
Western Digital has fixed a security vulnerability that enabled attackers to brute force SanDisk SecureAccess passwords and access the users' protected files.
SanDisk SecureAccess (now rebranded to SanDisk PrivateAccess) allows storing and protecting sensitive files on SanDisk USB flash drives.
"SanDisk SecureAccess 3.02 was using a one-way cryptographic hash with a predictable salt making it vulnerable to dictionary attacks by a malicious user," Western Digital explained in a security advisory issued Wednesday.
"The software also made use of a password hash with insufficient computational effort that would allow an attacker to brute force user passwords leading to unauthorized access to user data."
The flaw (CVE-2021-36750) stemming from the key derivation function issues presented above has been addressed with the release of SanDisk PrivateAccess Version 6.3.5, which now uses PBKDF2-SHA256 together with a randomly generated salt.
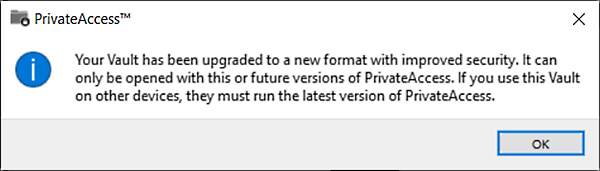
How to upgrade to PrivateAccess Vault
You can find detailed information here on upgrading your installation and migrating the SecureAccess Vault to the new PrivateAccess Vault.
This requires updating the iXpand Drive mobile app and the Windows and macOS Desktop to the latest released versions.
"We urge our customers to install this software update immediately to keep their vaults secure," Western Digital added.
"As with any upgrade, it is best to back up your data before installing the upgrade. Back up your data using the built-in Backup function in the Tools menu."
In related news, Western Digital confirmed a speed crippling SN550 SSD flash change in August (with writing speed decreases of up to 50%) after replacing the NAND flash memory in the WD Blue SN550, one of its most popular M.2 NVMe SSD models.
While it failed to alert customers of the change, the company said that, in the future, it would also introduce new model numbers when making hardware changes impacting its' products' performance.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now