Insights from CISA HPH Sector Risk and Vulnerability Assessment
Security Boulevard
JANUARY 1, 2024
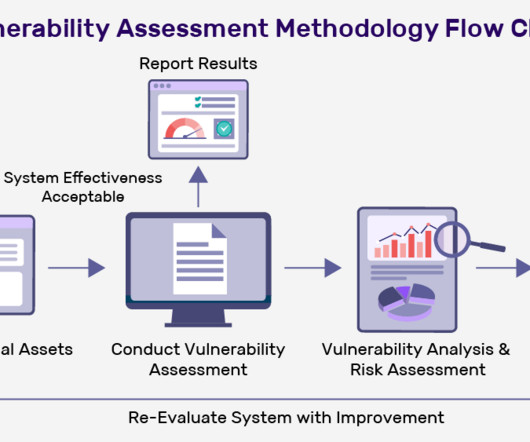
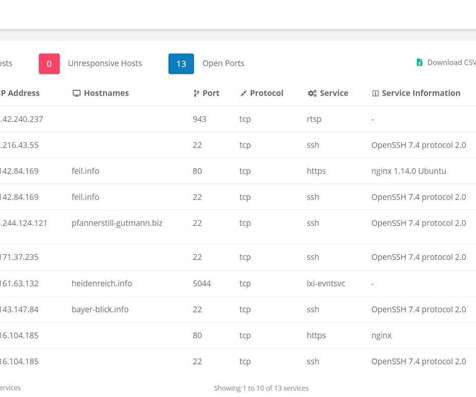
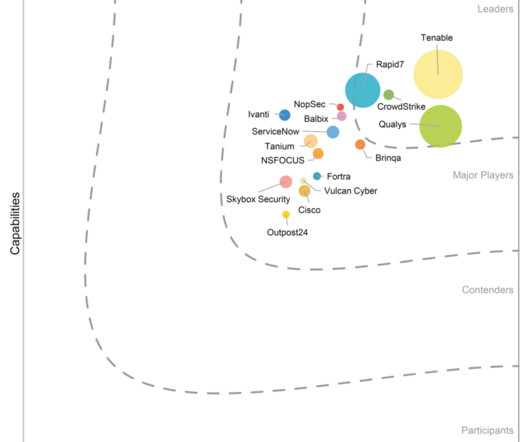
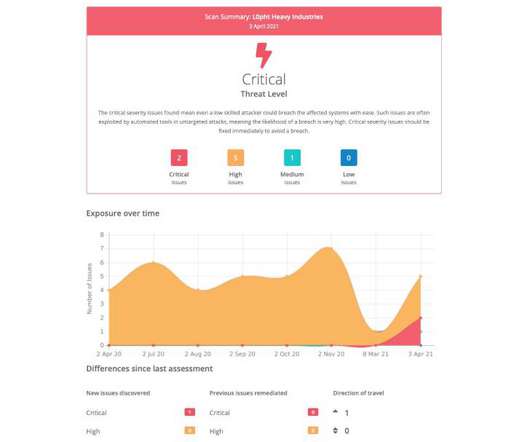
The United States Cybersecurity and Infrastructure Security Agency (CISA) recently conducted a Risk and Vulnerability Assessment (RVA), delving into the cybersecurity posture of an unnamed HPH organization utilizing on-prem software.










































Let's personalize your content