
Security analysts have found security issues in the payment system present on Xiaomi smartphones that rely on MediaTek chips providing the trusted execution environment (TEE) that is responsible for signing transactions.
Attackers could exploit the weaknesses to sign fake payment packages using a third-party unprivileged application.
The implications of such an attack would be to make the payment service unavailable or to sign transactions from the user’s mobile wallet to the threat actor’s account.
Considering how common mobile payments and Xiaomi phones are, especially in Asian markets, the money pool hackers could tap into is estimated to be in the billions of U.S. dollars.
Trusted environment in Xiaomi
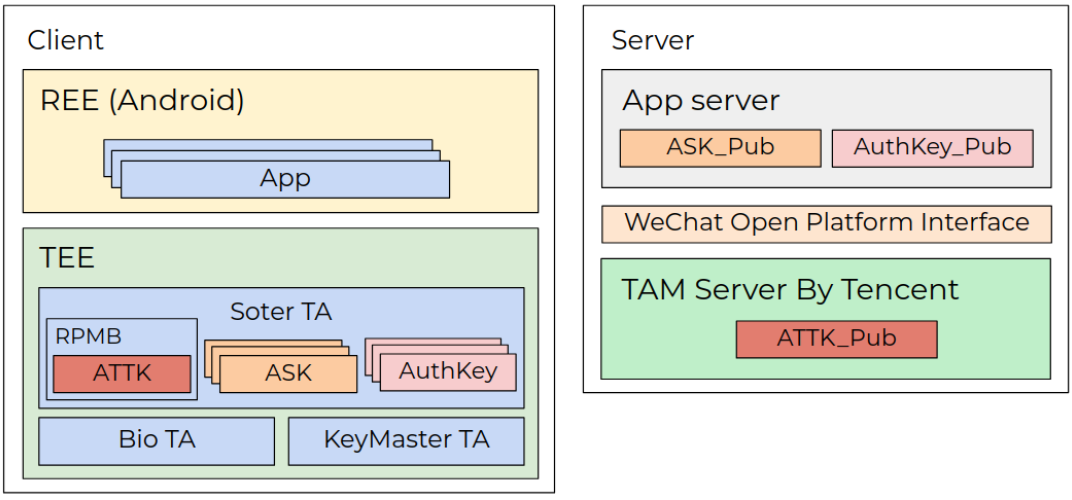
Xiaomi phones that run on a MediaTek chip use the “Kinibi” TEE architecture, which creates a separate virtual enclave for storing security keys required for signing transactions.
This space is designed for running trusted apps like Xiaomi’s “thhadmin,” which is responsible for security management, including the ‘Tencent Soter’ embedded mobile payment framework that provides an API for third-party apps to integrate payment capabilities.
Apps like WeChat Pay and Alipay, which collectively have over a billion users, rely on the ‘Tencent Soter’ API to verify payment packages securely and enable financial transactions.
Attacking Xiaomi’s trusted space
Security researchers at Check Point have found a flaw in the trusted app format that Xiaomi uses, namely the lack of version control. This opens the door for a downgrade attack, meaning that a threat actor could replace a newer, more secure app with an older, vulnerable version.
The researchers were able to use another vulnerability (CVE-2020-14125) in the Tencent Soter trusted app that allows an attacker to extract private keys and sign fake payment packages in the context of an unprivileged user.
They bypassed Xiaomi and MediaTek security patches by overwriting the ‘thhadmin’ app on MIUI 12.5.6.0 with that from MIUI 10.4.1.0, opening up a host of exploitation possibilities.
The communication link is established by using the SoterService as a proxy, after invoking the initSigh function in the Soter app using the following Java code.
.png)
How to stay safe
For users of MediaTek-based Xiaomi phones, it is important to apply June Android 2022 security updates, which addresses the CVE-2020-14125 vulnerability.
The Soter key leak flaw is a third-party issue, and Xiaomi could only confirm that the vendor is working on a fix, so a patch should become available in the future.
If you can’t afford to disable mobile payments altogether, try to minimize the number of installed apps on your device, keep your OS up to date, and use a mobile security suite that can detect and stop suspicious actions.



Comments
fromFirefoxToVivaldi - 1 year ago
>and use a mobile security suite that can detect and stop suspicious actions.
Any recommendations? IIRC many android security apps only scan for known hashes.
EndangeredPootisBird - 1 year ago
Theres Trustd (Formerly Traced) Mobile Security
https://traced.app/app/android/
beepboopboopbleeep - 1 year ago
Does that mean if you are running LineageOS you are not affected by this problem because you are not running vulnerable `thhadmin,`? Yet MediaTek chip use the “Kinibi” TEE architecture may still be vulnerable. Can someone elaborate?