An Unholy Union: Remote Access and Ransomware
Category
Awareness, Vulnerabilities
Risk Level
Back in June 2020, the Department of Homeland Security (DHS) issued an advisory that married together two of today’s major cybersecurity concerns: remote access technology and ransomware. While we talked about the possibility of this in another ACT post, DHS has now confirmed that they are seeing this unholy union occurring in the wild.
“When you say remote access technology....what do you mean?”
Generally speaking, this is any technology that lets you access your organization’s IT resources while you’re away from the office. During the COVID-19 pandemic for example, you may use a Virtual Private Network (VPN) to connect to your organization’s network as if you’re sitting in the office, or you might use Remote Desktop Protocol (RDP) to connect to your computer that’s now collecting dust on your office desk.
“Ah ok, yeah, we use one of those. What’s the problem?”
Remote access technology has been critical to keeping organization’s running during the COVID-19 pandemic. However some organization’s implementations of these technologies have left them vulnerable. For example, if your organization allows you to connect directly to your computer using RDP over the internet, then you’re essentially inviting a hacker right in through your front door to cause trouble.
Back in March, a group of security researchers noted that there were over 4.5 million instances of RDP that were open to the internet. Their goal in telling this story was to draw attention to it in hopes that organization’s would correct the issue. Unfortunately, many did not while even more appeared, and there are now over 4.7 million exposed RDP ports.
VPNs continue to be problematic as well. For example, if someone in your organization reuses their VPN password somewhere else, and there’s no multi-factor authentication setup, hackers could easily login to the VPN and have free rein over all of your organization’s information.
Once a hacker is on your computer or in your network, that’s when the problems start. They can steal information, edit documents, send emails that look like they’re from your boss, or even install ransomware.
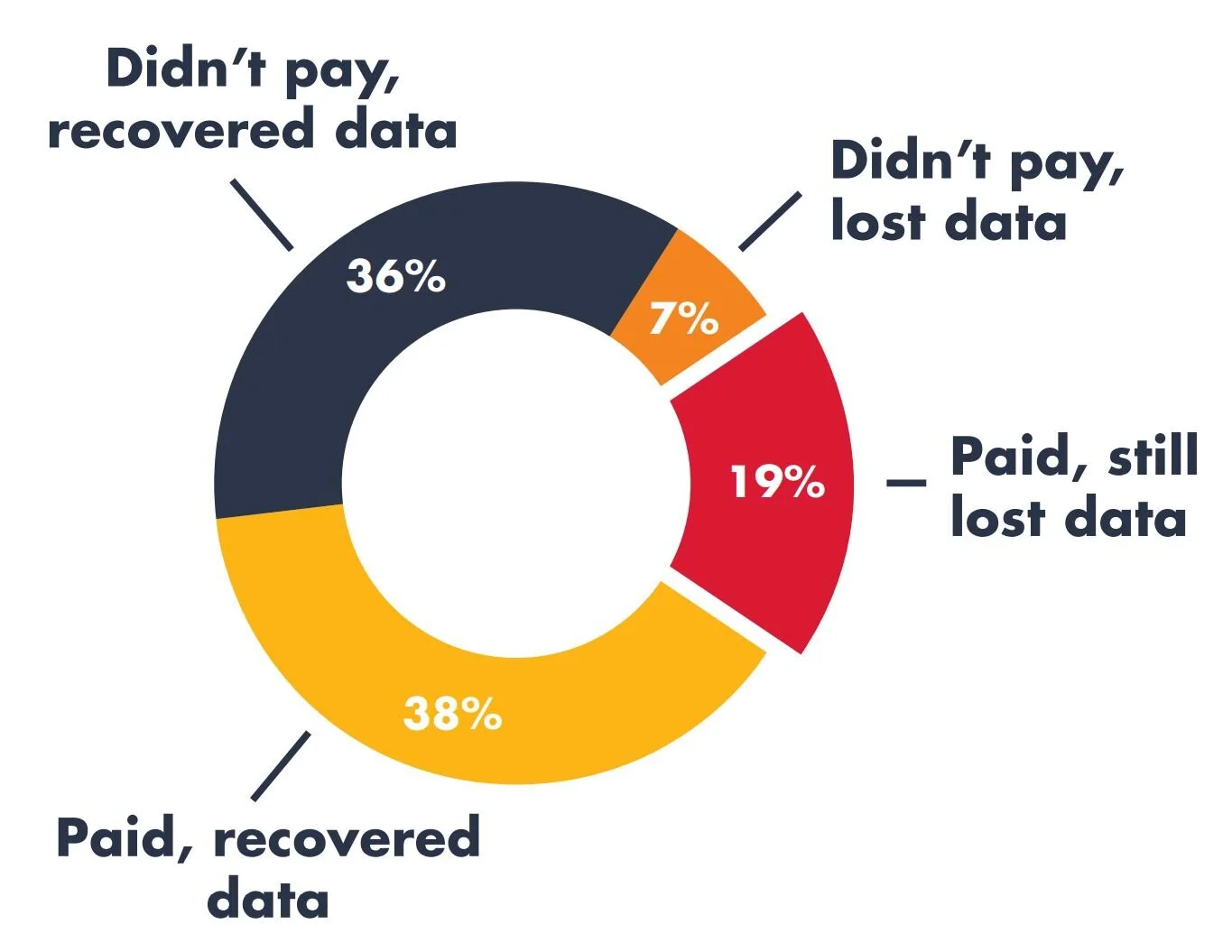
That last one is especially problematic. Not only does paying the ransom potentially cost thousands, but it likely stops your organization from being able to operate. That adds on even more expenses! Even worse, there’s no guarantee you’ll get your information back (see the graphic), and hackers may still steal your information to sell to other hackers, or even your competitors, for more money.
Source: CyberEdge 2020 Cyberthreat Defense Report
“Yikes! So what should we do?”
First don’t panic. There are simple steps you can take right now without spending a lot of, or any, money:
Securing RDP
Generally, using RDP is not recommended. VPN technology allows better security and more granularity in terms of access. However, if your organization is only able to use RDP, UC Berkeley has created a great guide on securing it. Their minimum recommendations include:
Use strong passwords
Restrict access using firewalls
Enable Network Level Authentication (NLA)
Limit users who can login using RDP
Set an account lockout policy
If you want to increase your security further:
Do not allow direct RDP access to clients or servers from off campus.
Use RDP Gateways (Best Option)
Change the listening port for Remote Desktop
Tunnel Remote Desktop connections through IPSec or SSH
Use existing management tools for RDP logging and configuration
Securing VPNs
VPN technology is the main remote access technology for a lot of organizations. However, not all implementations are created equal, and there are steps to make it more secure. Mike Chapple, a cybersecurity expert, wrote a handy guide for FedTech that covered three major tips. They included:
Regularly updating VPN hardware and software
Following best practices for VPN management. This would include items like:
Strong encryption and authentication
Limiting who has VPN access
Limiting what resources the VPN can access
IT admins should monitor VPN usage
He also notes the risks of split-tunnel vs full-tunnel VPNs. While a full-tunnel VPN is more secure because ALL of your computer’s internet traffic goes through the VPN, your organization’s internet connection may not be able to handle that much bandwidth. In consideration of this, some organization’s will route SOME traffic through the VPN (e.g. accessing a shared drive), and other traffic through the internet (e.g. going to www.hivesystems.io). This can dramatically increase the risk if not handled appropriately!
Preventing Ransomware
The chance of you being impacted by ransomware has increased dramatically over the past couple of years. The good news is that there are a number of ways to reduce your risk, and better yet, recover from it should you get infected. The Cybersecurity & Infrastructure Security Agency (CISA), a division of DHS, released this information guide on preventing and recovering from ransomware (in addition to who you should contact if you do get infected). Their recommendations to prevent ransomware include:
Backup your data, system images, and configurations, and keep the backups offline
Update and patch all of your IT devices
Make sure your security solutions are up to date
Review and exercise your incident response plan
Pay attention to ransomware events and apply lessons learned
“Ok - we’ll start working on those when we have a chance.”
Unfortunately, there’s no time to wait, as noted by the Tonya Ugoretz from the FBI:
.@FBI's Tonya Ugoretz says just now the Internet Crime Complaint Center already in ~the 1st/2nd week of June had as may complaints as they did in all of 2019. For coronavirus-related internet crime the FBI has received/reviewed at least 20,000 complaints, she says. https://t.co/ujWnugzRnC
— Shannon Vavra (@shanvav) June 24, 2020
So ACT today! If you’re unsure if you’re vulnerable, or want to know more about the best path forward for your organization, check out our Vulnerability Assessment. We’ll help you find out where you can improve your cybersecurity posture and give you actionable recommendations to do just that - together.




It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. How did we make this table? Want to download a copy? Read on!