
The Center for Internet Security (CIS), a non-profit dedicated to securing IT systems and data, has announced the launch of free ransomware protection for US private hospitals through the Malicious Domain Blocking and Reporting (MDBR) service.
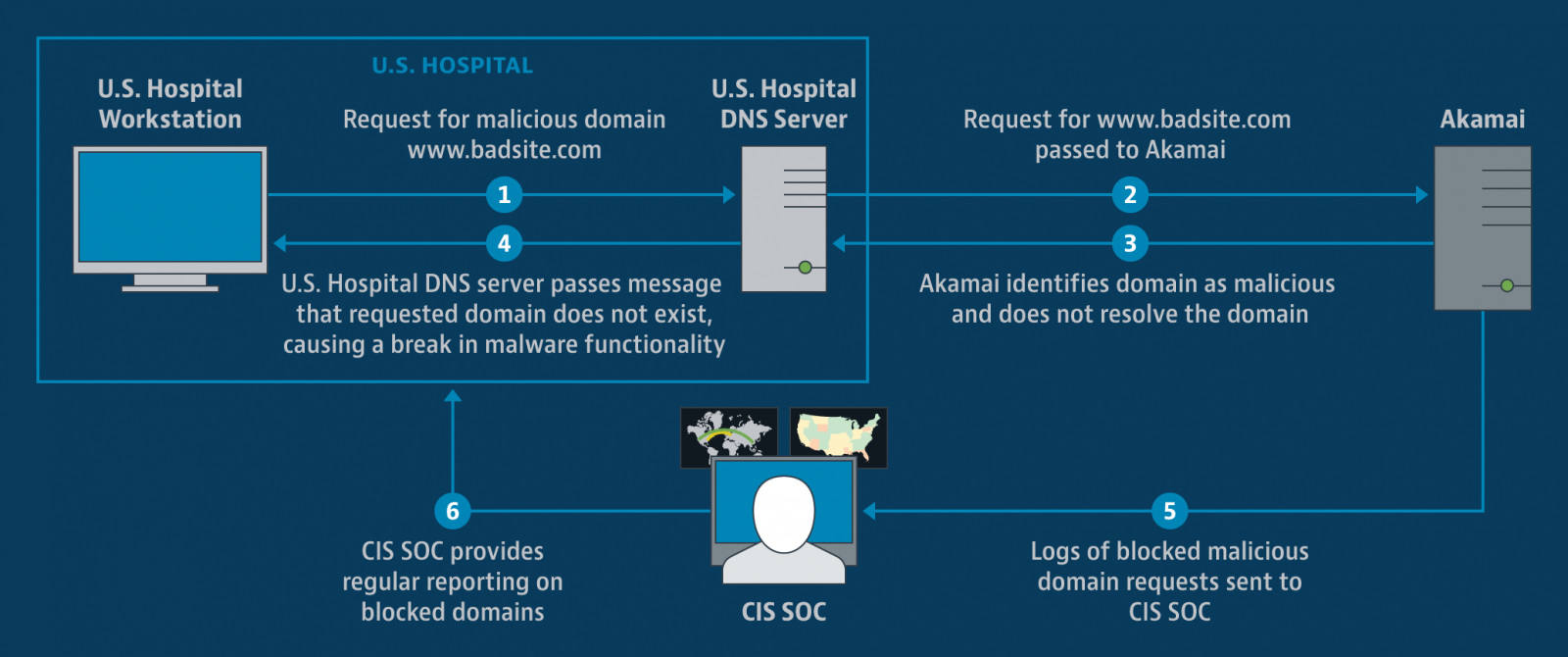
The MDBR service, powered by systems maintained by CIS and Akamai, automatically blocks domains associated with cyber threats including ransomware, malware, and phishing after the organizations switch their DNS provider to Akamai's DNS server.
"This capability can block the vast majority of ransomware infections just by preventing the initial outreach to a ransomware delivery domain," as CIS explains.
CIS will fund the MDBR service at no-cost for several types of health care organizations including independent hospitals, multi-hospital systems, hospital-based integrated health systems, post-acute patient care facilities, psychiatric, rehabilitation, or other specialty hospitals.
Public health care orgs already protected by MDBR
MDBR has been protecting public healthcare organizations, hospitals, and health departments under funding provided by DHS-CISA through the Multi-State Information Sharing and Analysis Center (MS-ISAC).
This federally funded pilot program is being currently used by over 1,000 US state, local, tribal, and territorial (SLTT) government organizations.
"The CIS Board of Directors prioritized making MDBR service available to all public and private U.S. hospitals at no cost, through both the MS-ISAC for public hospitals and a $1 million investment of CIS funds for private hospitals this year," Ed Mattison, Executive Vice President of CIS Operations and Security Services, said.
"CIS is fully funding this for private hospitals at no cost, and with no strings attached because it’s the right thing to do and no one else is doing it at scale."
With the launch of the free ransomware protection for private healthcare organizations, CIS is now providing this service at no-cost for all US hospitals.
Already stopped some ransomware attacks in their tracks
Since it was launched, MDBR blocked millions of requests for malicious domains which could have led to potentially successful attacks or ransomware infections affecting SLTT organizations.
MDBR blocked nine instances of ransomware domains for a group of nine US public health orgs just in December 2020 alone, preventing major cyber incidents that could have affected hundreds of thousands of people.
"The COVID-19 pandemic has made hospitals an even larger target for malicious cyber threats than they were already," Mattison added.
"While other commercial cybersecurity organizations are certainly supporting hospitals and hospital systems, our nonprofit status and mission focus enable us to offer this service at no cost and at scale to any hospital or system that can benefit from it."
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) warned of an imminent cybercrime threat to hospitals and healthcare providers in a joint report published at the end of October 2020.
The advisory's goal was to prepare organizations for ransomware attacks with Ryuk and Conti ransomware by sharing tactics, techniques, and procedures (TTPs) specific to incidents where these malware strains are deployed.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now