
Microsoft has added XLM macro protection for Microsoft 365 customers by expanding the runtime defense provided by Office 365's integration with Antimalware Scan Interface (AMSI) to include Excel 4.0 (XLM) macro scanning.
AMSI was introduced in 2015, and it has been adopted by all major antivirus products available for the Windows 10 platform since then.
It allows Windows 10 services and apps to communicate with security products and request runtime scans of potentially dangerous data.
This helps expose malicious intent even when hidden using heavy obfuscation and to detect and block malware abusing Office VBA macros and PowerShell, JScript, VBScript, MSHTA/Jscript9, WMI, or .NET code, regularly used to deploy malware payloads via Office document macros.
Microsoft first extended support for its Antimalware Scan Interface (AMSI) to Office 365 client applications in 2018 to defend customers against attacks using VBA macros.
"The recent AMSI instrumentation in XLM directly tackles the rise of malware campaigns that abuse this feature," Microsoft said.
"Because AMSI is an open interface, other antivirus solutions can leverage the same visibility to improve protections against threats."
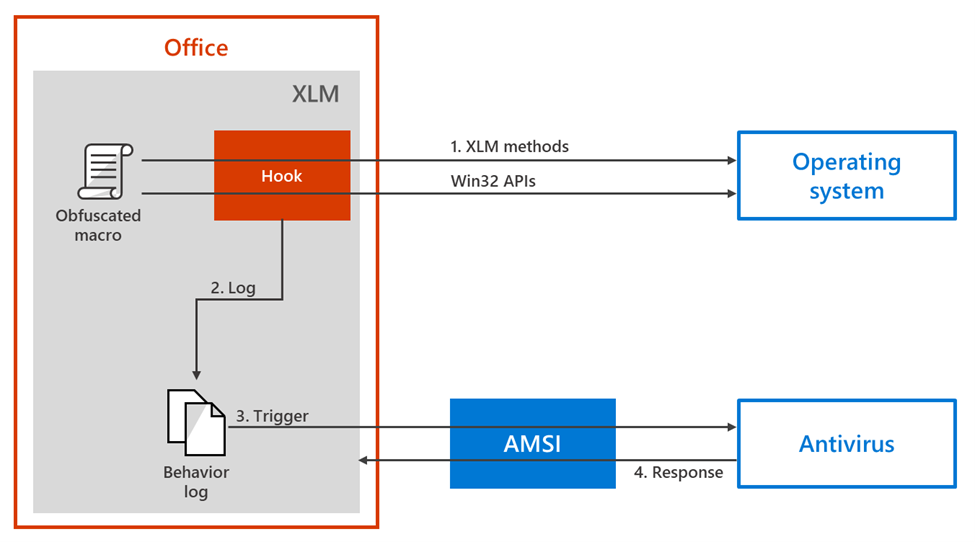
Since AMSI started allowing Office 365 apps to block malicious VBA macros, attackers such as the ones behind Trickbot, Zloader, and Ursnif have migrated to using XLM-based malware to evade static analysis and infect their targets with malware.
"While more rudimentary than VBA, XLM is powerful enough to provide interoperability with the operating system, and many organizations and users continue to use its functionality for legitimate purposes," Microsoft said.
"Cybercriminals know this, and they have been abusing XLM macros, increasingly more frequently, to call Win32 APIs and run shell commands."
With this latest improvement to Office 365, antivirus solutions like Microsoft Defender Antivirus can detect malicious XLM macros and stop malware using them in its tracks.
It also enables them to detect a broader range of malware and force more granular restrictions on what macros are permitted to do at runtime.
"The visibility provided by AMSI leads to significant improvements in generic and resilient signatures that can stop waves of obfuscated and mutated variants of threats," Microsoft added.
"Administrators can now use the existing Microsoft 365 applications policy control to configure when both XLM and VBA macros are scanned at runtime via AMSI."
Admins can download the latest group policy template files for Microsoft 365 Apps from the Microsoft 365 download center.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now