
Emsisoft has released a decryptor for the SynAck Ransomware, allowing victims to decrypt their encrypted files for free.
The SynAck ransomware gang launched its operation in 2017 but rebranded as the El_Cometa gang in 2021.
As part of this rebranding, the threat actors released the master decryption keys and documentation for their encryption algorithm on their Tor data leak site.
SynAck decryptor released
Today, Emsisoft has released a SynAck ransomware decryptor that works on all variants and allows victims to recover their files for free.
Works for both RSA and ECIES (secp192r1) variants. Thanks @kaspersky for the great article on the older variant, saved me lots of RE time.
— Michael Gillespie (@demonslay335) August 20, 2021
After downloading the decryptor, simply run the program and browse to a ransom note. After selecting the ransom, press the Start button and the decryption key will be detected.
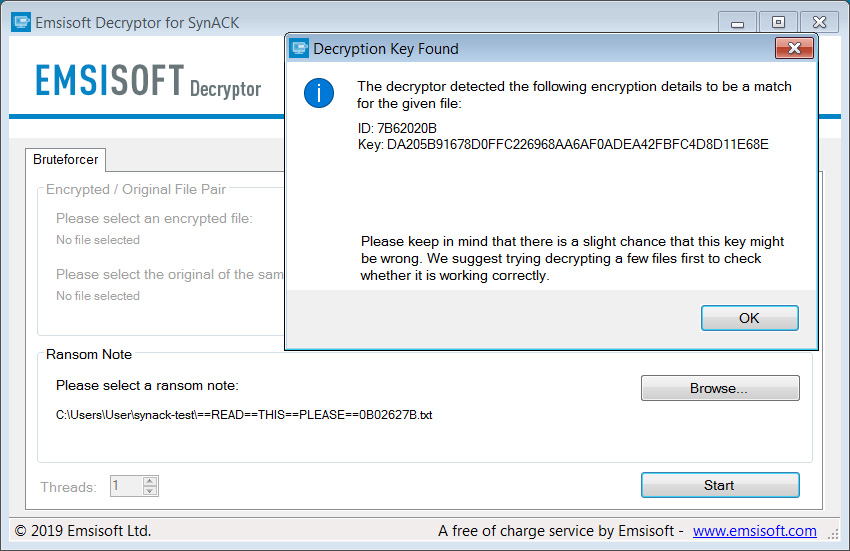
After pressing the OK button, the decryptor will load your decryption key, and you can now begin decrypting files.
As you can see from the image below, we could decrypt a test file using the key extracted from the bundled ransom note.
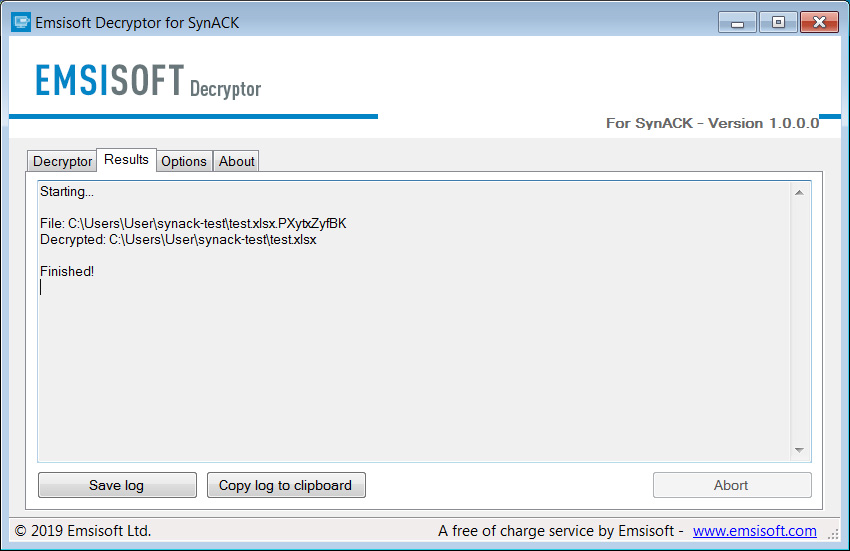
You can delete the leftover encrypted files after you have decrypted your files and determined that they are opening correctly.
For those who need help using the decryptor, please read this page first, and if that does not help, feel free to ask in our forums for further assistance.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now