
The Chicago Public Schools has suffered a massive data breach that exposed the data of almost 500,000 students and 60,000 employee after their vendor, Battelle for Kids, suffered a ransomware attack in December.
Ohio-based Battelle for Kids is a not-for-profit educational organization that analyzes student data shared by public school systems to design instructional models and evaluate teacher performance.
Battelle for Kid says they work with 267 school systems, and its programs have reached over 2.8 million students.
Massive data breach for Chicago Public Schools
Yesterday, the Chicago Public School (CPS) district disclosed that a December 1st ransomware attack on Battelle for Kids exposed the stored data of 495,448 students and 56,138 employees in its school system.
According to a CPS, the school system partners with Battelle for Kids to upload student course information and assessment data for teacher evaluations.
CPS says that the data stored on Battelle for Kids' servers was for school years 2015 through 2019 and exposed students' personal information and assessment scores.
"Specifically, an unauthorized party gained access to your child’s name, date of birth, gender, grade level, school, Chicago Public Schools student ID number, State Student ID number, information about the courses your student took, and scores from performance tasks used for teacher evaluations during school years 2015-2016, 2016-2017, 2017-2018 and/or 2018-2019," explains the CPS student data breach notification.
For staff, the threat actors potentially accessed their name, school, employee ID number, CPS email address, and Battelle for Kids username during school years 2015-2016, 2016-2017, 2017-2018 and/or 2018-2019.
CPS says that no Social Security Numbers, home addresses, health data, or financial information was exposed in the attack.
CPS is providing free credit monitoring, and identity theft protection to any students or staff members impacted. Instructions on how to access this free credit reporting can be found on the CPS data breach page created by the school system.
Over four months to disclose breach
In April, Ohio school districts began issuing data breach notifications warning students and staff that their data was exposed in the ransomware attack on Battelle for Kids.
Even though CPS' says their contract with Battelle for Kids requires immediate notification of a data breach, they first learned about the breach four months later, on April 26th, 2022.
However, it was not until May 11th that they first learned which specific students or staff had their data exposed.
"Our vendor, Battelle for Kids, informed us that the reason for the delayed notification to CPS was the length of time that it took for Batelle to verify the authenticity of the breach through an independent forensic analysis, and for law enforcement authorities to investigate the matter," explains CPS on their data breach page.
While it is not known what ransomware gang is behind this attack, all groups leave ransom notes behind on encrypted devices that include email addresses or links to ransom negotiation sites.
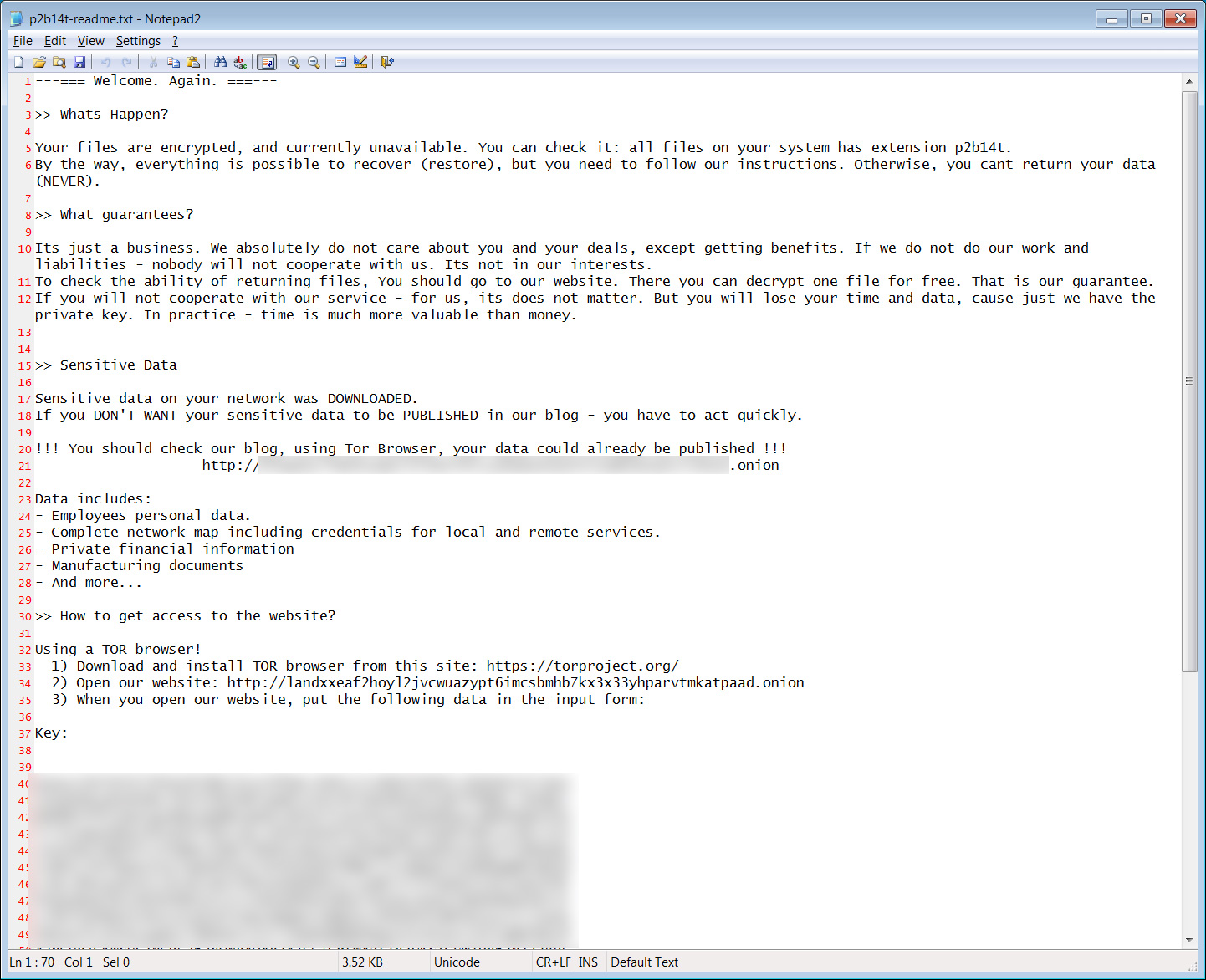
As part of the extortion process, ransomware gangs commonly provide proof that they stole data by sharing a list of all the stolen folders and sometimes sharing individual files as proof.
When a victim refuses to pay a ransom, the threat actors publicly disclose that they attacked the victim and begin leaking their stolen data.
There has been no public disclosure by a ransomware gang stating that they breached Battelle for Kids, possibly indicating that Battelle for Kids paid a ransom demand.
A similar but unrelated data breach was disclosed by the New York City Department of Education in March, where a vendor's cyber attack exposed the data of 820,000 students.
BleepingComputer has contacted Battelle for Kids with questions but has not heard back at this time.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now