
While ransomware attacks have slowed during Russia's invasion of Ukraine and the subsequent sanctions, the malware threat continues to affect organizations worldwide.
This can be seen with Costa Rica declaring a national emergency after suffering a massive IT systems outage caused by a Conti Ransomware attack in April.
These outages are impacting public services, including requiring people to pay taxes at banks rather than online.
This declaration comes soon after the US government offered a $15 million reward for the location and identification of Conti ransomware members.
Secureworks also analyzed the new REvil ransomware samples, confirming previous reports that the ransomware gang has returned. With the threat actors having both the REvil source code and Tor private keys, it is clear that the operation has returned in some manner.
Other news this week includes a technical analysis of Black Basta with the Conti gang denying they are involved in the new operation.
Contributors and those who provided new ransomware information and stories this week include: @jorntvdw, @Ionut_Ilascu, @Seifreed, @billtoulas, @PolarToffee, @VK_Intel, @fwosar, @malwareforme, @malwrhunterteam, @DanielGallagher, @demonslay335, @BleepinComputer, @serghei, @LawrenceAbrams, @struppigel, @FourOctets, @TrendMicro, @kaspersky, @Secureworks, @BrettCallow, @bofheaded, @pcrisk, @ValeryMarchive, @kevincollier, @andrewselsky, @Amigo_A_, and @petrovic082.
May 7th 2022
US offers $15 million reward for info on Conti ransomware gang
The US Department of State is offering up to $15 million for information that helps identify and locate leadership and co-conspirators of the infamous Conti ransomware gang.
New Kekpop ransomware
Petrovic found a new ransomware that appends the .kekpop extension and drops a ransom note named ReadMe.html.
May 9th 2022
Costa Rica declares national emergency after Conti ransomware attacks
The Costa Rican President Rodrigo Chaves has declared a national emergency following cyber attacks from Conti ransomware group on multiple government bodies.
REvil Development Adds Confidence About GOLD SOUTHFIELD Reemergence
Secureworks® Counter Threat Unit™ (CTU) researchers analyzed REvil ransomware samples that were uploaded to the VirusTotal analysis service after the GOLD SOUTHFIELD threat group's infrastructure resumed activity in April 2022. The infrastructure had been shuttered since October 2021. Analysis of these samples indicates that the developer has access to REvil's source code, reinforcing the likelihood that the threat group has reemerged. The identification of multiple samples containing different modifications and the lack of an official new version indicate that REvil is under active development.
Examining the Black Basta Ransomware’s Infection Routine
Black Basta, a new ransomware gang, has swiftly risen to prominence in recent weeks after it caused massive breaches to organizations in a short span of time.
Lincoln College to close after 157 years due ransomware attack
Lincoln College, a liberal-arts school from rural Illinois, says it will close its doors later this month, 157 years since its founding and following a brutal hit on its finances from the COVID-19 pandemic and a recent ransomware attack.
New TitanCrypt ransomware
PCrisk found a new variant of Jcrypt called TitanCrypt that appends the .titancrypt and drops a ransom note named ___RECOVER__FILES__.titancrypt.txt.
New 'Japan' ransomware variant
PCrisk found a ransomware that is appending the .japan extension to encrypted files and drops a ransom note named how to decrypt.txt.
May 10th 2022
New Xorist variant
PCrisk found a new Xoris variant appending the .WanaCray2023+ and dropping a ransom note named HOW TO DECRYPT FILES.txt.
Hackers hit web hosting provider linked to Oregon elections
A week before Oregon’s primary election, the secretary of state’s office is moving to protect the integrity of its online system where campaign finance records are published after a web hosting provider was hit by a ransomware attack.
May 11th 2022
New ransomware trends in 2022
Ahead of the Anti-Ransomware Day, we summarized the tendencies that characterize ransomware landscape in 2022. This year, ransomware is no less active than before: cybercriminals continue to threaten nationwide retailers and enterprises, old variants of malware return while the new ones develop. Watching and assessing these tendencies not only provides us with threat intelligence to fight cybercrime today, but also helps us deduce what trends may see in the months to come and prepare for them better.
Conti denies involvement in new Black Basta gang
Conti continues to threaten the government of Peru and also states that they are not associated with the new Black Basta operation.

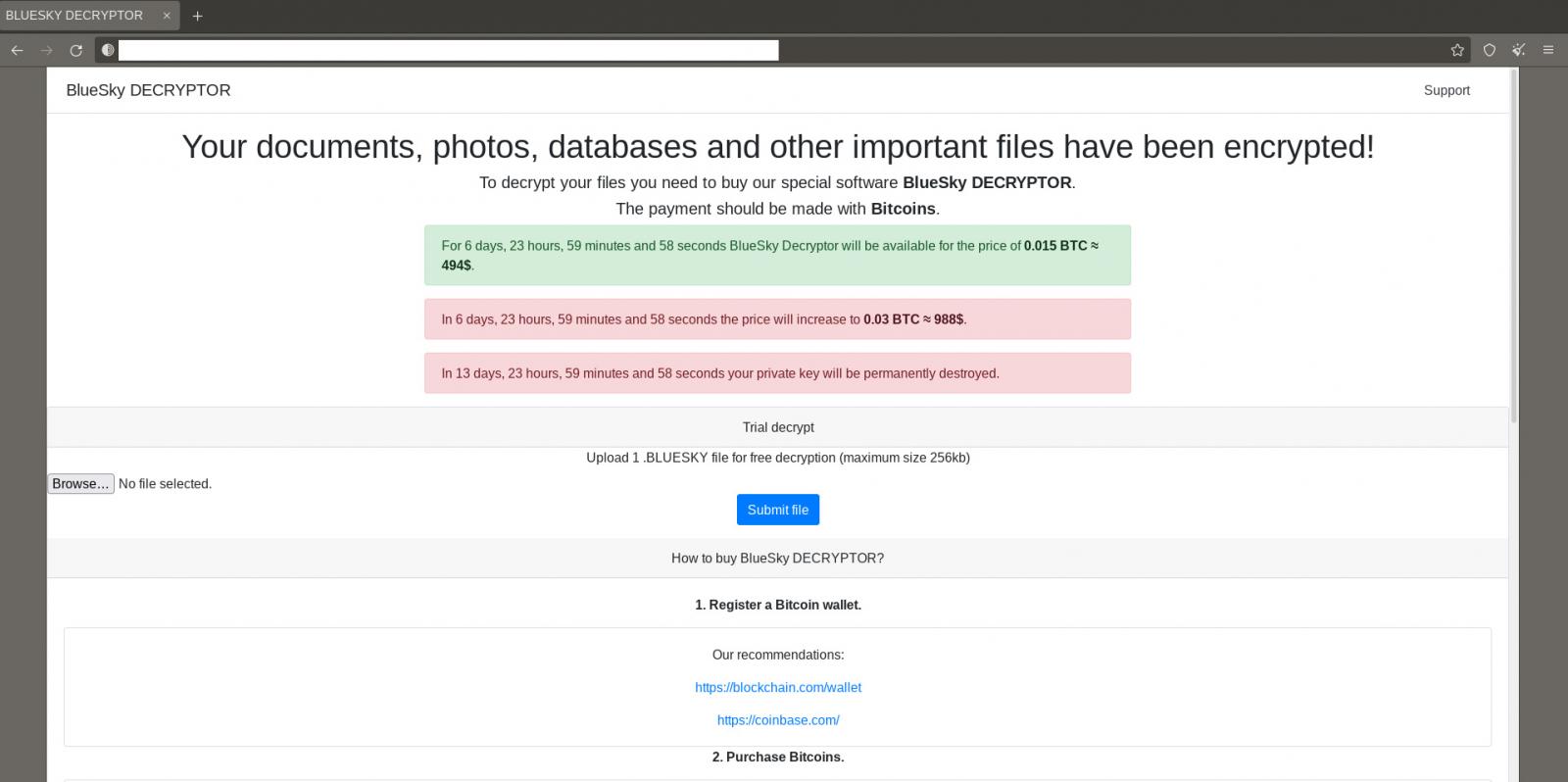
New BlueSky ransomware
Dreamer discovered a new ransomware operation named BlueSky.
May 12th 2022
Ransomware: Has Moscow given free rein to its cybercriminals in Latin America?
Links between Conti and the FSB have come to light. The cybercriminal SME has been very aggressive against Costa Rica and Peru, while Latin America appears to be particularly affected. Fifteen countries in the region have spoken out against the invasion of Ukraine.
New STOP ransomware variants
PCrisk found new STOP ransomware variants that append the .kruu, .ifla, and .byya extensions.
May 13th 2022
New STOP ransomware variant
PCrisk found a new STOP ransomware variant that appends the .errz extension.
New TxLocker ransomware
Amigo-A found a new TxLocker ransomware that appends the .txlck extension and drops a ransom note named f1x_instructions.txt.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now