
Some organizations victimized by the Royal and Akira ransomware gangs have been targeted by a threat actor posing as a security researcher who promised to hack back the original attacker and delete stolen victim data.
Both Royal and Akira ransomware operations use the double extortion tactic - encrypting victim systems after stealing info, and threaten with a data leak unless a ransom is paid.
Cybersecurity company Arctic Wolf says it has investigated "several cases" where victims of the two ransomware groups that paid a ransom were approached by a threat actor claiming to be an ethical hacker or security researcher with a deep understanding of the field.
The fake researcher offered to provide proof of access to the stolen data still on the attacker's servers and said they could delete it for a fee of up to five Bitcoins (around $190,000 at the time).
Arctic Wolf’s report presents two cases from October and November 2023, where the cybercriminal contacted organizations that had been compromised by Royal and Akira ransomware.
In the first case, the scammer posed as the ‘Ethical Side Group’ (ESG) and initially mistakenly attributed the attack to the ‘TommyLeaks’ gang, later switching to a narrative claiming access to Royal’s server.
It is worth noting that this victim had engaged in negotiations with the ransomware actor a year before, in 2022.
In the second incident, the scammer used the moniker ‘xanonymoux’ and offered to delete files on Akira’s servers or provide access to the actor's server.
However, in communication several weeks before the hack-back offer, Akira said they did not exfiltrate any data and their attack only encrypted the breached systems.
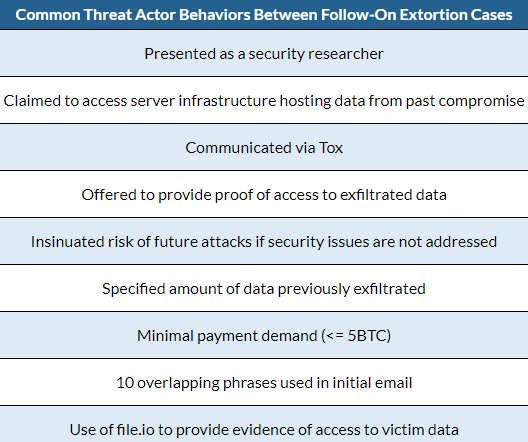
Arctic Wolf reports that the initial communication over an instant messaging program contained ten common phrases and the same method was used for providing proof of access to the stolen data. This suggests that the same individual was behind both attempts.
Ransomware attacks present a complex web of challenges for victims, extending far beyond the immediate crisis of encrypted and stolen data, having an enduring effect.
These scamming attempts highlight yet another aspect of the multi-layered problem and constitute additional risks that can compound the financial burden for ransomware victims.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now