
The "external sender" warnings shown to email recipients by clients like Microsoft Outlook can be hidden by the sender, as demonstrated by a researcher.
Turns out, all it takes for attackers to alter the "external sender" warning, or remove it altogether from emails is just a few lines of HTML and CSS code.
This is problematic as phishing actors and scammers can simply include some HTML and CSS code in their outgoing emails to tamper with the wording of the warning message or to make it disappear altogether.
Senders can easily hide "external sender" warnings
Email security products such as enterprise email gateways are often configured to display the "external sender" warning to a recipient when an email arrives from outside of the organization.
IT administrators enforce displaying such warnings to safeguard users against phishing and scam emails arriving from untrusted sources.
However, this week a researcher has shown a rather simple way that email senders can use to circumvent this protection applied by email security products.
By appending just a few lines of HTML and CSS code, researcher Louis Dion-Marcil showed how an external sender could hide the very warning from an email message.
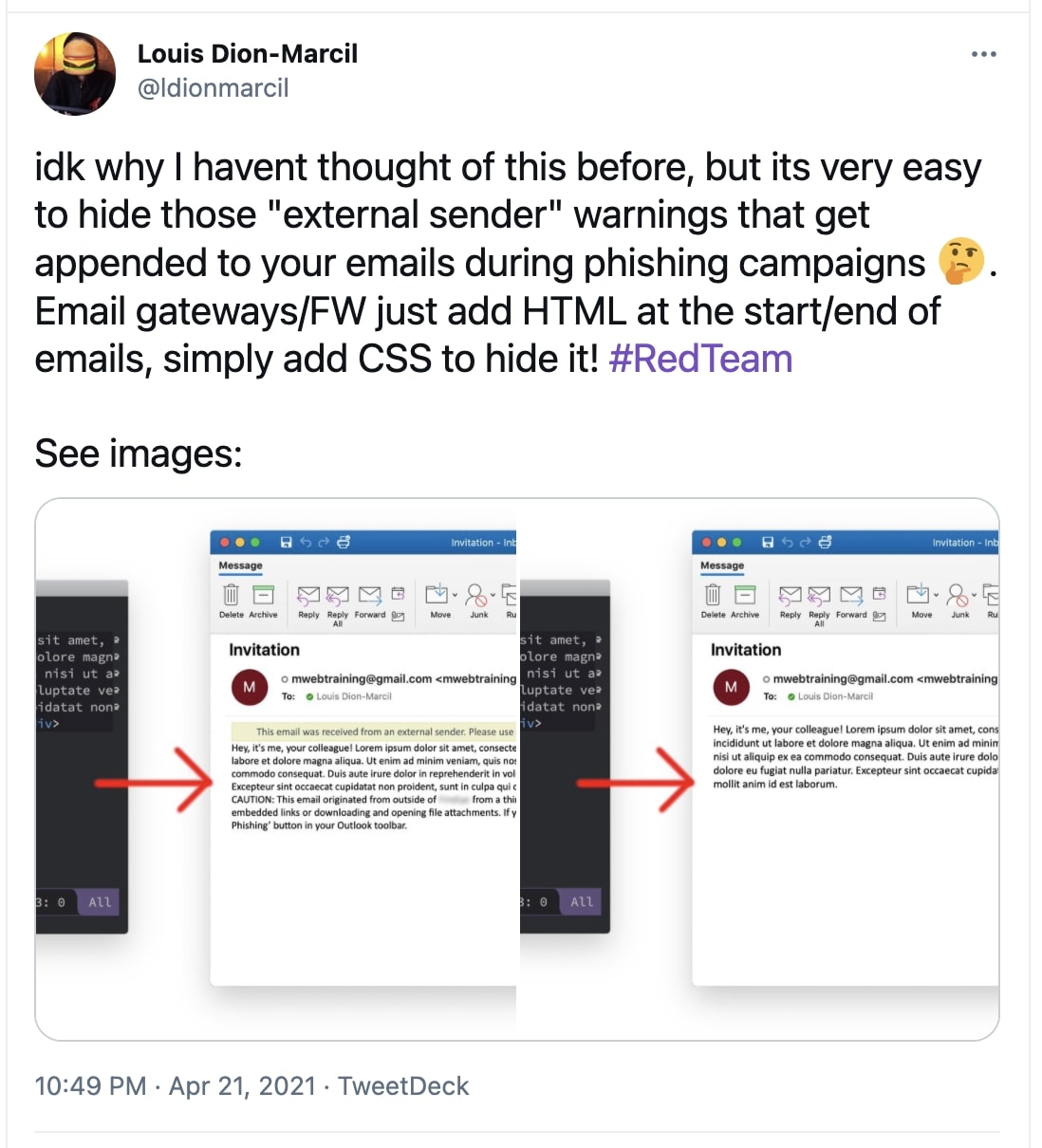
Source: Twitter
This happens because email security products and gateways that are intercepting and scanning incoming emails for suspicious content are simply injecting the "external sender" warning as an HTML/CSS code snippet in the email body itself, as opposed to the UI of the native email client displaying the message.
As such, an attacker-crafted email that contains CSS instructions to override the warning snippet's CSS code (display rules) can make the warning disappear altogether:
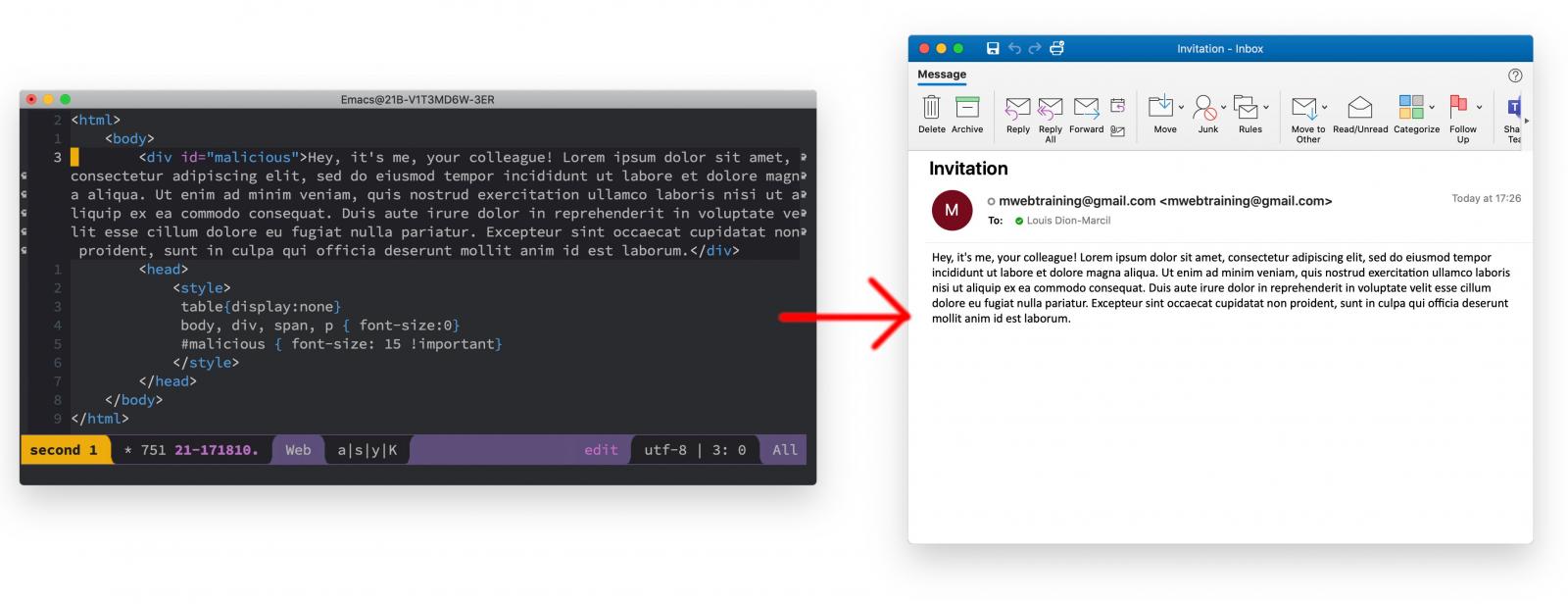
Source: Louis Dion-Marcil
Another researcher who alluded to also being aware of this behavior from the past implied an attacker could also exploit this flaw to alter the warning message:
"You could even fake HTML and CSS to [sic] instead of hiding it, indicating the content was scanned and deemed safe," said Jean Maes in the same thread.
Dion-Marcil has shared some insights with BleepingComputer on this behavior:
The researcher says that this is not a bug in any email client app per se, and is client-agnostic.
"It's not really a client bug, so it's client agnostic. nothing to do with Outlook really. I just happened to take a screenshot in Outlook, but [this] would work in Gmail, Thunderbird, etc."
"It's a limitation of HTML emails. If the warning is added to the HTML body, and the attacker obviously controls the HTML body, then they can add CSS rules to hide those elements."
"It is impossible to fix, other than moving to a non-HTML-based warning label," Dion-Marcil told BleepingComputer in an email interview.
Microsoft Exchange native 'external' email tags: a potential solution
Last month, Microsoft Exchange announced the addition of an upcoming "external" email tagging feature, as reported by BleepingComputer.
If IT administrators enable this feature on their organization's Exchange server, emails received from external sources, when parsed by native clients like Microsoft Outlook, will carry the "external" tags displayed within the native email client app's UI, as opposed to the email body.
As an example, screenshots shared by Microsoft show external emails received in Microsoft Outlook and Outlook mobile apps showing the "External" tag in the native email client's UI:
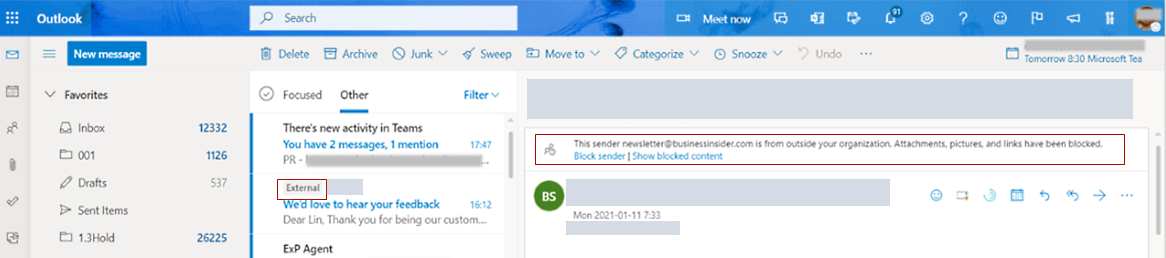
Source: Microsoft
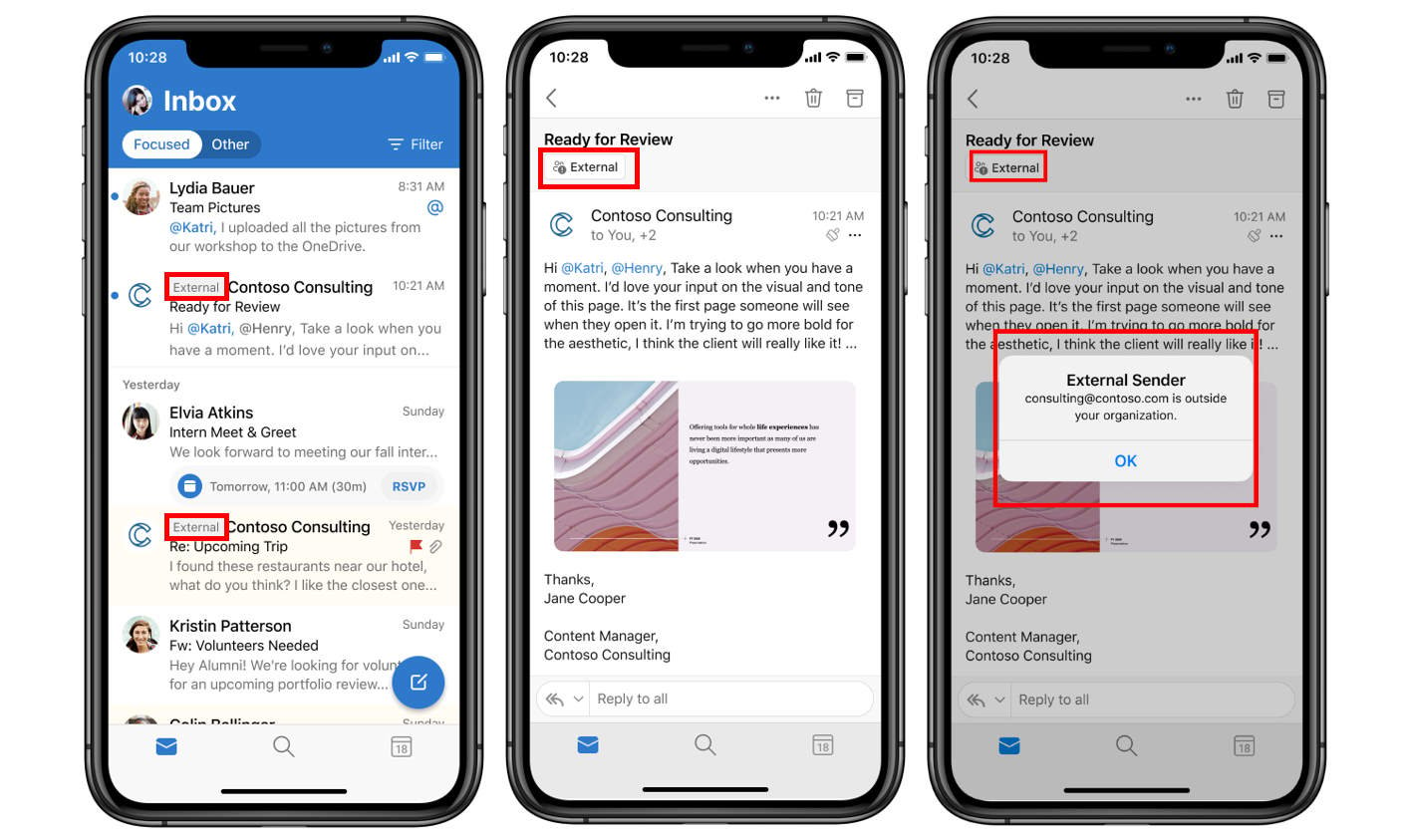
Source: Microsoft
Once the "external" email tagging feature rolls out to different Office 365 environments, however, it will be disabled by default.
As such, IT administrators interested in enabling this feature will need to use the Get-ExternalInOutlook and Set-ExternalInOutlook PowerShell cmdlets to view and modify external sender identification configuration in supported Outlook versions.
"If you enable the cmdlet, within 24-48 hours, your users will start seeing a warning tag in email messages received from external sources (outside of your organization)," says Microsoft.
"In Outlook mobile, by tapping on the External tag at the top of the message, the user will see the email address of the sender."
Regardless of whether an email contains the "external sender" warning, or on the contrary, touts itself to be "safe," users should be careful prior to opening any links or attachments in the emails they receive.
Update 10:52 AM: Added quotes received from Dion-Marcil.



Comments
jfftck - 3 years ago
Maybe Microsoft should upgrade the rendering engine in Office to a Chromium base as well and use web components to make it have isolated CSS that an injection like this less likely to be possible. Also, email could finally use modern CSS for styling with fallbacks since this is the only email client that has really been holding back the progress.
thorlancaster32 - 3 years ago
Couldn't the filtering gateway just randomize the CSS class name and location? Kind of like how Facebook prevents adblock.
You'd probably need JS to defeat this and there's no JS in emails.
Lemahtor - 3 years ago
Just setting the display explicitly or any other attributes you do not want changed in your banner will correct the issue. Yes html has default values so you do not have to define everything. You can also change the default values like the example above in the header style section. However, you can explicitly set the style on any attribute which will overide the default and header style settings. Add the below to the example provided and the table will display correctly.
<font size="12">
<table style=display:table;>
<tr>
My external banner
</tr>
</table>
</font>
Dominique1 - 3 years ago
I always stuck with TEXT emails, so a none issue for me. LOL!!!
N8an - 3 years ago
Can you please provide citation (link?) for the Microsoft quote "If you enable the cmdlet, within 24-48 hours, your users will start seeing a warning tag in email messages received from external sources (outside of your organization)". TIA.
AxSharma - 3 years ago
Have added it next to the quote: https://techcommunity.microsoft.com/t5/exchange-team-blog/native-external-sender-callouts-on-email-in-outlook/ba-p/2250098
The quote was taken from an earlier BleepingComputer article (perhaps sent to the reporter directly) which is already linked as well, at the beginning of the second section.