
Cloudflare says some of its employees' credentials were also stolen in an SMS phishing attack similar to the one that led to Twilio's network being breached last week.
However, although the attackers got their hands on Cloudflare employees' accounts, they failed to breach its systems after their attempts to log in using them were blocked since they didn't have access to their victims' company-issued FIDO2-compliant security keys.
"Around the same time as Twilio was attacked, we saw an attack with very similar characteristics also targeting Cloudflare's employees," Cloudflare explained on Tuesday.
"While individual employees did fall for the phishing messages, we were able to thwart the attack through our own use of Cloudflare One products, and physical security keys issued to every employee that are required to access all our applications.
"While the attacker attempted to log in to our systems with the compromised username and password credentials, they could not get past the hard key requirement."
As Cloudflare also revealed, after entering their credentials on the phishing pages, AnyDesk remote access software was automatically downloaded on their computers to allow the threat actors to take control of their computers remotely if installed.
The phishing messages sent to 76 employees and their families from T-Mobile phone numbers redirected the targets to a Cloudflare Okta login page clone hosted on the cloudflare-okta[.]com domain.
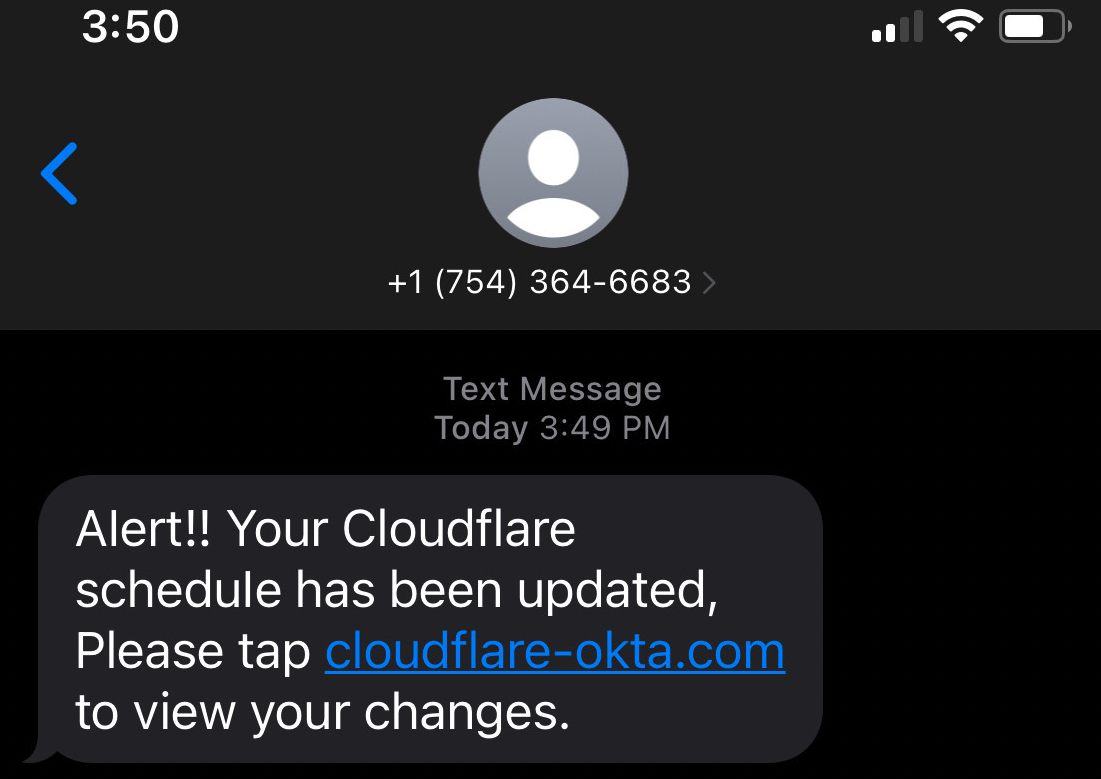
This domain was registered via the Porkbun domain registrar, also used to register web domains used to host landing pages seen in the Twilio attack.
The company took multiple measures in response to this attack, including to:
- Block the phishing domain using Cloudflare Gateway
- Identify all impacted Cloudflare employees and reset compromised credentials
- Identify and take down threat-actor infrastructure
- Update detections to identify any subsequent attack attempts
- Audit service access logs for any additional indications of attack
Cloud communications company Twilio, the owner of the highly popular two-factor authentication (2FA) provider Authy, disclosed a similar attack this week.
Unlike Cloudflare, the company said the attackers were able to access some of its customers' data after breaching internal systems using stolen employee credentials in an SMS phishing attack.
Twilio also revealed that it coordinated its incident response efforts with other companies targeted by similar attacks around the same time.
"We have heard from other companies that they, too, were subject to similar attacks, and have coordinated our response to the threat actors – including collaborating with carriers to stop the malicious messages, as well as their registrars and hosting providers to shut down the malicious URLs," Twilio said.
"Despite this response, the threat actors have continued to rotate through carriers and hosting providers to resume their attacks."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now