
Researchers at the University of Hamburg in Germany have conducted a field experiment capturing hundreds of thousands of passersby's WiFi connection probe requests to determine the type of data transmitted without the device owners realizing it.
WiFi probing is a standard process, part of the bilateral communication required between a smartphone and an access point (modem/router) to establish a connection.
By default, and for reasons of usability, most smartphones search for available WiFi networks all the time, and connect to them if trusted.
Many stores already use WiFi probing to track their customers' position and movement. Because this tracking only uses anonymized MAC addresses in the probe, it is considered GDPR compliant.
The researchers decided to analyze those probes to see what else they might contain, and in 23.2% of the cases, they found that the requests broadcast SSIDs of networks those devices connected to in the past.
Experiment findings
The experiment occurred in November 2021 in a busy pedestrian zone in the center of a German city. The team used six antennae to capture probes in various channels and spectrums.
They recorded all broadcasted WiFi connection problems for three hours, capturing a total of 252,242 probe requests, 46.4% in the 2.4GHz spectrum and 53.6% in 5GHz.
In just three hours, the researchers had 58,489 SSIDs from random passersby, which, in many cases, contained numeric strings with 16 or more digits that were likely "initial passwords" of popular German home routers from FritzBox or Telekom.
"Leaking passwords in SSIDs is especially critical if, along with the password, the device also broadcasts the true SSID either correctly or with a mistype that can be used to infer the true SSID," explain the researchers in the technical paper.
"The assumption that the sniffed passwords correspond to SSIDs that were also transmitted could additionally be verified by setting up fake access points on the fly using the potential credentials we observed."
In other subsets of the captured SSIDs, the researchers found strings corresponding to store WiFi networks, 106 distinct names, three email addresses, and 92 holiday homes or accommodations previously added as trusty networks.
Some of these sensitive strings were broadcasted tens, hundreds, and in some cases, even thousands of times during the three hours of recording through repeated bursts of probing.
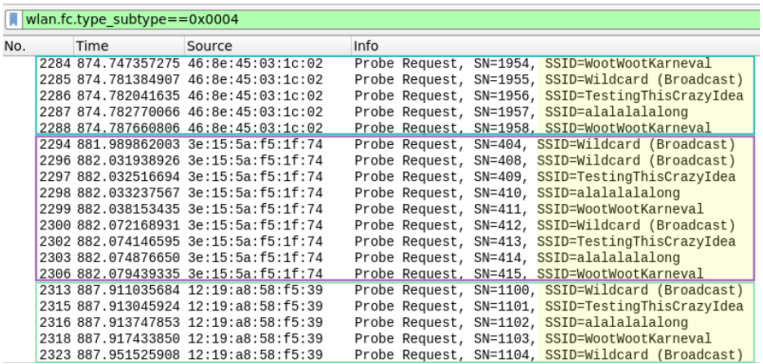
Tracking implications
Leaving aside the data exposure and the scenario of setting up malicious hotspots and accepting connections from nearby devices, the main implication here is persistent tracking.
The critical aspect on that front is MAC addresses randomization, which can act as a defense against tracking attempts.
While it has come a long way in both Android and iOS to make device tracking harder, although not impossible.
Newer OS versions feature more randomization and less information in the probe requests, but when combined with dataset parameters like signal strength, sequence number, network capabilities, etc., fingerprinting individual devices might still be possible.
An overview of the privacy features of each OS version is given below. Note that market share percentages reflect November 2021 figures.
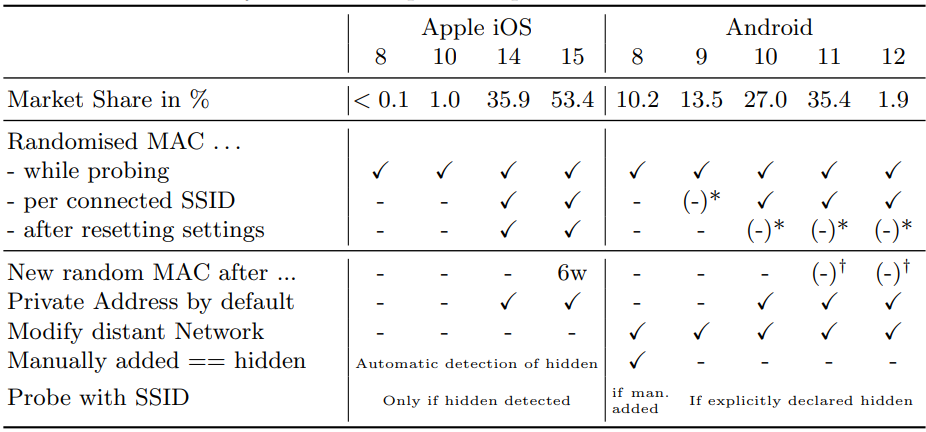
Clearly, the more recent the OS version, the stronger the privacy-protection features, but the availability of newer versions doesn't mean instant adoption.
At the time of the field experiment, Android 8 and older versions accounted for roughly one out of four Android smartphones. In iOS, the situation is better due to Apple's tighter software update policies and long-term support, but many still use older iPhone models.
Previous studies have also reflected the improvement from gradual upgrades to more secure operating systems. For example, in a 2014 study, 46.7% of recorded probe requests contained SSIDs, and in two others conducted in 2016, the percentage ranged between 29.9% and 36.4%.
How to bolster your privacy
The first and simplest thing a smartphone user can do is upgrade their OS and use a more recent and safer version that features more privacy protections.
Secondly, removing SSIDs you no longer use or need and which are unnecessarily broadcasted wherever you go would be a good idea.
Thirdly, Android and iOS offer a quick way to disable auto-join networks, rendering hotspot attacks impossible.
Finally, users can completely silence probe requests, which can be done via advanced network settings. This approach, however, has several practical drawbacks, such as slower connection establishment, inability to discover hidden networks, and higher battery consumption.


Comments
AgeOfMarcus - 1 year ago
Not only can you gather that sort of information, but combined with the community driven WiGLE map of networks, you can create a map of the locations each device has visited.
This has worrying implications for the future of stalking. Check wigle (dot) net, is your router's SSID mapped? You could be in danger.