
F5 has issued a security advisory warning about a flaw that may allow unauthenticated attackers with network access to execute arbitrary system commands, perform file actions, and disable services on BIG-IP.
The vulnerability is tracked as CVE-2022-1388 and has a CVSS v3 severity rating of 9.8, categorized as critical. Its exploitation can potentially lead up to a complete system takeover.
According to F5's security advisory, the flaw lies in the iControl REST component and allows a malicious actor to send undisclosed requests to bypass the iControl REST authentication in BIG-IP.
Due to the severity of the vulnerability and the widespread deployment of BIG-IP products in critical environments, CISA (Cybersecurity and Infrastructure Security Agency) has also issued an alert today.
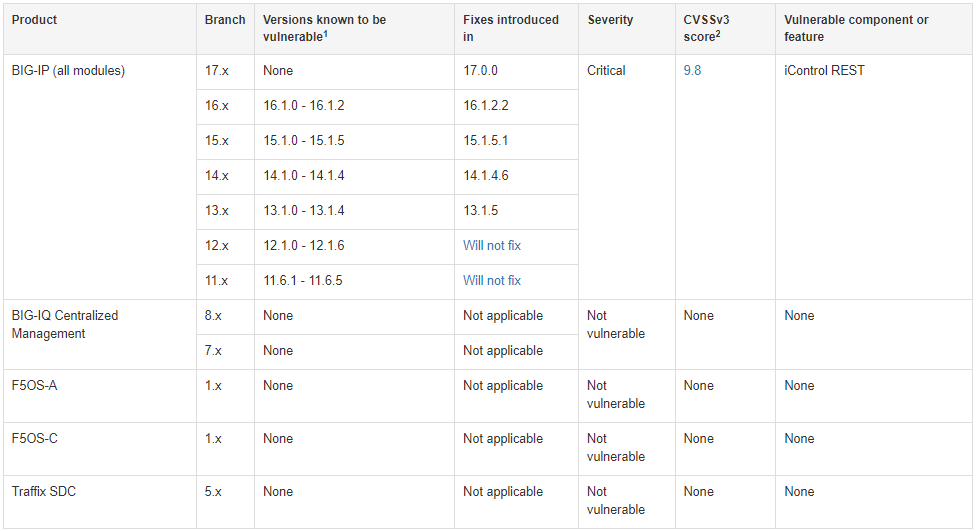
The complete list of the affected products is given below:
- BIG-IP versions 16.1.0 to 16.1.2
- BIG-IP versions 15.1.0 to 15.1.5
- BIG-IP versions 14.1.0 to 14.1.4
- BIG-IP versions 13.1.0 to 13.1.4
- BIG-IP versions 12.1.0 to 12.1.6
- BIG-IP versions 11.6.1 to 11.6.5
F5 has introduced fixes in v17.0.0, v16.1.2.2, v15.1.5.1, v14.1.4.6, and v13.1.5. The branches of 12.x and 11.x will not receive a fixing patch.
Also, the advisory clarifies that BIG-IQ Centralized Management, F5OS-A, F5OS-C, and Traffic SDC are not impacted by CVE-2022-1388.
F5 has provided the following three effective mitigations that may be used temporarily for those who can't apply the security updates immediately.
Block all access to the iControl REST interface of your BIG-IP system through self IP addresses, restrict access only to trusted users and devices via the management interface, or modify the BIG-IP httpd configuration.
F5 has provided all the details on how to do the above in the advisory, but some methods like blocking access completely may impact services, including breaking high availability (HA) configurations. As such, applying the security updates is still the recommended pathway to follow, if possible.
Finally, F5 has released a more generic advisory to cover an additional set of 17 high-severity vulnerabilities discovered and fixed in BIG-IP, so make sure to check that one too.
Over 16,000 BIG-IP devices exposed
With F5 BIG-IP devices commonly used in the enterprise, this vulnerability presents a significant risk for allowing threat actors to gain initial access to corporate networks.
To make matters worse, instead of the enterprise properly securing BIG-IP devices, security researcher Nate Warfield has seen the amount of publicly exposed devices significantly increase since 2020.
https://t.co/80tShneNwK - When CVE-2020-5902 dropped there were ~10k F5 management interfaces exposed online.
— Nate Warfield | #StandWithUkraine (@n0x08) May 4, 2022
Today there are 16k (https://t.co/2JPkVZwH5X is the @shodanhq query I use)
The trend data from Shodan would imply nobody learned to lock these things down pic.twitter.com/yC1oEbEZk9
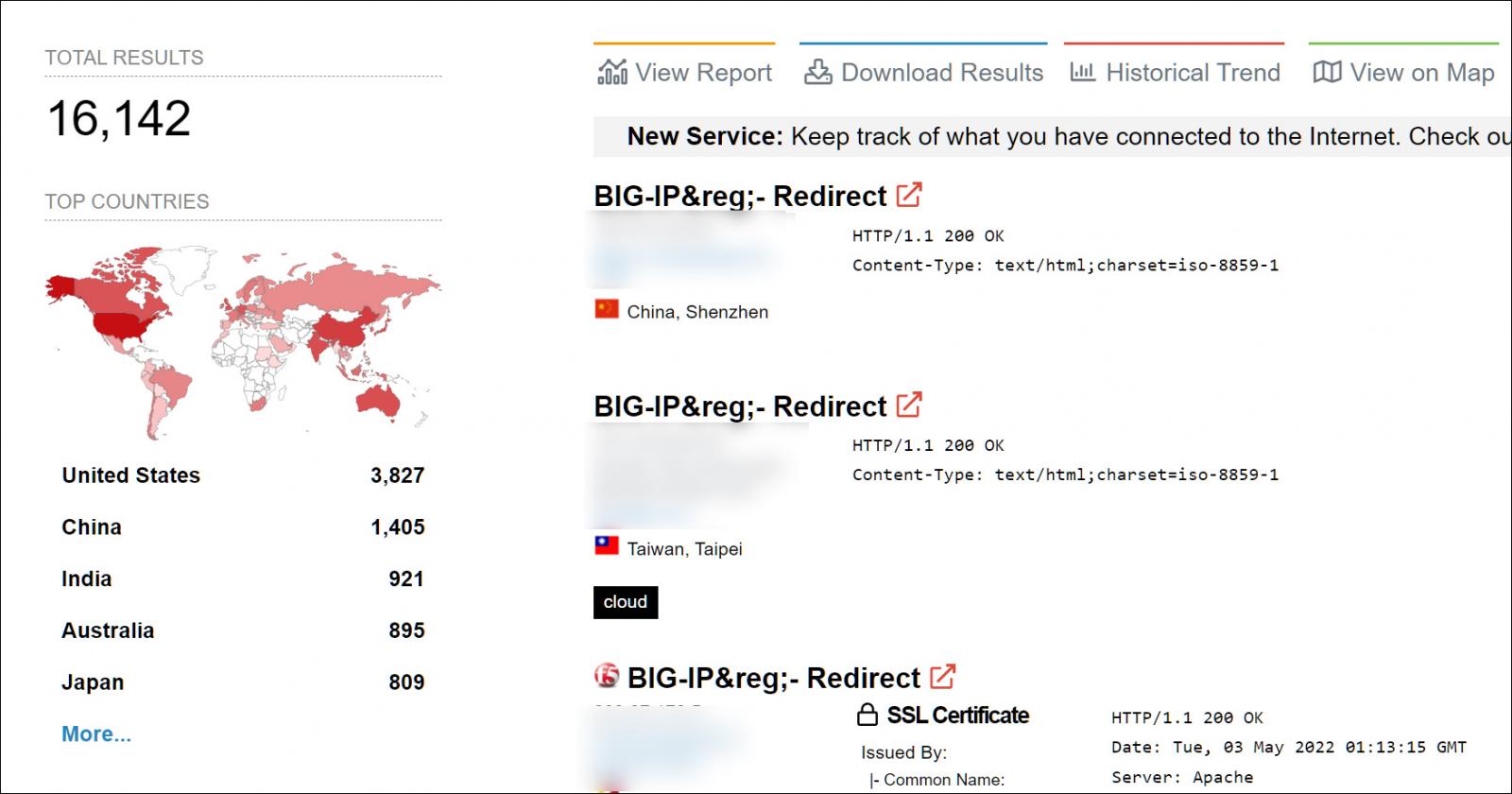
Using the query shared by Warfield, Shodan shows that there are currently 16,142 F5 BIG-IP devices publicly exposed to the Internet. Most of these devices are located in the USA, followed by China, India, Australia, and Japan.
Security researchers have already started narrowing down the location of the vulnerability, and it wouldn't be surprising to see threat actors begin scanning for vulnerable devices shortly.
Therefore, network admins must patch these devices as soon as possible or at least apply the supplied mitigations.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now