
A malicious document builder named EtterSilent is gaining more attention on underground forums, security researchers note. As its popularity increased, the developer kept improving it to avoid detection from security solutions.
Cybercriminals behind operations with notorious malware started to include EtterSilent in their campaigns more often to increase the payload delivery success rate.
Using macros and exploits
Ads promoting EtterSilent maldoc builder have been published on underground forums since at least mid-2020, boasting features like bypassing Windows Defender, Windows AMSI (Antimalware Scan Interface), and popular email services, Gmail included.
In a blog post today, researchers at threat intelligence company Intel 471 note that the seller offered weaponized Microsoft Office (2007 through 2019) documents in two 'flavors': with an exploit for a known vulnerability or with a malicious macro.
One of the vulnerabilities leveraged is CVE-2017-8570, a high-severity remote code execution. The author also mentioned two other vulnerabilities (CVE-2017-11882 and CVE-2018-0802), albeit some restrictions applied, and demonstrated them in a video.
According to Intel 471, the variant with the macro is the more popular variant, likely because of the "lower pricing and higher compatibility when compared to the exploit."
An EtterSilent maldoc with macro code can pose as a DocuSign or DigiCert document that asks users to enable support for macros that downloads a payload in the background.
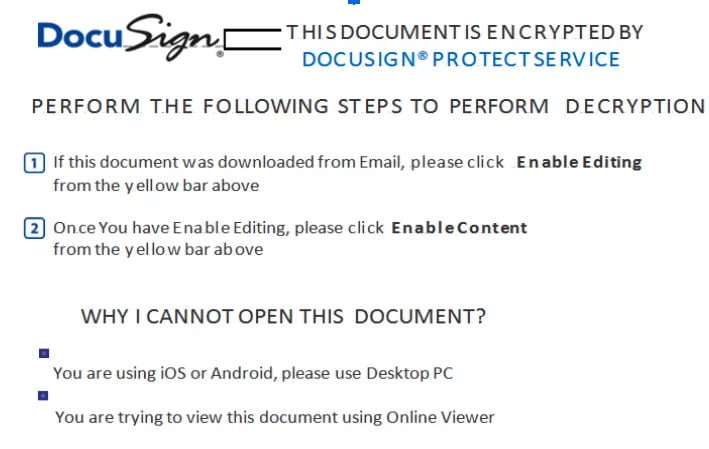
Because it uses Excel 4.0 XML macros, EtterSilent does not depend on the Visual Basic for Applications (VBA) programming language, which is commonly seen with malicious macros.
"The maldoc then leverages Excel 4.0 macros stored in a hidden sheet, which allow an externally-hosted payload to be downloaded, written to disk and executed using regsvr32 or rundll32. From there, attackers can follow up and drop other assorted malware" - Intel 471
Low detection attracts big names
The researchers note that an EtterSilent maldoc was included in a recent spam campaign that dropped an updated version of Trickbot. The gang used the same method in a campaign on March 19 to infect systems with BazarLoader/BazarBackdoor.
Intel 471 says that other cybercriminal groups leveraged EtterSilent services for their operations. Some examples are banking trojans IcedID/BokBot, Ursnif/Gozi ISFB, and QakBot/QBot. Along with Trickbot, most of them have been used to deliver various ransomware strains (Ryuk, Conti, Maze, Egregor, ProLock).
Gangs as prolific as these are constantly looking for new ways to distribute their payloads while drawing as little attention as possible and the EtterSilent maldoc service appears to provide a good cover.
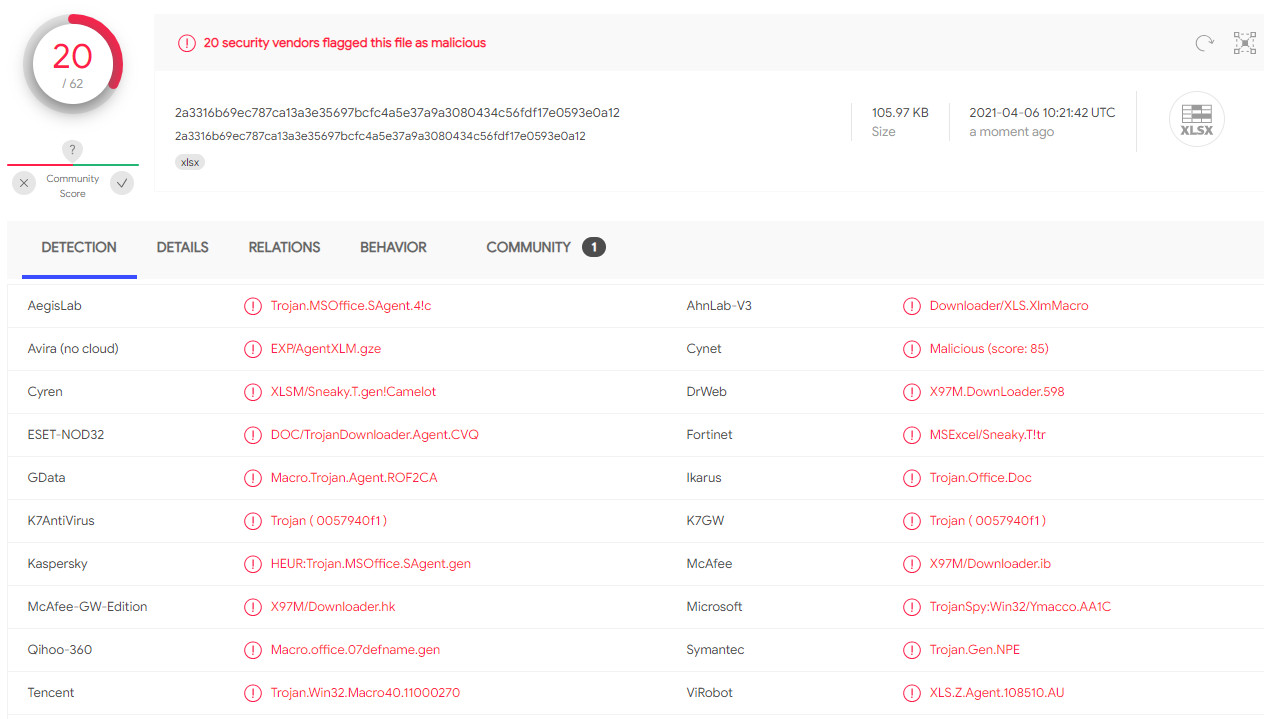
In early March, some of the weaponized documents built with this tool went completely undetected by all antivirus engines included in a scanning service.
A week ago, less than a handful of antivirus engines detected one weaponized document built with this tool. At the time of writing, the detection increased to 20/40 engines in VirusTotal. For another file, the detection increased over six days from 16/62 to 20/62.
In a post last year, EtterSilent had a price tag of $130 for the normal build. A more expensive tier also existed, though: $230 for a custom stub to make malicious files unique by encrypting them.
Intel 471's Chief Information Security Officer, Brandon Hoffman, told BleepingComputer that those prices are for the exploit version of the maldoc builder. For the macro variant, the price is around $9 per build.
As for the seller, Hoffman told us that they are a "prominent Russian speaking actor" that's been active for the past two years showing interest in malware crypting, malicious Microsoft office docs, malware loaders, and evasion techniques.
Intel 471's blog provides a list of indicators of compromise for EtterSilent malicious documents as well as for the payloads they delivered: Trickbot, IcedID, QBot, Ursnif, and BazarLoader.
Update [April 6, 15:44]: Clarified information about the price and added details about the threat actor from Intel 471 CISO, Brandon Hoffman.



Comments
Mike_Walsh - 3 years ago
"WHY I cannot open this document....?"
That, RIGHT THERE, is a big warning 'give-away' to anyone who's even half awake. The grammar is atrocious, and is clearly written by someone to whom English is NOT their native language.....
EmanuelJacobsson - 3 years ago
Yet it works, because a majority of the population thinks the internet is this magical place where nothing bad can happen.