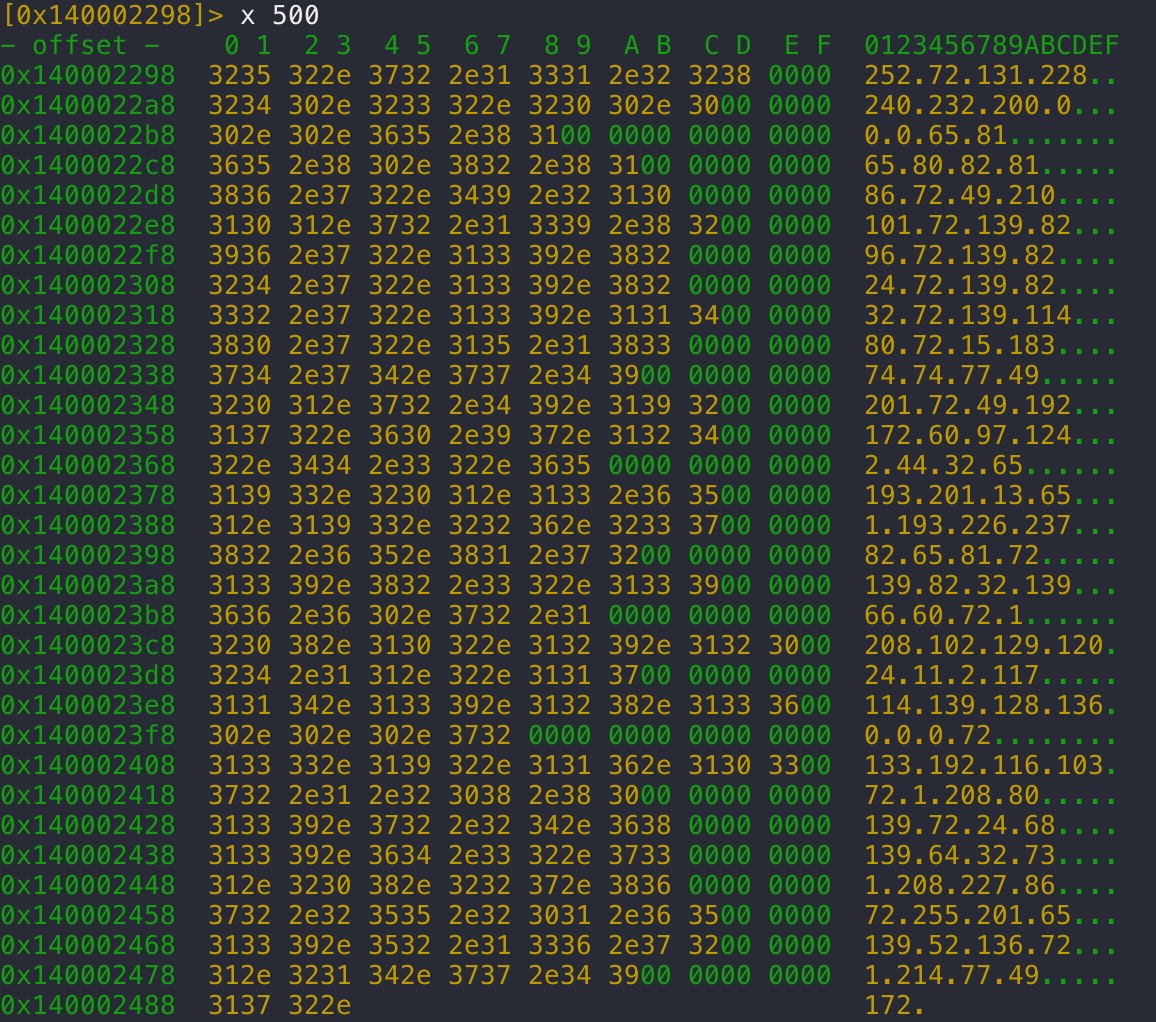
(Sentinel Labs)
When the file is passed to a converting function (ip2string.h) that translates the string to binary, a blob of shellcode appears.
Once this step has been completed, the malware executes the shellcode either via direct SYSCALLs or by proxying execution via callback on the user interface language enumerator (winnls.h), resulting in a standard Cobalt Strike stager.
Here’s an example from the Sentinel Labs report:
The first hardcoded IP-formatted string is the ASCII string “252.72.131.228”, which has a binary representation of 0xE48348FC (big endian), and the next “IP” to be translated is “240.232.200.0”, which has a binary representation of 0xC8E8F0.
Disassembling these “binary representations” shows the start of shellcode generated by common penetration testing frameworks.
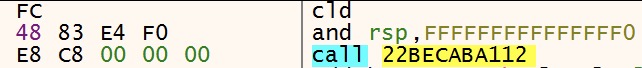
(Sentinel Labs)
The analysts have discovered additional IPfuscation variants that instead of IPv4 addresses use IPv6, UUIDs, and MAC addresses, all operating in an almost identical manner as what we described above.
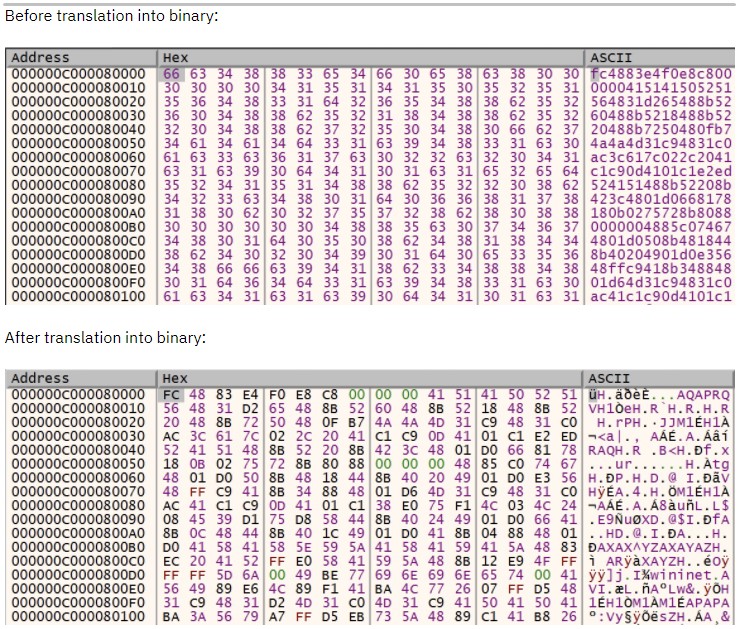
(Sentinel Labs)
The takeaway from this is that relying solely on static signatures for malicious payload detection is not enough these days.
Behavioral detection, AI-assisted analysis, and holistic endpoint security that aggregates suspicious elements from multiple points would have a better chance at lifting the lid of IPfuscation, the researchers say.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now