
Several ransomware strains have been linked to APT38, a North Korean-sponsored hacking group known for its focus on targeting and stealing funds from financial institutions worldwide.
They're also known for deploying destructive malware on their victims' networks during the last stage of their attacks, likely to destroy any traces of their activity.
Christiaan Beek, a lead threat researcher at cybersecurity firm Trellix, said that the group's operators (part of Unit 180 of North Korea's cyber-army Bureau 121) have also used the Beaf, PXJ, ZZZZ, and ChiChi ransomware families to extort some of their victims.
The links to APT38 were found while analyzing code and artifact similarity with VHD ransomware which, just like TFlower ransomware, was linked to the North Korean Lazarus APT group.
Kaspersky and Sygnia researchers made the connection after seeing the two strains being deployed on victims' networks via the cross-platform MATA malware framework, a malicious tool exclusively used by Lazarus operators, according to Kaspersky.
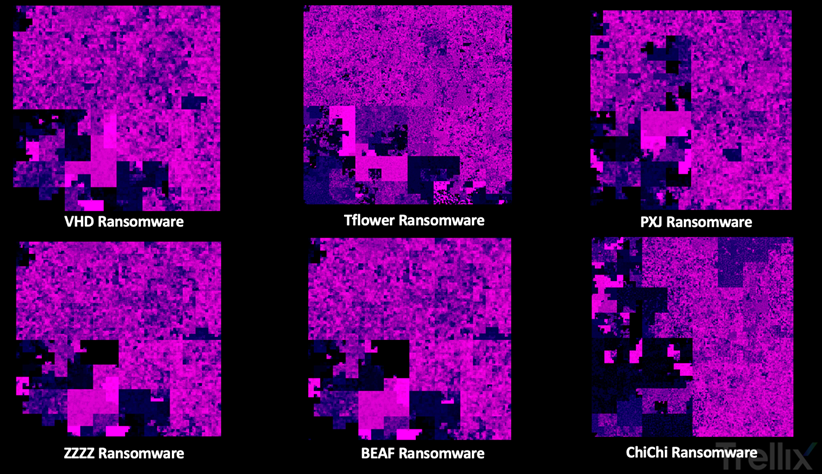
Beek revealed on Wednesday that — based on visualizing the code using Hilbert curve mapping — PXJ, Beaf, and ZZZZ share a notable amount of source code and functionality with VHD and TFlower ransomware, with Beaf and ZZZZ being almost exact clones of each other.
"You don't have to be a malware specialist to immediately recognize that the ZZZ and BEAF Ransomware pictures are almost identical," the Trellix researcher said.
"It also becomes apparent that both Tflower and ChiChi are vastly different when compared to VHD."
While ChiChi's codebase has little to no common points, Beek was able to find that the Semenov[.]akkim@protonmail[.]com email address was used by both ChiChi and ZZZZ in their ransom notes.
Attacks using these ransomware families have only targeted entities in the Asia-Pacific (APAC), making it harder to find the victims' identities since there were no negotiation chats or leak sites to investigate.
Trellix also attempted to discover additional links by analyzing the cryptocurrency transfers behind ransom payments but found no overlap in the crypto wallets used to collect ransoms.
However, they discovered that the North Korean hackers were only able to collect small amounts of crypto assets (for instance, a 2.2 BTC transfer in mid-2020, worth $20,000 at the time).
"We suspect the ransomware families [..] are part of more organized attacks," Beek added.
"Based on our research, combined intelligence, and observations of the smaller targeted ransomware attacks, Trellix attributes them to DPRK affiliated hackers with high confidence."



Comments
itjohan - 1 year ago
about North Korea.. I have been there, there is no chance they have these sofisticated hacking abilities.. I don't buy it.