
Trend Micro says it patched a DLL hijacking flaw in Trend Micro Security used by a Chinese threat group to side-load malicious DLLs and deploy malware.
As Sentinel Labs revealed in an early-May report, the attackers exploited the fact that security products run with high privileges on Windows to plant and load their own maliciously crafted DLL into memory, allowing them to elevate privileges and execute code.
"Trend Micro is aware of some research that was published on May 2, 2022, regarding a purported Central-Asian-based threat actor dubbed 'Moshen Dragon' that had deployed malware clusters that attempted to hijack various popular security products, including one from Trend Micro," the cybersecurity company said.
After analyzing the report and its product line, the company discovered that only the Trend Micro Security consumer-focused product was affected, with no other commercial or business products impacted.
"For Trend Micro Security (Consumer), a fix was deployed via Trend Micro's ActiveUpdate (AU) on May 19, 2022, and any user with an active internet connection should receive the update shortly if they have not yet already received it," the antivirus vendor added.
DLL hijacking bugs in multiple security products
The Moshen Dragon group also reportedly abused similar bugs in security products from Bitdefender, McAfee, Symantec, and Kaspersky to install Impacket, a Python kit designed for lateral movement and remote code execution via Windows Management Instrumentation (WMI).
Impacket also has credential-stealing capabilities powered by an open-source tool used to capture the details of password change events on a domain
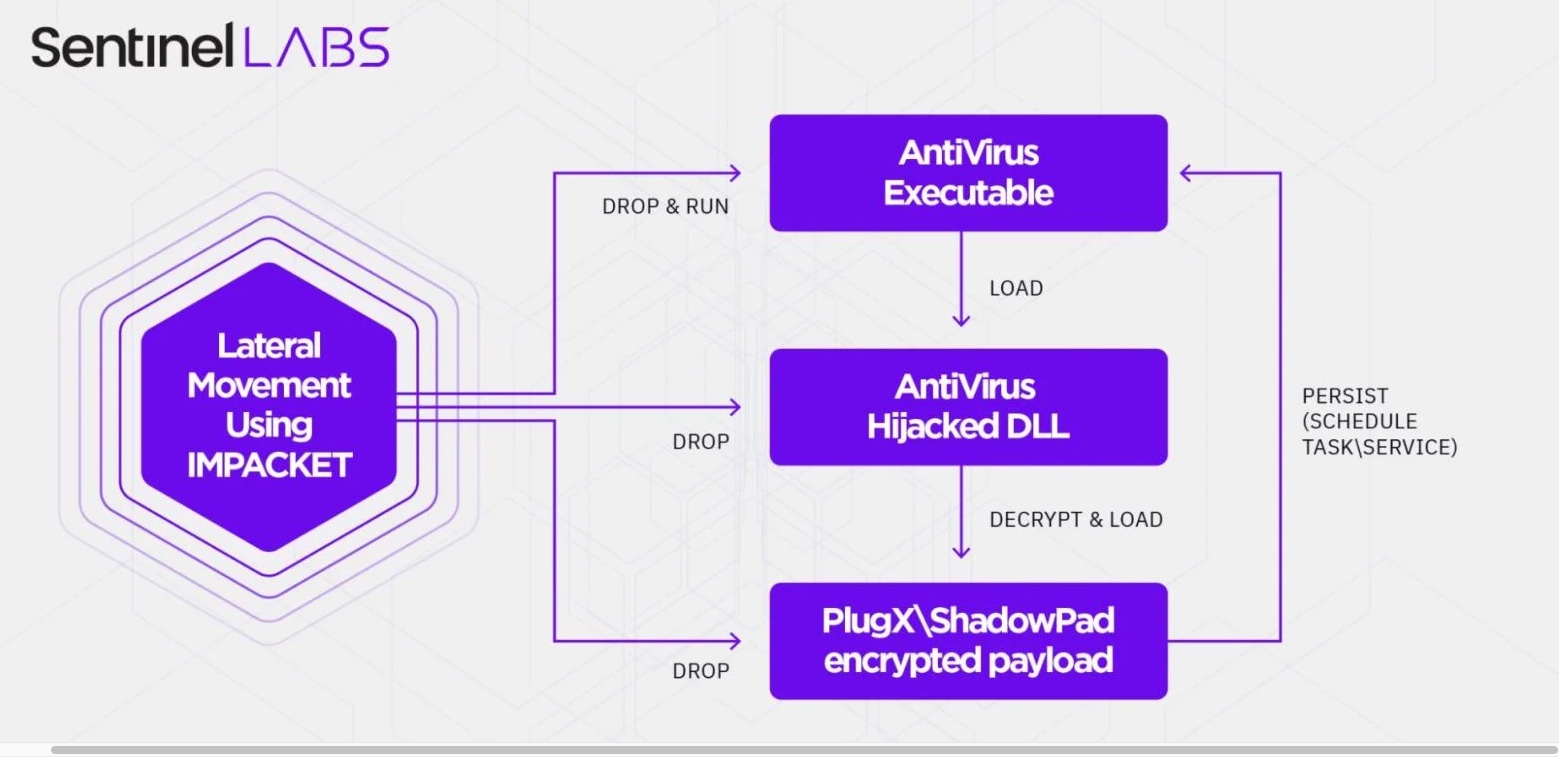
According to Sentinel Labs, the final payloads dropped by the Moshen Dragon operators include variants of PlugX and ShadowPad, two backdoors used by multiple Chinese APTs in recent years.
The threat actors have used these tactics to target telecommunication service providers in Central Asia with the end goal of exfiltrating data from as many systems as possible.
While Trend Micro has published an advisory detailing the mitigation measures taken to stop Moshen Dragon from abusing its security products for malicious products, the other vendors are yet to confirm if their products have been affected and if the bugs have been patched.
BleepingComputer has reached out to spokespersons from McAfee and Symantec for comment but has yet to receive a reply.
Update May 2, 15:06 EDT: Steve Fiore, Bitdefender's Senior Director for Global Public Relations, told BleepingComputer after the article was published that the company's customers are protected against DLL Search Order Hijacking attacks and there was no need to issue a security advisory.
Adversaries use DLL Search Order Hijacking to execute malicious payloads by taking control of the search order used to load dynamic-link libraries. The most serious result using this technique would be adversaries using antivirus to bypass file execution restrictions and gain privilege escalation.
This is not the case with Bitdefender, we have no information pertaining to our installed product being compromised by the threat actor, our customers and partners are protected from privilege escalation in this campaign. Bitdefender is not vulnerable to these types of attacks. We employ technology called Self-Protect as an added security layer to guard our product data (files, registries etc.). Even if an attacker discovers an unknown vulnerability, they are denied access to external non-Bitdefender processes preventing exploitation.
The second DLL Search Order Hijacking attack vector adversaries commonly use involves using antivirus as a masking technique for inserting malicious code using digitally signed binaries to gain trust from the target system. Customers and partners running the latest version of Bitdefender products are protected. We did not issue a security advisory because it was not needed – we answered questions directly if asked by a customer.
Update May 25, 17:04 EDT: Kaspersky says that none of the products in its current lineup were affected and that Moshen Dragon used a legacy, 10-year-old executable part of Kaspersky Anti-Virus 2013 in these attacks.
We have no information about our solutions being compromised. Our customers are protected. Our solutions’ self-defense mechanisms protect against DLL hijacking attacks and additionally we detect such malicious activity with Behavior Detection component as PDM:Trojan.Win32.Generic.
According to the data from the specified article, the attackers used a technique called DLL Side-Loading. A typical scenario used by adversaries to implement such technique is to put some trusted signed executable to the compromised host together with a malicious library which mimics one of the legitimate DLLs used by the mentioned executable. Attackers then run the executable, which loads the DLL invoking malicious payload in the context of this legitimate executable. This technique is commonly used for privilege escalation and defense evasion purposes. In this case attackers used an executable from 10 years old version of Kaspersky Anti-Virus 2013.
We implemented protection measures against this type of attacks years ago. Modern versions of our solutions are not susceptible to this technique. We have self-defense technologies which protect our solutions against this and other types of attacks involving DLL hijacking.
We have not published a security advisory since the executable that was used in the attack is a part of a solution that have reached End of Life in 2018.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now