
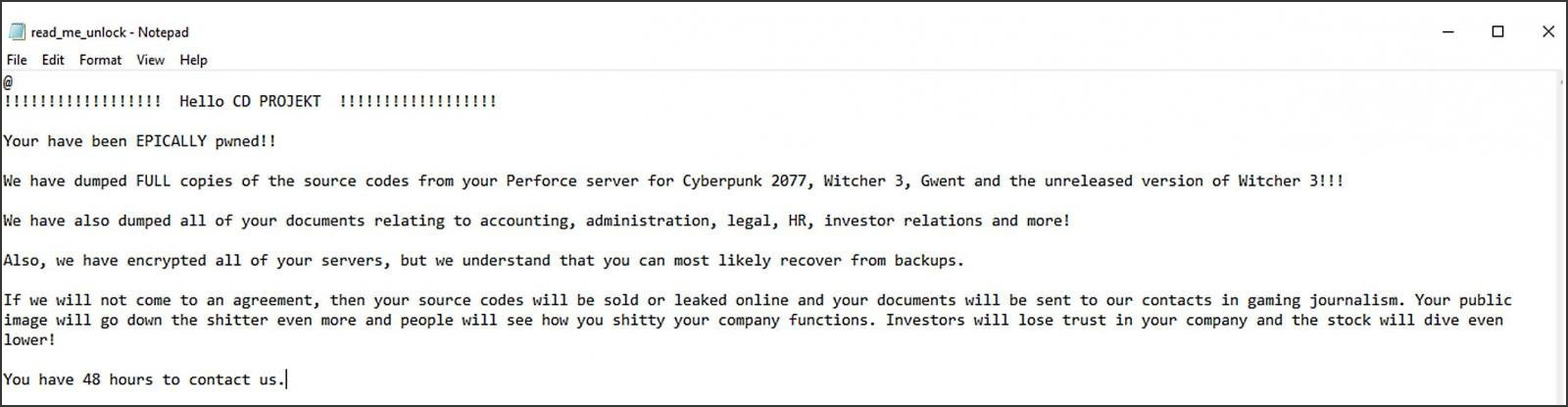
Threat actors are auctioning the alleged source code for CD Projekt Red games, including Witcher 3, Thronebreaker, and Cyberpunk 2077, that they state were stolen in a ransomware attack.
Yesterday, CD Projekt suffered a ransomware attack where the attackers claim to have stolen unencrypted source code for Cyberpunk 2077, Witcher 3, Gwent, and an unreleased version of Witcher 3.
As part of the double-extortion attempt, the attackers threatened to release or sell the stolen data if CDPR did not pay the ransom.
This attack was later confirmed to be conducted by the HelloKity ransomware group.
When disclosing the attack, CD Projekt stated that they would not give into the ransom demands and are restoring from backups instead.
Threat actors begin to auction allegedly stolen data
Today, security researcher VX-Underground tweeted that the threat actors have started to auction what they claim is stolen data from the CD Projekt attack.
This data allegedly includes stolen internal documents, 'CD Projekt offenses,' and the source code for Cyberpunk 2077, Witcher 3, Thronebreaker, and an unreleased Witcher 3 version with raytracing.
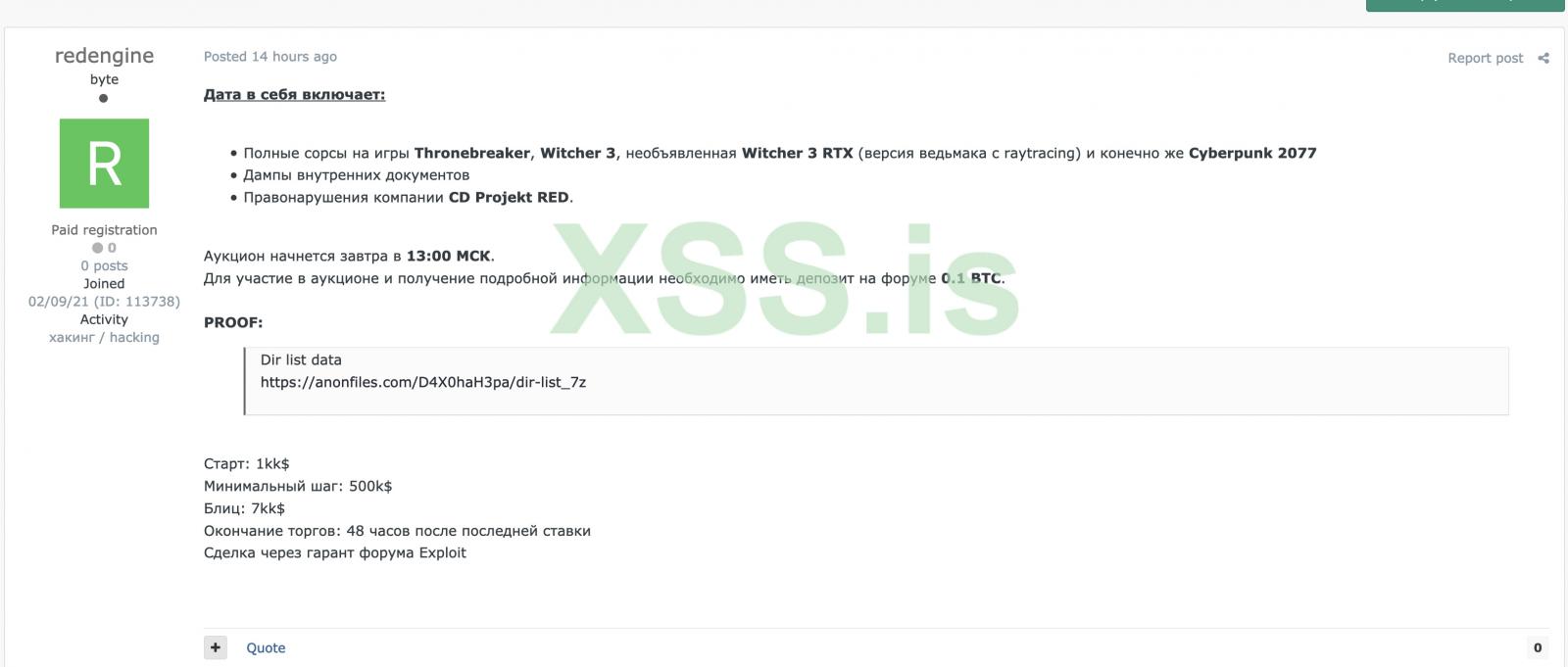
The starting price for this auction is $1 million with bid increments of $500,000 and a 'blitz' or buy now price of $7 million.
To prove the stolen data's validity, the seller known as 'redengine' has shared a text file containing a directory listing from the alleged Witcher 3 source code.
Cyber intelligence firm Kela told BleepingComputer that they believe the auction to be legitimate due to the directory listing and the demand to use a middle man to handle the sale.
"The seller is requiring buyers to use a guarantor and have a deposit - this user is new to the forum, but we think that maybe this is a known user that just created a new account in order to prevent them from being traced by researchers."
"Additionally, the demand for using a middleman seems to be their way to ensure that there is no scam that will occur," Kela threat intelligence analyst Victoria Kivilevich told BleepingComputer.
Alleged Gwent source code released for free
A threat actor who claims to be part of the HelloKitty ransomware operation told BleepingComputer that the auction is only being held on the well-known cybercrime forum Exploit.in.
As part of this data leak and to further prove the data's validity, this threat actor released a 21 GB archive for free on hacker forums that allegedly contains the source code for the Gwent card game.
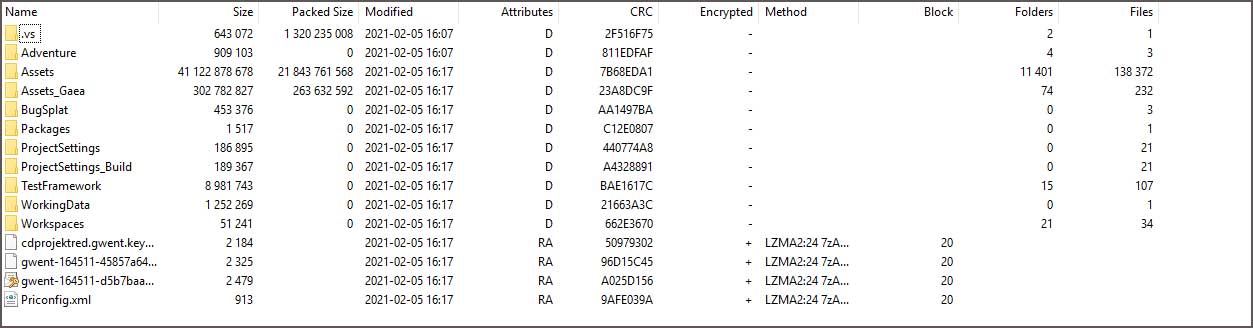
BleepingComputer has not been able to verify if the source code is legitimate independently.
BleepingComputer has contacted CD Projekt to confirm if this leaked data is legitimate but has not heard back.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now