
Microsoft now allows Windows users to block drivers with known vulnerabilities with the help of Windows Defender Application Control (WDAC) and a vulnerable driver blocklist.
The new option is part of the Core Isolation set of security features for devices that use virtualization-based security.
It works on devices running Windows 10, Windows 11, and Windows Server 2016 and above with hypervisor-protected code integrity (HVCI) enabled and on Windows 10 systems in S mode.
WDAC, the software-based security layer that blocks the vulnerable drivers, protects Windows systems against potentially malicious software by ensuring that only trusted drivers and apps can run, blocking malware and unwanted software from launching.
The vulnerable driver blocklist used by this new Windows security option is kept up to date with the help of independent hardware vendors (IHVs) and Original Equipment Manufacturers (OEMs). Drivers can also be submitted for security analysis via the Microsoft Security Intelligence Driver Submission page.
It hardens Windows systems against third party-developed drivers with any of the following attributes:
- Known security vulnerabilities that attackers can exploit to elevate privileges in the Windows kernel
- Malicious behaviors (malware) or certificates used to sign malware
- Behaviors that are not malicious but circumvent the Windows Security Model and can be exploited by attackers to elevate privileges in the Windows kernel
The "Microsoft Vulnerable Driver Blocklist" option can be toggled on from Windows Security > Device security > Core isolation.
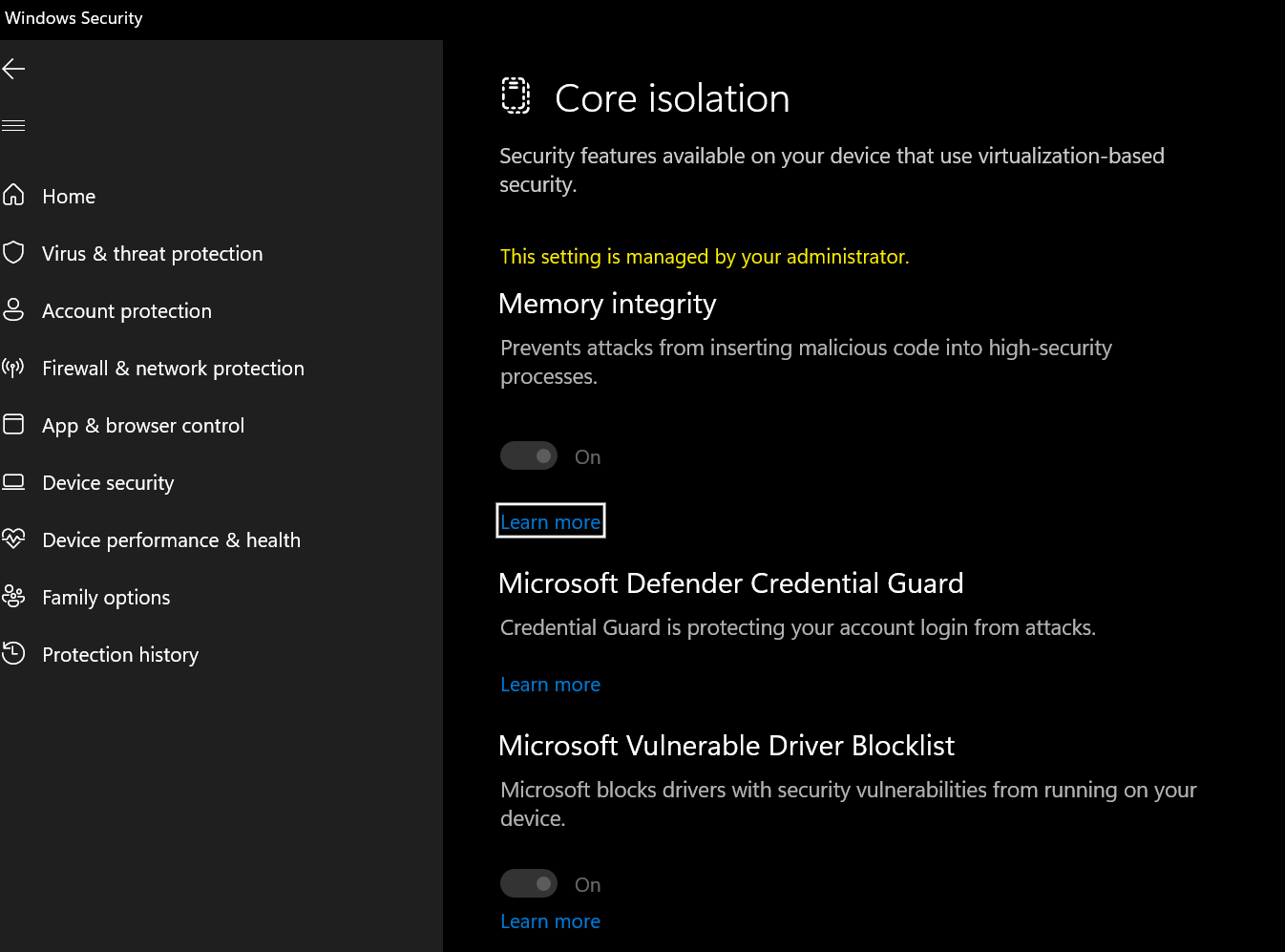
Once enabled, it blocks certain drivers based on their SHA256 hash, based on file attributes such as the filename and version number, or on the code signing certificate used to sign the driver.
This feature will also cause legitimate programs not to work, such as Cheat Engine and Process Hacker, as their drivers are blocked.
"Blocking kernel drivers without sufficient testing can result in devices or software to malfunction, and in rare cases, blue screen," Microsoft also warns.
"It's recommended to first validate this policy in audit mode and review the audit block events."
A Microsoft spokesperson was not available for comment when contacted by BleepingComputer earlier today.
Microsoft also plans to launch a new deployment service for drivers and firmware (as a public preview starting with the first half of 2022) to give Windows admins complete control over driver updates by allowing them to select the right drivers for devices on their enterprise networks.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now