
Threat actors actively exploit a critical authentication bypass vulnerability impacting home routers with Arcadyan firmware to take them over and deploy Mirai botnet malicious payloads.
The vulnerability tracked as CVE-2021-20090 is a critical path traversal vulnerability (rated 9.9/10) in the web interfaces of routers with Arcadyan firmware that could allow unauthenticated remote attackers to bypass authentication.
The ongoing attacks were discovered by Juniper Threat Labs researchers while monitoring the activity of a threat actor known for targeting network and IoT devices since February.
Millions of routers likely exposed to attacks
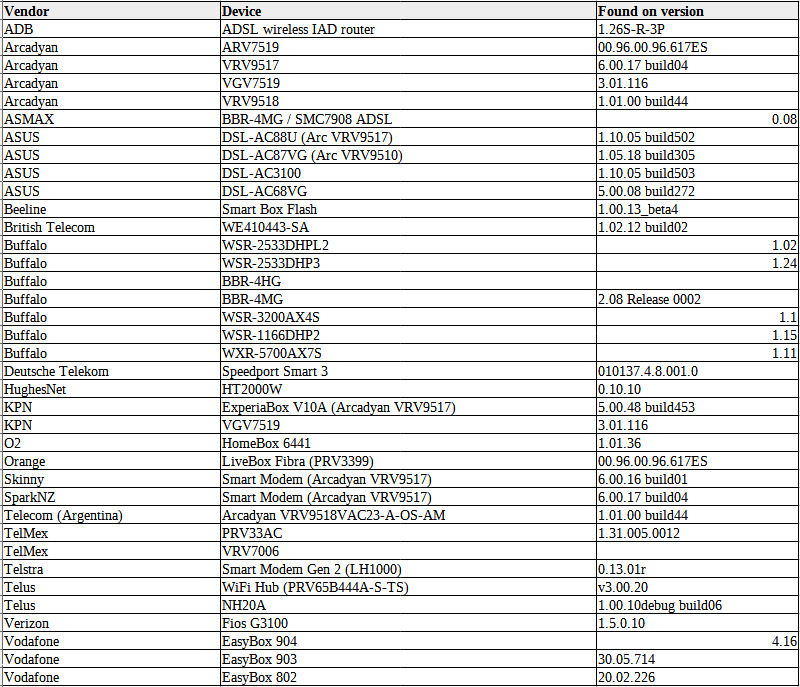
Vulnerable devices include dozens of router models from multiple vendors and ISPs, including Asus, British Telecom, Deutsche Telekom, Orange, O2 (Telefonica), Verizon, Vodafone, Telstra, and Telus.
Based on the number of router models and the long list of vendors impacted by this bug, the total number of devices exposed to attacks likely reaches millions of routers.
The security flaw was discovered by Tenable, which published a security advisory on April 26 and added proof of concept exploit code on Tuesday, August 3.
"This vulnerability in Arcadyan’s firmware has existed for at least 10 years and has therefore found its way through the supply chain into at least 20 models across 17 different vendors, and that is touched on in a whitepaper Tenable has released," explained Evan Grant, Tenable Staff Research Engineer, on Tuesday.
A little video demo from the Buffalo writeup ( https://t.co/ySft5EP299 ) : pic.twitter.com/1ulDi0CyXZ
— evan grant (@stargravy) August 3, 2021
A list of all known affected devices and vendors (including vulnerable firmware versions) is embedded below.
Attacks start two days after PoC exploit release
Since Thursday, Juniper Threat Labs "identified some attack patterns that attempt to exploit this vulnerability in the wild coming from an IP address located in Wuhan, Hubei province, China."
The threat actors behind this ongoing exploitation activity use malicious tools to deploy a Mirai botnet variant, similar to those used in a Mirai campaign targeting IoT and network security devices, discovered by Unit 42 researchers in March.
"The similarity could indicate that the same threat actor is behind this new attack and attempting to upgrade their infiltration arsenal with yet another freshly disclosed vulnerability," Juniper Threat Labs said.
The researchers first spotted the threat actors' activity on February 18. Since then, they've continuously added new exploits to their arsenal, the one targeting CVE-2021-20090 being the last included earlier this week, with more likely to come.
"Given that most people may not even be aware of the security risk and won’t be upgrading their device anytime soon, this attack tactic can be very successful, cheap and easy to carry out."
Indicators of compromise (IOCs), including IP addresses used to launch the attacks and sample hashes, are available at the end of Juniper Threat Labs' report.
Update: Orange told Le Parisien that the vulnerability poses no risk to their French customers "since the Arcadyan software is not used in the LiveBox Fibra currently being used in France."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now