
The emergency patches for the recently disclosed critical vulnerabilities in Microsoft Exchange email server did not come soon enough and organizations had little time to prepare before en masse exploitation began.
Named ProxyLogon, the bug has been exploited in the wild even before Microsoft received the vulnerability report, giving attackers a two-month head start to breach targets before security updates became available.
Vulnerable servers are hot targets for a wide spectrum of threat actor groups looking for an initial foothold into a network for espionage or financial purposes. Nation-state adversaries, ransomware gangs, and cryptomining activities have already exploited ProxyLogon.
With patches released and proof-of-concept (PoC) exploit code surfacing online, thousands of Microsoft Exchange servers worldwide continue to remain vulnerable and the number of attacks is still at a worrying level.
ProxyLogon threat found
On December 10, 2020, DEVCORE researcher Orange Tsai discovered CVE-2021-26855, a critical server-side request forgery (SSRF) flaw that allows bypassing authentication in Microsoft Exchange.
DEVCORE named the bug ProxyLogon and, at the end of December, Tsai found a second one (CVE-2021-27065) that could be used to achieve remote code execution.
The researcher on January 5, 2021, forwarded to Microsoft a report along with an exploit chaining the two flaws to prove the validity of his findings.
APT groups had a two-month advantage
The same month, threat intelligence and incident response company Volexity detected ProxyLogon attacks aiming to compromise networks or to steal email data.
Closer examination determined that “cyber espionage operations using the SSRF vulnerability CVE-2021-26855 started occurring on January 3, 2021,” two days before DEVCORE submitted the report to Microsoft.
In January, multiple cybersecurity companies detected attacks against on-premise Exchange servers in client environments using zero-day vulnerabilities.
The network of at least one FireEye customer was breached that month and the intruder created web shells for persistence access and remote code execution, and the activity “suggested exploitation of CVE-2021-26858,” the company said.
Dropping web shells (ASPX files) is also what Volexity saw, followed by credential dumping, adding user accounts, stealing copies of the Active Directory database (NTDS.DIT), and lateral movement on the network.
Also in January, Danish incident response firm Dubex investigated activity on Exchange servers that used a zero-day (CVE-2021-26857) exploit to write web shells to disk, listing a set of three ASPX files among the indicators of compromise (IoCs).
On March 2, Microsoft released updates for Exchange Server and informed of “multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks.”
Microsoft attributes the incidents to a state-sponsored group named Hafnium that operates out of China and exploited the following vulnerabilities before a patch was available:
- CVE-2021-26855, pre-authentication SSRF
- CVE-2021-26857, insecure deserialization leading to privilege escalation to SYSTEM level
- CVE-2021-26858, post-authentication file write
- CVE-2021-27065, post-authentication file write
Hafnium, which may have compromised 68,500 Exchange servers by the time patches were available, is not the only APT group that leveraged the bugs above before the patches came out.
ESET said that other actors - Tick, LuckyMouse, Calypso, Winnti, Websiic - many of them China-linked, had been actively exploiting them since at least February 28 and recommended organizations to look for suspicious ASPX files.
“This suggests that multiple threat actors gained access to the details of the vulnerabilities before the release of the patch, which means we can discard the possibility that they built an exploit by reverse engineering Microsoft updates” - ESET
MSP threat detection provider Huntress Labs analyzing a few hundred compromised Exchange servers also found that some had been hacked days before Microsoft released the patches, on February 27.
Threat actor used DEVCORE’s exploit
One of the exploits used in the wild before the patches arrived is the same chain that DEVCORE submitted to Microsoft on January 5 as part of the responsible disclosure.
DEVCORE confirms this in an update on the ProxyLogon website, noting that it started to investigate after Volexity reported active exploitation of the SSRF bug.
“Regarding the multiple attacks that Volexity mentioned on January 3rd [sic], we are not aware of when our exploit was used in the wild,” DEVCORE told BleepingComputer.
“After learning that ProxyLogon exploit has been used by HAFNIUM from the exploitation advisory from Volexity and the blog post from Huntress, DEVCORE immediately launched an internal investigation on March 3rd to verify whether the team has been hacked or any information has been leaked from our end.”
DEVCORE told BleepingComputer that a thorough examination of personal computers and devices of its employees, and its infrastructure and systems showed no signs of hacking, indicating that the leak may have occurred somewhere else.
“Also, we have investigated our internal system and found no unusual login attempts or file access” - DEVCORE
According to a report from Wall Street Journal, Microsoft is currently investigating whether one of its partners that had access to the information leaked it intentionally or by accident.
Most security software providers are part the Microsoft Active Protections Program (MAPP), which gives them early access to vulnerability information so they can update protections for their customers quicker.
A wide spectrum of attackers
Once official patches came out, even for unsupported versions, vulnerable Microsoft Exchange servers directly exposed on the internet became an even hotter target as threat actors could reverse engineer the updates to build an exploit.
ESET saw more than 10 APT groups rushing to attack unpatched devices. Many were running cyberespionage operations, and this list includes Mikroceen and Tonto Team, but not all.
The researchers noticed activity from a group they call “Opera” Cobalt Strike that exploited the Microsoft Exchange vulnerabilities to install the Cobalt Strike penetration testing product that is common to some high-profile ransomware gangs.
In another instance, ESET saw an adversary dropping web shells to “install so-called IIS backdoors.” Activity attributed to the DLTMiner [1, 2] cryptomining botnet was seen on servers that had been targeted using the ProxyLogon vulnerabilities.
The DLTMiner botnet shows similarities in infrastructure and behavior with another cryptocurrency botnet called Lemon_Duck, whose infrastructure has been documented in IoCs for hacked Exchange servers.
Security professionals at Shadowserver saw yesterday more than 8,000 IP addresses that showed signs of DLTMiner activity, most of them in China and the U.S.
Ransomware also jumped in and started to compromise Microsoft Exchange server using the ProxyLogon vulnerabilities. BleepingComputer broke the story on the evening of March 9th about a new piece of file-encrypting malware called DearCry used in attacks on Exchange servers.
PoCs and attack tools
Starting March 10, PoC exploit for the massively exploited Exchange vulnerabilities started to appear online. The first variant was a buggy remote code execution exploit that Microsoft quickly pulled from GitHub to prevent abuse at an even larger scale.
A new ProxyLogon PoC emerged over the weekend, increasing the chances of even low-skilled attackers to go after vulnerable Exchange servers, which are likely in the thousands.
Furthermore, there is plenty of information to reproduce the ProxyLogon exploit by reverse-engineering the official patches from Microsoft. Cybersecurity firm Praetorian published a blog with full technical details to create a working end-to-end exploit.
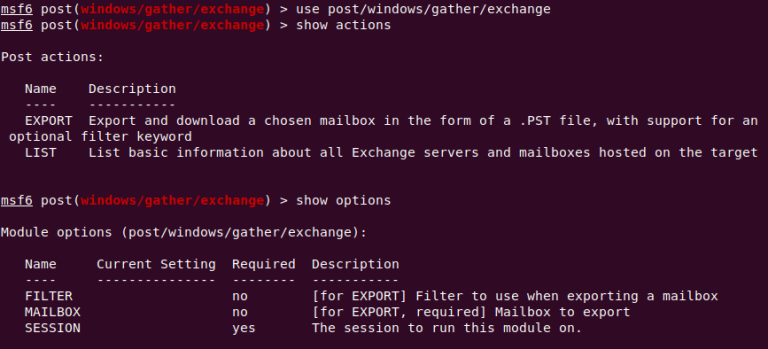
SophosLabs created a tool called metasploit_gather_exchange that can extract all the contents of an inbox as a PST file. It does not help hack Exchange servers but is meant as a post-exploitation tool for red team penetration test engagements.
Plenty of unpatched Exchange servers around
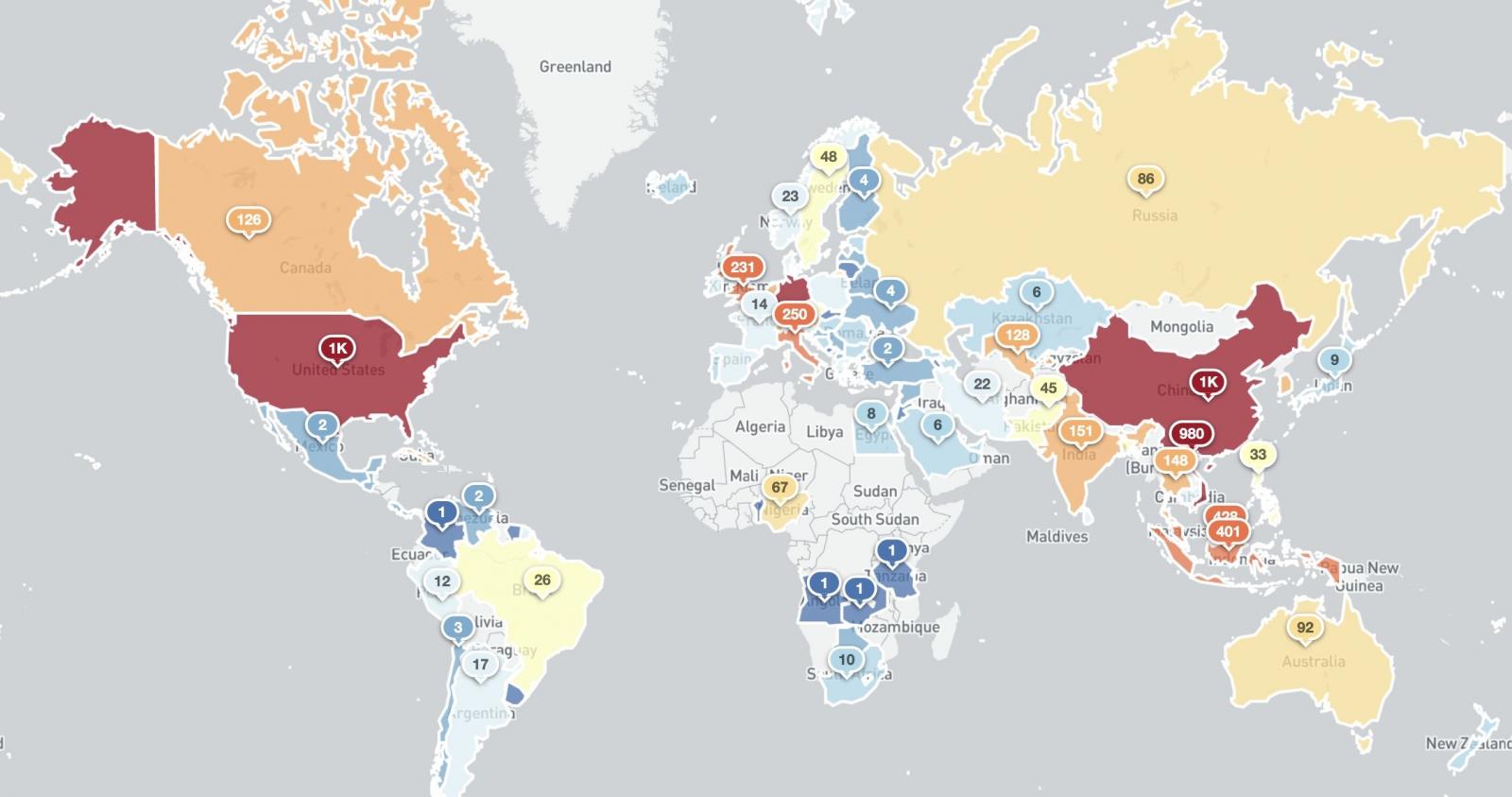
Victor Gevers, the chair of the Dutch Institute for Vulnerability Disclosure, told BleepingComputer on Friday that there were about 64,000 vulnerable Microsoft Exchange servers around the world.
A report from Shadowserver today, which combines data from KryptosLogic, reveals that on Sunday, the number of potentially vulnerable Microsoft Exchange servers in the world was 59,218.
These figures are smaller than the 80,000 that Palo Alto Networks recorded in internet scans between March 8-11 using its Expanse platform, likely because of the high patch rates for Microsoft Exchange.
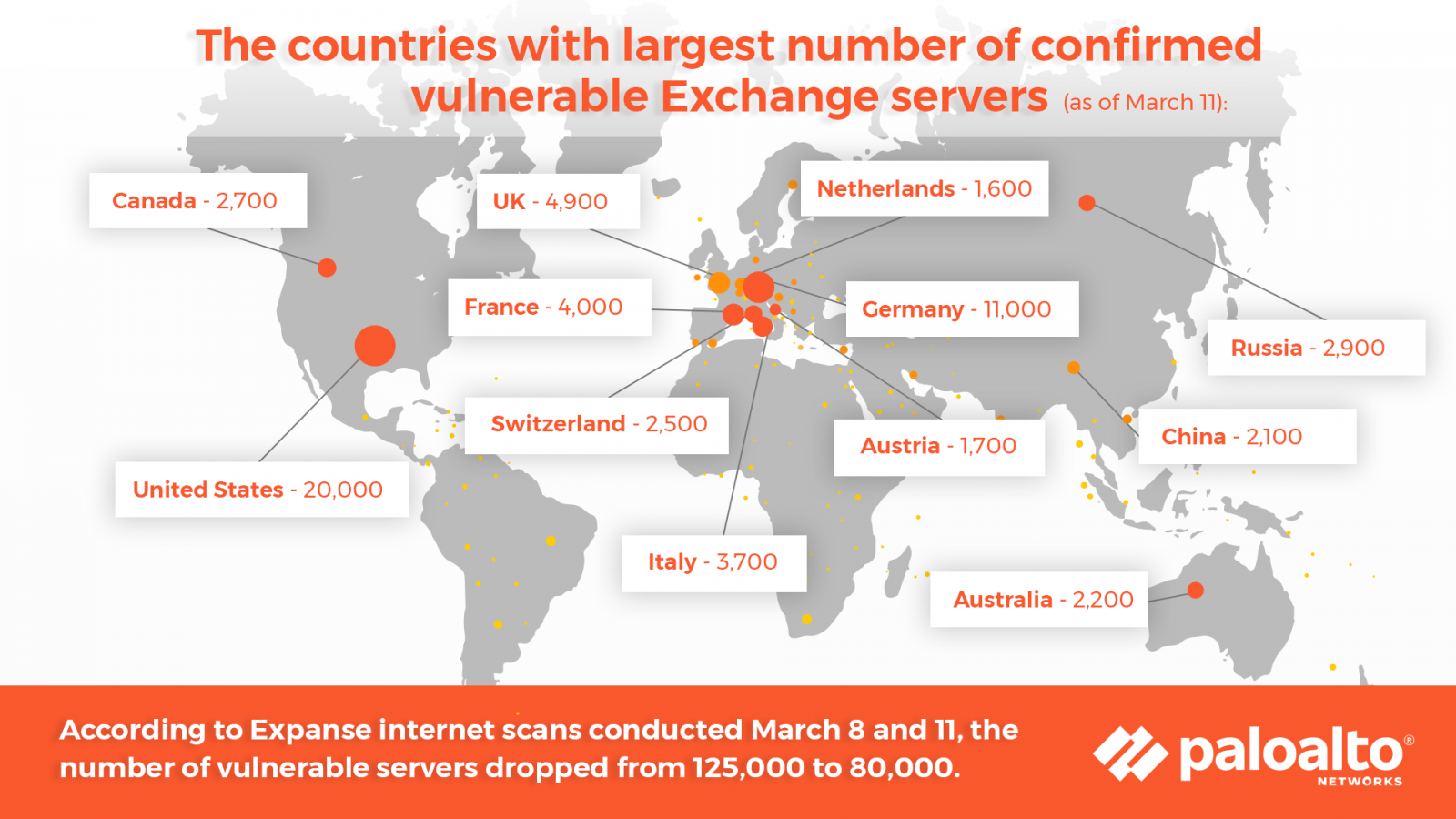
Matt Kraning, Chief Technology Officer, Cortex at Palo Alto Networks, said that organizations running any version of Exchange should “assume they were compromised before they patched their systems” because of the massive exploitation that began in January.
Even if the servers are not facing the public internet, companies should update them to defend against actors that could be on the local network.
Mandiant vice-president of analysis, John Hultquist, is expecting more exploitation of the ProxyLogon vulnerabilities soon from ransomware gangs, which may find the attack vector “particularly attractive” because it makes for “an efficient means of gaining domain admin access.”
“That access enables them to deploy encryption across the enterprise. In cases where organizations are unpatched, these vulnerabilities will provide criminals a faster path to success” - John Hultquist
Kaspersky has also warned about the high risk of ransomware infection and the data theft danger associated with these attacks. Since Microsoft released the patches, the company has seen "an increased amount of automated attempts at mass exploitation of new Exchange vulnerabilities."
A company representative told BleepingComputer that they're expecting the number of attacks to grow until most users install the updates.
"It seems that the actors behind these attacks are trying to compromise as many organizations as possible. It is yet to be uncovered how they will try to use the access in the future" - Kaspersky
According to Check Point Research, hackers keep trying to exploit ProxyLogon, with attacks growing more than ten times over the past four days. Since Thursday, the company saw the number of attempts grow from 700 to 7,200 today.
On Friday, UK's National Cyber Security Centre (NCSC) said that more than 3,000 email servers in the country were vulnerable and that malware had been detected on 2,300 of them.
Tools and info of the trade
With all the hacking beginning more than two months ago, many Exchange servers may have already been compromised by the time they get the updates.
CISA has published seven Malware Analysis Reports to its alert with mitigations for the Microsoft Exchange Server vulnerabilities. Each of them provides details about a webshell used in attacks to give adversaries remote administration on the system.
Many cybersecurity companies strongly recommend checking for signs of compromise before installing the patches. For this purpose, Microsoft added signatures to Microsoft Defender to detect web shells installed after exploiting the vulnerabilities.
The same can be achieved using the portable Microsoft Support Emergency Response Tool (MSERT), which automatically deletes any detected files without quarantine.
Administrators can also use a PowerShell script to check if Exchange servers were hacked using the ProxyLogon vulnerabilities. It automates a set of commands that can also be run manually to test either one or all on-premise servers.
Dubex recommends checking Exchange and Internet Information Services (IIS) logfiles for known IoCs [1, 2, 3, 4, 5, 6] and the hosts for signs of web shells/hashes, IoCs in known paths and filenames, LSASS dumps.
Furthermore, companies can check if their Exchange Server has been compromised by using Check My OWA. It's a new service that compiles lists of compromised servers with Outlook Web Access (OWA) turned on. The data includes affected IP addresses and domains and can reveal if actors in the initial attacks were able to load a shell on the machine.
Check My OWA can be used by simply loading it from the Exchange server and a warning pops up if it's found in the service's list; or you can type in a business email address and a message will reach your inbox informing if your domain is a match in the database.
IoC checking scripts:
Microsoft > github.com/microsoft/CSS-Exchange/tree/main/Security
PwnDefend > github.Com/PwnDefend/Exchange-RCE-Detect-Hafnium
CERT Latvia > github.Com/cert-lv/exchange_webshell_detection
sgnls > github.com/sgnls/exchange-0days-202103
Soteria > github.com/soteria-security/HAFNIUM-IOC
Daniel Card of PwnDefend > github.com/mr-r3b00t/ExchangeMarch2021IOCHunt
Daniel Card of PwnDefend > github.com/PwnDefend/badExchangePews (community-based list of bad IPs)
Yara rule for DearCry / DoejoCrypt
IoCs for DearCry:
- feb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33ede
- e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6
- 10bce0ff6597f347c3cca8363b7c81a8bff52d2ff81245cd1e66a6e11aeb25da
- 2b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bff



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now