
Advanced hackers are actively exploiting a critical remote code execution (RCE) vulnerability, CVE-2022-22954, that affects in VMware Workspace ONE Access (formerly called VMware Identity Manager).
The issue was addressed in a security update 20 days ago along with two more RCEs - CVE-2022-22957 and CVE-2022-22958 that also affect VMware Identity Manager (vIDM), VMware vRealize Automation (vRA), VMware Cloud Foundation, and vRealize Suite Lifecycle Manager.
Soon after the public disclosure of the flaws, proof of concept (PoC) exploit code emerged in the public space, enabling hackers leveraged to target vulnerable VMware product deployments. VMware confirmed CVE-2022-22954 exploitation in the wild.
Now, researchers at Morphisec report seeing exploitation from advanced persistent threat (APT) actors, particularly an Iranian hacking group tracked as APT35, aka “Rocket Kitten.”
Attack details
The adversaries gain initial access to the environment by exploiting CVE-2022-22954, the only one in the RCE trio that doesn’t require administrative access to the target server and also has a publicly available PoC exploit.
The attack starts with executing a PowerShell command on the vulnerable service (Identity Manager), which launches a stager.
The stager then fetches the PowerTrash loader from the command and control (C2) server in a highly obfuscated form and loads a Core Impact agent into the system memory.
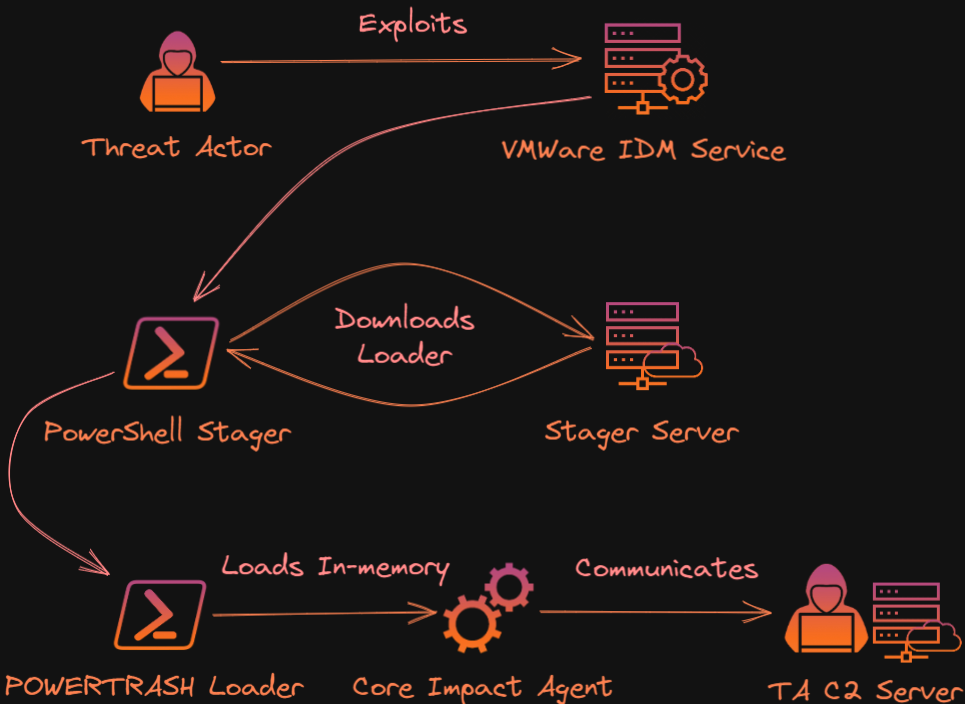
Core Impact is a legitimate penetration testing tool that is abused for nefarious purposes in this case, similar to how Cobalt Strike is deployed in malicious campaigns.
This isn't a novel element, though. Trend Micro has reported Core Impact abuse in the past by APT35, the activity dating as far back as 2015.
“Morphisec research observed attackers already exploiting this vulnerability (CVE-2022-22954) to launch reverse HTTPS backdoors—mainly Cobalt Strike, Metasploit, or Core Impact beacons” - Morphisec
Morphisec CTO Michael Gorelik told BleepingComputer that the attacker tried lateral movement on the network, although the backdoor was stopped.
“With privileged access, these types of attacks may be able to bypass typical defenses including antivirus (AV) and endpoint detection and response (EDR),” Morphisec adds in the report.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now