
Network monitoring company LogicMonitor confirmed today that some users of its SaaS platform have fallen victim to cyberattacks.
The company says that the hacking campaign has hit what it describes as a "small number" of users and is working with those affected to mitigate the attacks' impact.
"We are currently addressing a security incident that has affected a small number of our customers," a spokesperson told BleepingComputer.
"We are in direct communication and working closely with those customers to take appropriate measures to mitigate impact."
While LogicMonitor did not confirm that ransomware attacks hit its affected customers, anonymous sources familiar with the incidents told BleepingComputer that the threat actors hacked customer accounts and "were able to create local accounts and deploy ransomware."
The same sources said the ransomware was deployed using the platform's on-premise LogicMonitor Collector sensors, which monitor user infrastructure but also have scripting functions.
This was allegedly done by the threat actors deploying scripts from the cloud-based platform that were pushed down to the on-premise Collectors and executed locally.
BleepingComputer was told the attacks targeting LogicMonitor's customers happened last week.
If you have any information on this attack or other attacks, you can contact us confidentially via Signal at 646-961-3731.
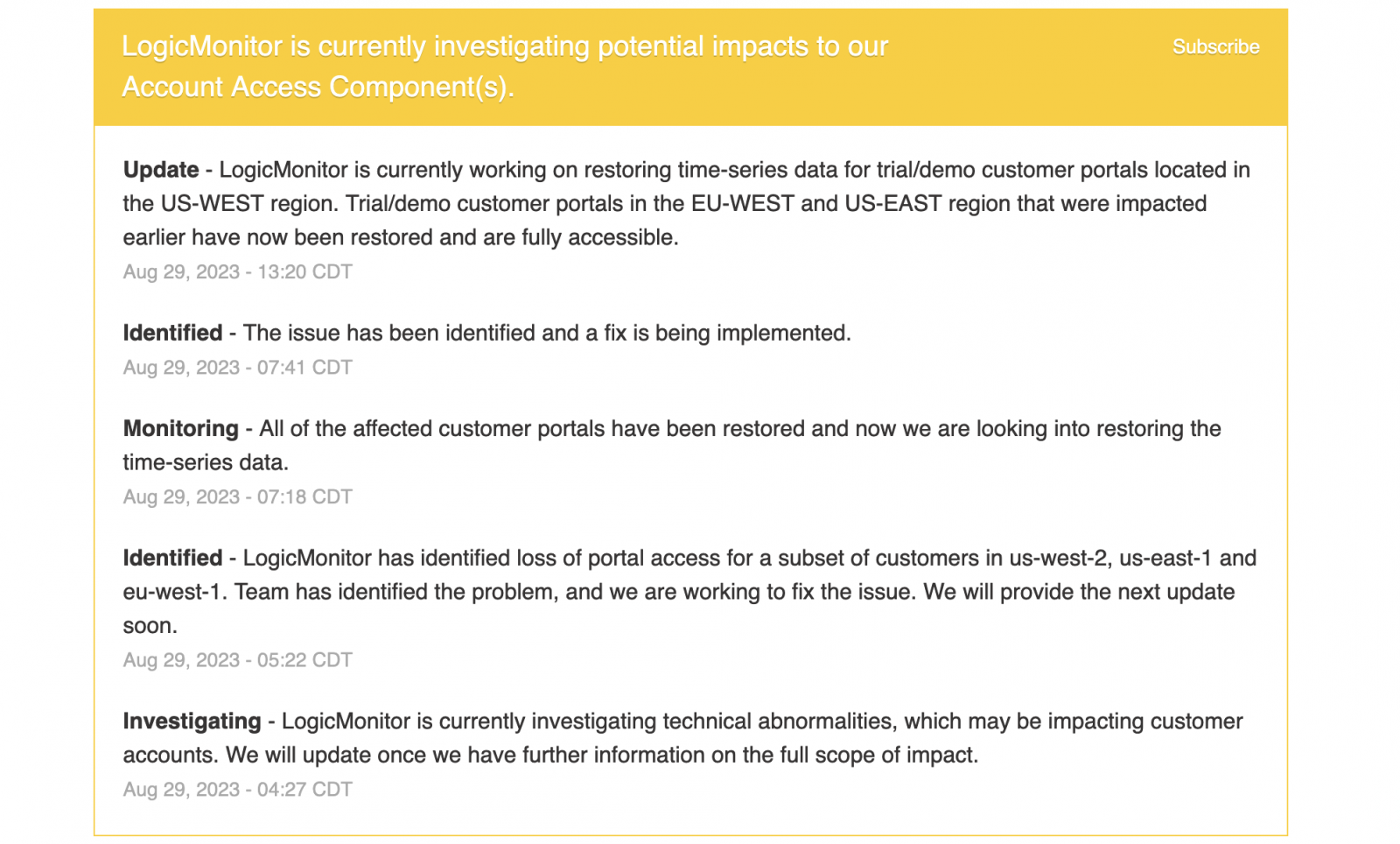
Company investigating account access issues
Two days ago, the company said on its status page that it was investigating "technical abnormalities" impacting customer accounts.
"LogicMonitor has identified loss of portal access for a subset of customers in us-west-2, us-east-1 and eu-west-1. Team has identified the problem, and we are working to fix the issue," the company said in an update.
"LogicMonitor is currently working on restoring time-series data for trial/demo customer portals located in the US-WEST region. Trial/demo customer portals in the EU-WEST and US-EAST region that were impacted earlier have now been restored and are fully accessible."
In a separate incident report, LogicMonitor said 17 hours ago that the incident had been resolved.
Customers hacked because of weak default passwords
Another anonymous source told TechCrunch that the affected customers' accounts were hacked using default weak passwords assigned by LogicMonitor to new users.
These passwords were also automatically assigned to all other users created across the organizations until they were changed.
"LogicMonitor had reached out to us proactively with a possible username/password breach for a few of their customers via a call, which could lead to systems that are being monitored by LogicMonitor to be compromised with a ransomware attack and henceforth this proactive reach out," one of the company's customers also said.
A LogicMonitor spokesperson declined to provide additional information in response to inquiries from BleepingComputer.
These queries sought additional details regarding the number of customers impacted and whether the attackers successfully infiltrated the company's systems.
Moreover, customers interviewed by BleepingComputer also said that LogicMonitor was sharing minimal information with users.
LogicMonitor says its network monitoring platform is used by more than 25,000 users.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now