
Network-attached storage (NAS) vendor QNAP once again warned customers on Friday to secure their devices against a new campaign of attacks pushing DeadBolt ransomware.
The company is urging users to update their NAS devices to the latest firmware version and ensure they're not exposed to remote access over the Internet.
"QNAP recently detected a new DeadBolt ransomware campaign. According to victim reports so far, the campaign appears to target QNAP NAS devices running QTS 4.x," QNAP said today.
"We are thoroughly investigating the case and will provide further information as soon as possible."
This warning follows multiple three other alerts the company has issued since the beginning of 2022 [1, 2, 3], all advising users to keep their devices up to date and not expose them to Internet access.
Customers asked to update their devices
The company "strongly" recommends that all users immediately update the QTS or QuTS hero operating systems on their NAS devices to the latest version.
As QNAP said, upgrading the firmware on a compromised device will allow the built-in Malware Remover app to automatically quarantine the DeadBolt ransom note known to hijack the login page.
QNAP also advises those who cannot locate the ransom note after upgrading the firmware to enter the DeadBolt decryption key to reach out to QNAP Support for assistance.
However, before contacting QNAP's customer service, you should first try restoring the DeadBolt page using the steps detailed on this support page.
Because QNAP devices are also being targeted with other ransomware strains, including Qlocker and eCh0raix, all owners should keep their devices up to date to secure their data from future attacks.
DeadBolt ransomware
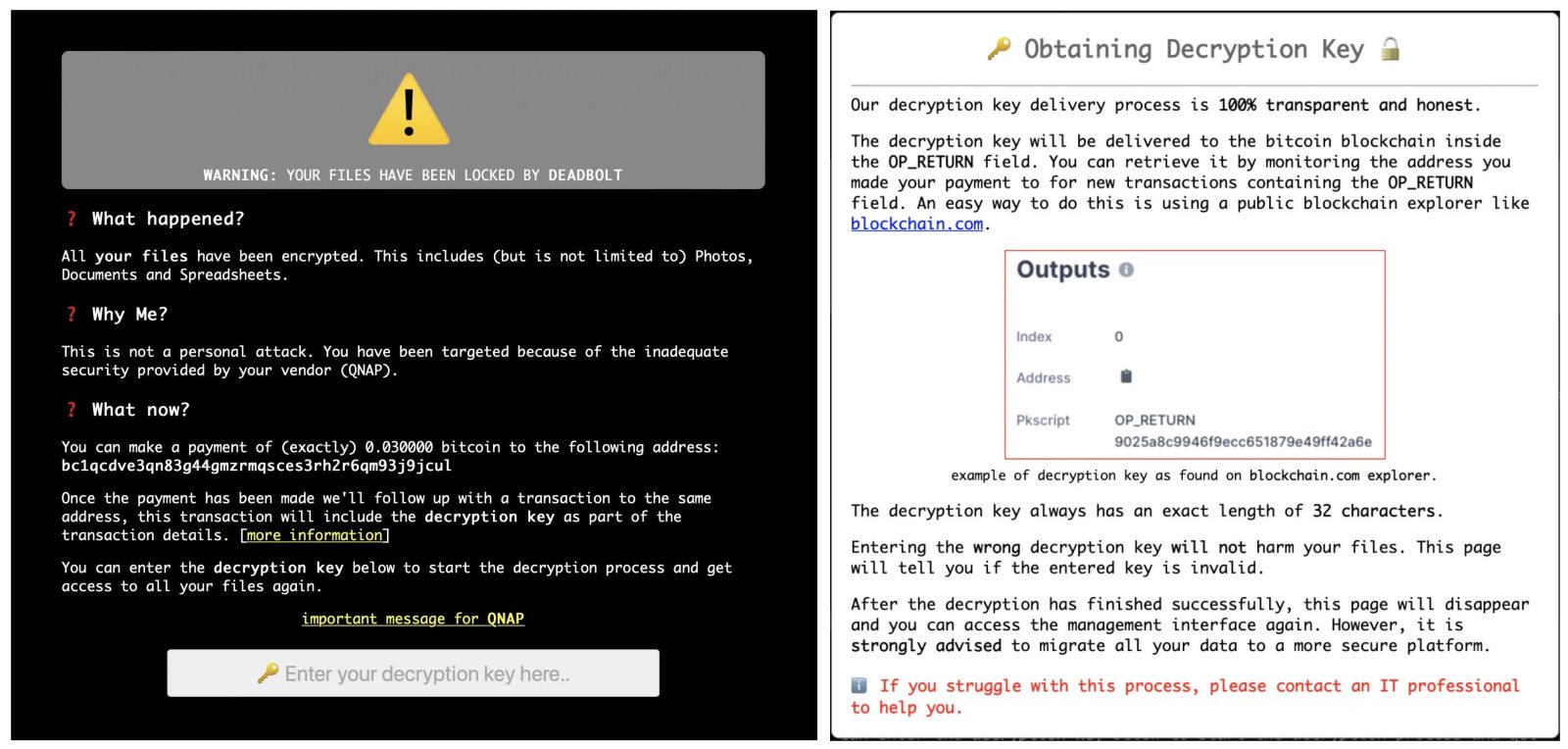
As seen during previous attacks targeting QNAP NAS devices in late January and hitting thousands of victims, DeadBolt ransomware hijacks the device's login page to display a screen stating, "WARNING: Your files have been locked by DeadBolt."
Once launched on a compromised NAS device, DeadBolt uses AES128 to encrypt files, appending a .deadbolt extension to their names.
It also replaces the /home/httpd/index.html file so that victims will see the ransom note when accessing the encrypted device.
After the victims pay a 0.03 bitcoins ransom, the threat actors create a bitcoin transaction to the same bitcoin address containing the decryption key under the OP_RETURN output.
Ransomware expert Michael Gillespie has created a free Windows decryptor that can help decrypt files without using the executable provided by DeadBolt.
However, QNAP owners hit by this ransomware will still need to pay the ransom to get a valid decryption key to recover their data.
DeadBolt ransomware has also hit ASUSTOR NAS devices in February, allegedly using a zero-day vulnerability.


Comments
tomjoad - 1 year ago
shame on QNAP! won't buy it.