
A newly discovered and uncommonly stealthy Advanced Persistent Threat (APT) group is breaching corporate networks to steal Exchange (on-premise and online) emails from employees involved in corporate transactions such as mergers and acquisitions.
Mandiant researchers, who discovered the threat actor and now track it as UNC3524, say the group has demonstrated its "advanced" capabilities as it maintained access to its victims' environments for more than 18 months (in some cases).
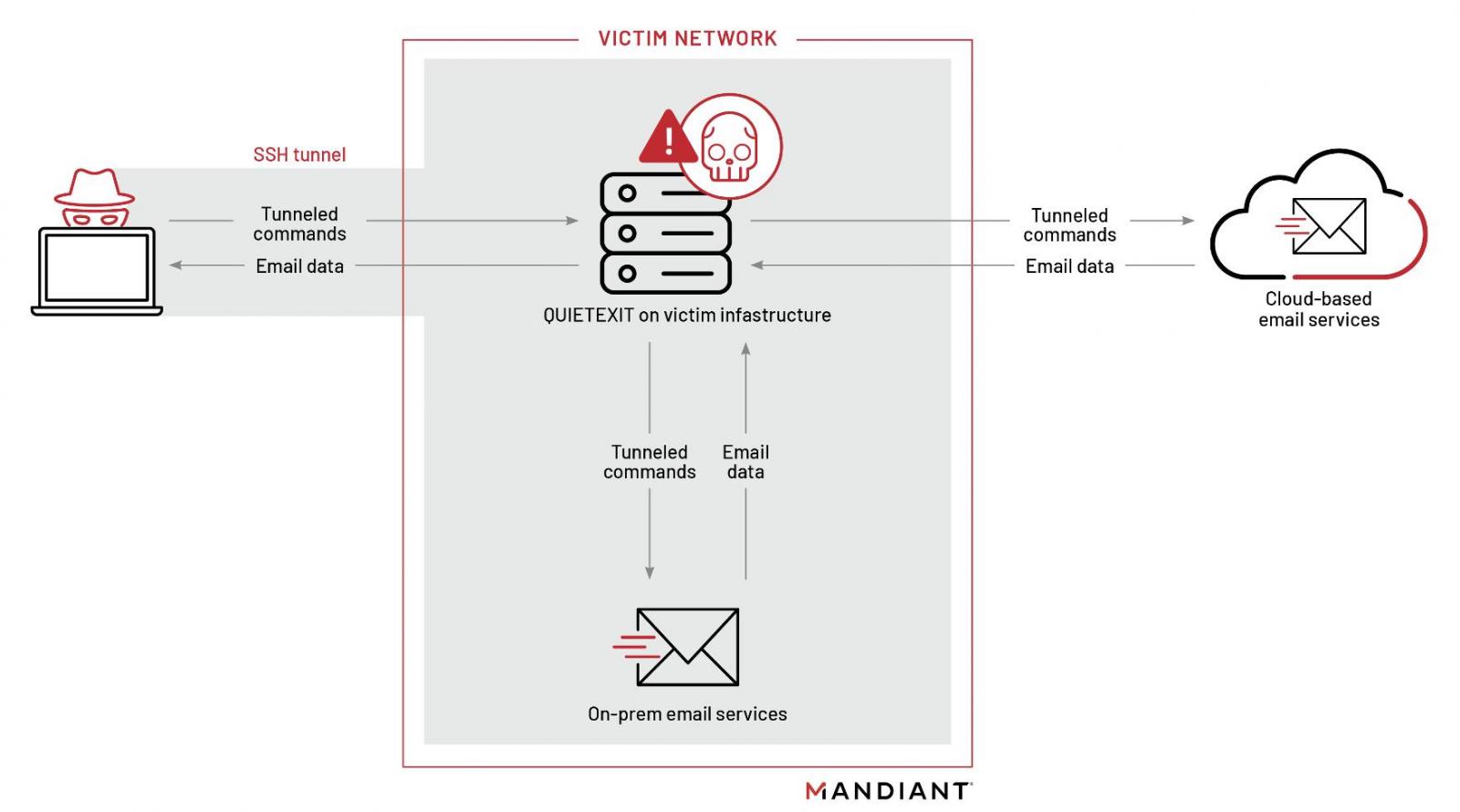
"Once UNC3524 successfully obtained privileged credentials to the victim's mail environment, they began making Exchange Web Services (EWS) API requests to either the on-premises Microsoft Exchange or Microsoft 365 Exchange Online environment," Mandiant said.
"In each of the UNC3524 victim environments, the threat actor would target a subset of mailboxes, focusing their attention on executive teams and employees that work in corporate development, mergers and acquisitions, or IT security staff."
UNC3524 can persist by deploying a newly found backdoor dubbed QUIETEXIT (developed using the open-source Dropbear SSH software as inspiration) on network appliances with no support for security monitoring and malware detection tools.
In some attacks, UNC3524 has also deployed the reGeorg web shell (a version linked by the NSA to the Russian-sponsored APT28/Fancy Bear group) on DMZ web servers to create a SOCKS tunnel as an alternate access point into its victims' networks.
By deploying its malware on these devices (e.g., wireless access point controllers, SAN arrays, and load balancers), UNC3524 greatly extends the interval between initial access to when victims detect its malicious activity and cut off access.
However, even when that happens, Mandiant says the threat group "wasted no time re-compromising the environment with a variety of mechanisms, immediately restarting their data theft campaign."
The QUIETEXIT backdoor command-and-control servers are part of a botnet built by compromising Internet exposed LifeSize and D-Link IP videoconferencing camera systems, likely with default credentials.
After gaining access and deploying its backdoors, UNC3524 obtained privileged credentials to their victims' mail environment and started targeting on-premises Microsoft Exchange or Microsoft 365 Exchange Online mailboxes via Exchange Web Services (EWS) API requests.
They usually steal all emails received by "executive teams and employees that work in corporate development, mergers and acquisitions, or IT security staff" over a specific date range instead of picking emails of interest or using keyword-filtering (this is a tactic used by Russian-backed Cozy Bear/APT29).
Given that UNC3524 has used tactics and tools previously linked to multiple Russian-backed hacking groups (including APT28 and APT29), Mandiant said that attribution is hazy and cannot link this activity to a specific threat group.
Update: Corrected info on initial access vector.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now