A new set of vulnerabilities collectively tracked as Nimbuspwn could let local attackers escalate privileges on Linux systems to deploy malware ranging from backdoors to ransomware.
Security researchers at Microsoft disclosed the issues in a report today noting that they can be chained together to achieve root privileges on a vulnerable system.
Tracked as CVE-2022-29799 and CVE-2022-29800, the Nimbuspwn security issues were discovered in networkd-dispatcher, a component that sends connection status changes on Linux machines.
Discovering the vulnerabilities started with “listening to messages on the System Bus,” which prompted the researchers to review the code flow for networkd-dispatcher.
The Nimbuspwn security flaws refer to directory traversal, symlink race, and time-of-check-time-of-use (TOCTOU) race condition issues, explains Microsoft researcher Jonathan Bar Or says in the report.
One observation that piqued interest was that the networkd-dispatcher daemon was running at boot time with root privileges on the system.
The researcher noticed that the daemon used a method called “_run_hooks_for_state” to discover and run scripts depending on the detected network state.
The logic implemented by “_run_hooks_for_state” includes returning executable script files owned by the root user and the root group that are in the “/etc/networkd-dispatcher/.d” directory.
It runs each script in the above location using the process called subprocess.Popen while supplying custom environment variables.
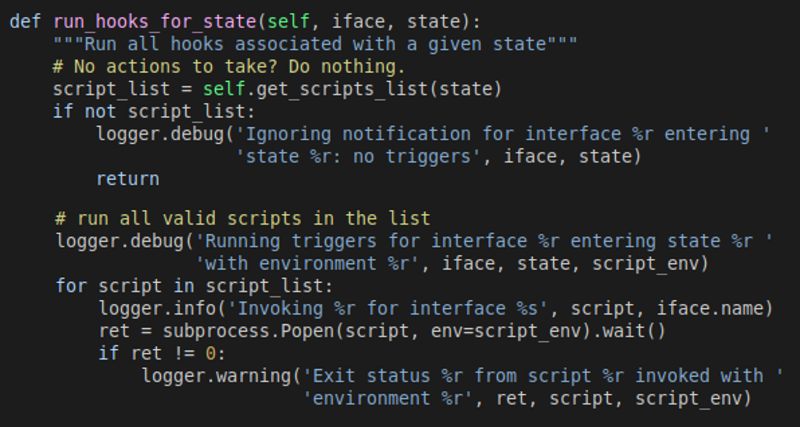
Microsoft’s report explains that “_run_hooks_for_state” has multiple security issues:
- Directory traversal (CVE-2022-29799): none of the functions in the flow sanitize the OperationalState or the AdministrativeState. The states are used to build the script path, so a state could contain directory traversal patterns (e.g. “../../”) to escape from the “/etc/networkd-dispatcher” base directory.
- Symlink race: both the script discovery and subprocess.Popen follow symbolic links.
- Time-of-check-time-of-use (TOCTOU) race condition (CVE-2022-29800): there is a certain time between the scripts being discovered and them being run. An attacker can abuse this vulnerability to replace scripts that networkd-dispatcher believes to be owned by root to ones that are not.
An attacker with low privileges on the system could chain together the above vulnerabilities to escalate to root-level permissions by sending an arbitrary signal.
An overview of the steps for successful exploitation is captured in the image below, which covers three stages of the attack:
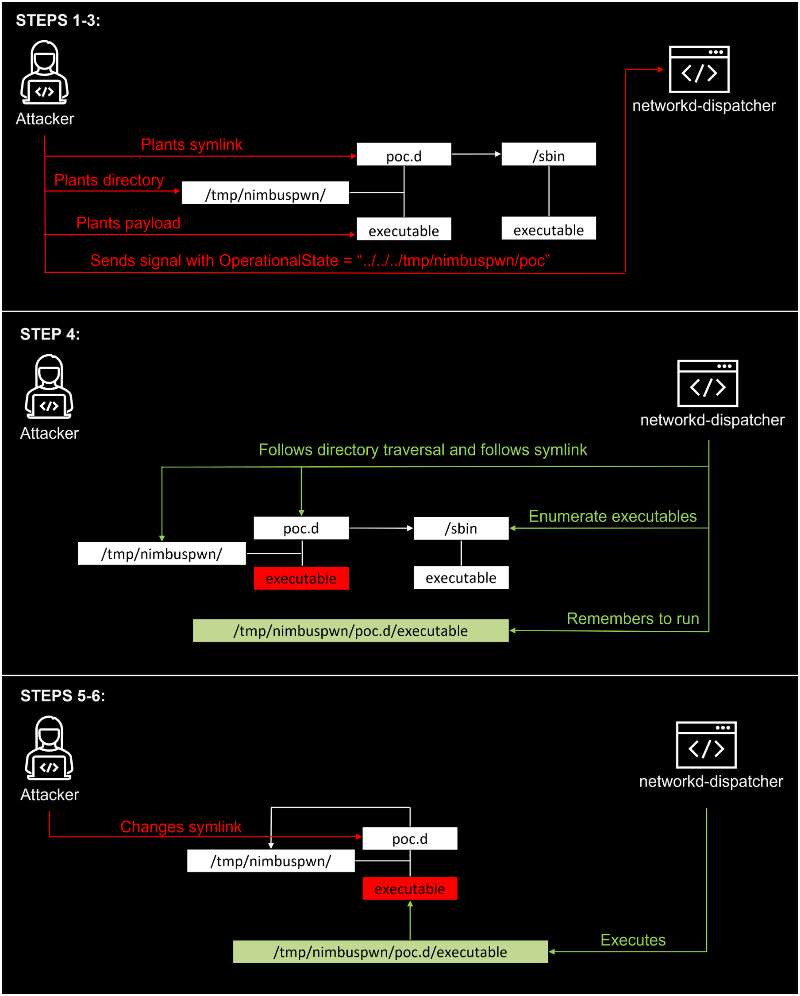
Bar Or notes that winning the TOCTOU race condition requires planting multiple files. In his experiment to implement a custom exploit, success was recorded after three attempts.
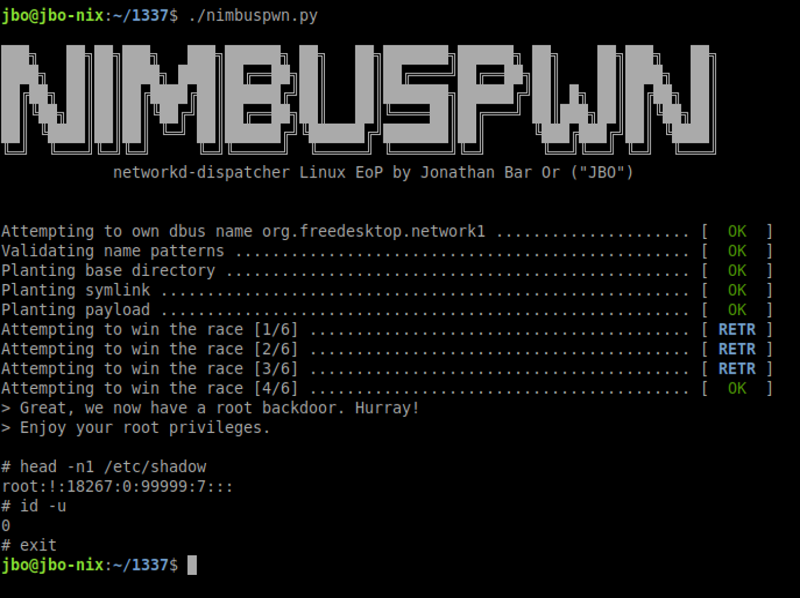
Leveraging Nimbuspwn successfully is possible when the exploit code can own a bus name under a privileged service or process.
The researcher says that there are many environments where this is possible, including Linux Mint where “the service systemd-networkd that normally owns the “org.freedesktop.Network1” [used in the research] bus name does not start at boot by default.”
Additionally, the Bar Or found additional “processes running as the systemd-network user” that executed arbitrary code from world-writable locations: e.g. several gpgv plugins (launched when apt-get installs or upgrades), the Erlang Port Mapper Daemon (epmd) that allows running arbitrary code under some scenarios.
Clayton Craft, the maintainer of networkd-dispatcher has deployed the necessary updates that address the Nimbuspwn vulnerabilities.
Linux users are recommended to patch their systems as soon as the fixes become available for their operating system.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now