
A threat actor known as ‘Blue Mockingbird’ targets Telerik UI vulnerabilities to compromise servers, install Cobalt Strike beacons, and mine Monero by hijacking system resources.
The flaw leveraged by the attacker is CVE-2019-18935, a critical severity (CVSS v3.1: 9.8) deserialization that leads to remote code execution in the Telerik UI library for ASP.NET AJAX.
The same threat actor was seen targeting vulnerable Microsoft IIS servers that used Telerik UI in May 2020, by which time a year had passed since security updates were made available by the vendor.
Blue Mockingbird is seemingly leveraging the same flaw to launch new cyberattacks, with Sophos researchers reporting today on incidents involving tactics closely resembling those previously used by the threat actor.
Exploiting old bugs
To exploit CVE-2019-18935, the attackers must acquire the encryption keys that protect Telerik UI’s serialization on the target. This is possible either by exploiting another vulnerability in the target web app or using CVE-2017-11317 and CVE-2017-11357.
There are still valid targets available for exploitation because many web apps were projects that embedded the Telerik UI framework version available at the time of their development and then were discontinued or forgot all about it.
Once the keys are acquired, the attackers can compile a malicious DLL containing the code to be executed during deserialization and run it within the context of the ‘w3wp.exe’ process.
In the recent attacks spotted by Sophos, Blue Mockingbird employs a readily available proof-of-concept (PoC) exploit, which handles the encryption logic and automates the DLL compilation.
.png)
Financially-motivated attacks
The payload used in the recent attacks is a Cobalt Strike beacon, a stealthy, legitimate penetration testing tool Blue Mockingbird abuses for executing encoded PowerShell commands.
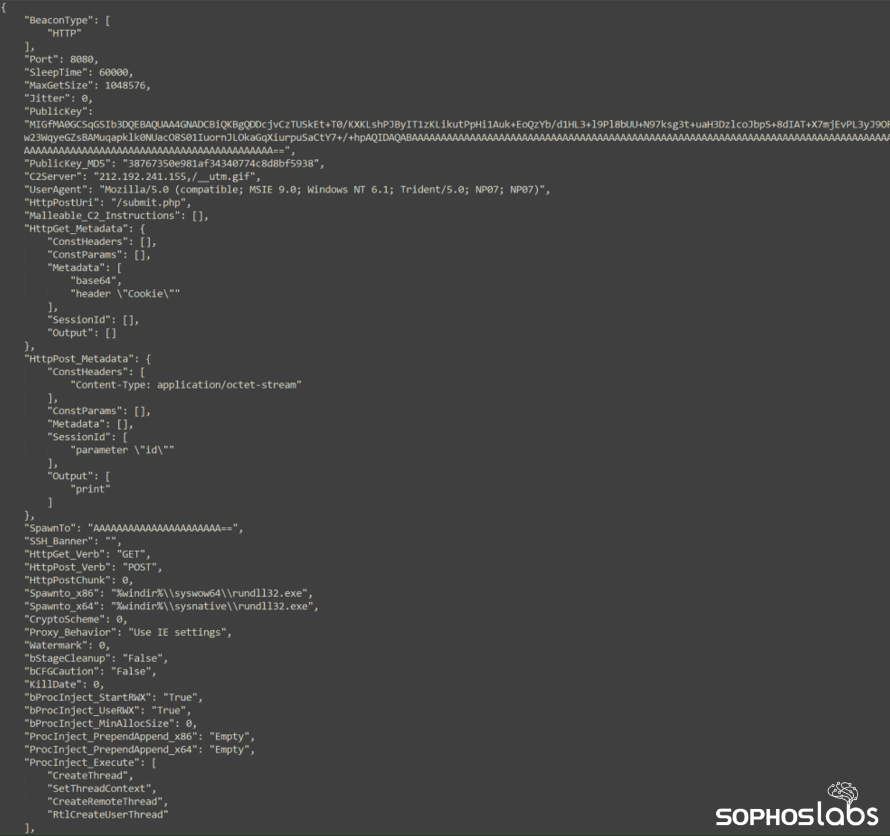
Persistence is established via Active Directory Group Policy Objects (GPOs), which create scheduled tasks written in a new registry key containing base64-encoded PowerShell.
.png)
The script uses common AMSI-bypassing techniques to evade Windows Defender detection to download and load a Cobalt Strike DLL onto memory.
The second-stage executable (‘crby26td.exe’) is an XMRig Miner, a standard open-source cryptocurrency miner used for mining Monero, one of the least traceable crypto coins.
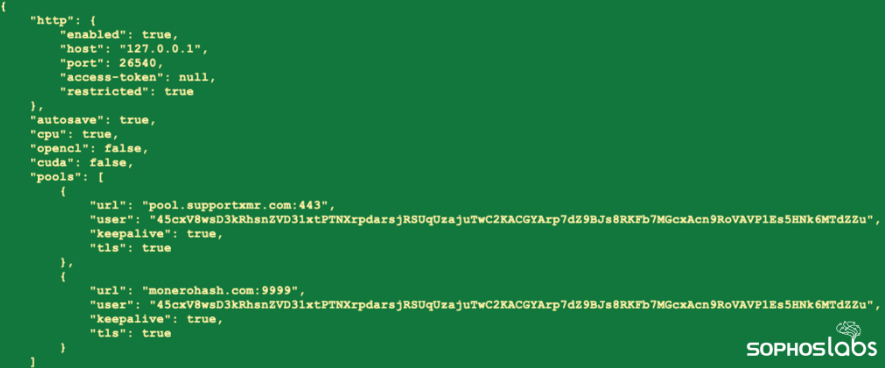
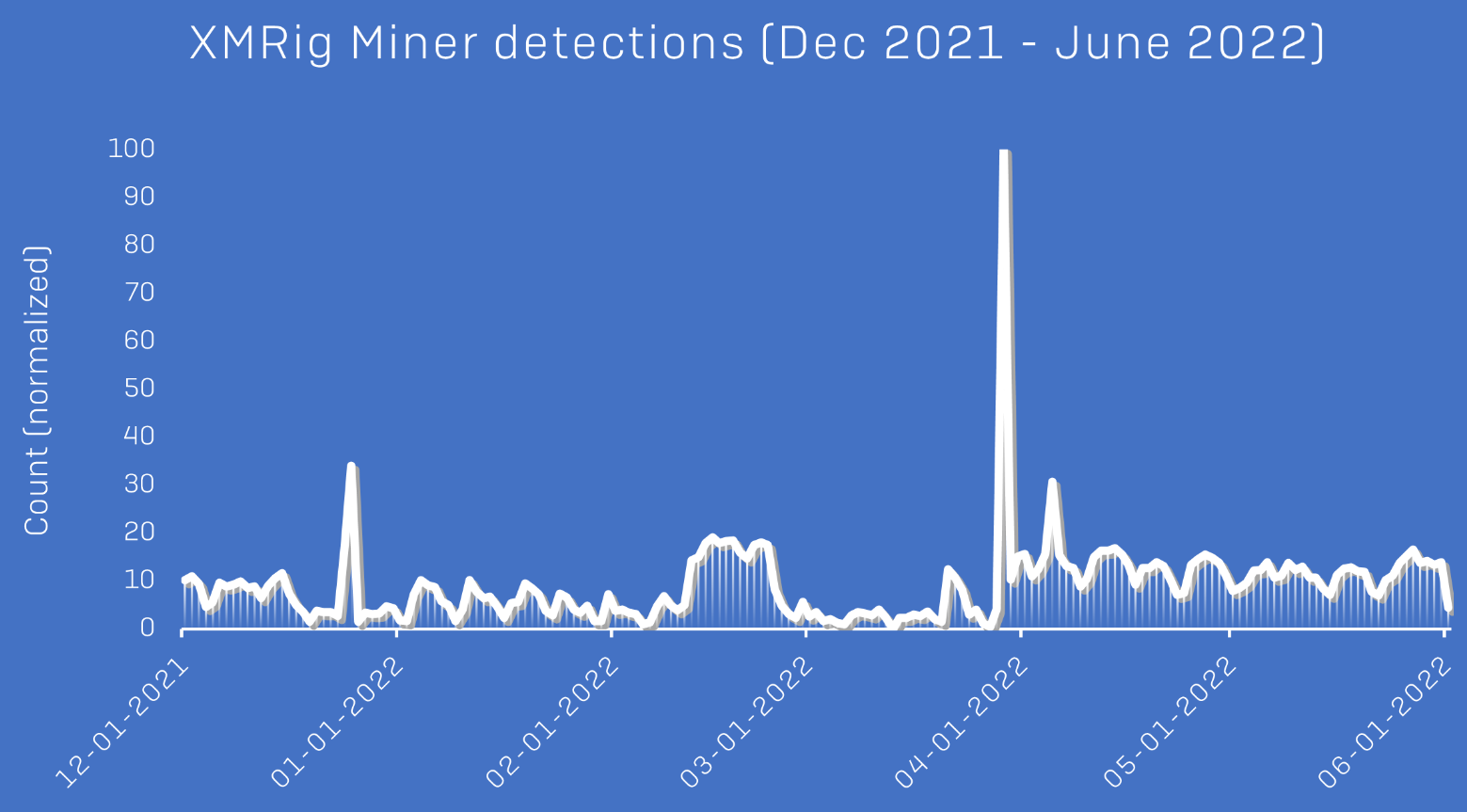
Notably, this was the main goal of the threat actor’s 2020 campaign, so not much has changed in the whole attack chain, techniques, and goals.
However, the deployment of Cobalt Strike opens the way to easy lateral movement within the compromised network, data exfiltration, account takeover, and deployment of more potent payloads such as ransomware.
Whether or not Blue Mockingbird is interested in exploring these scenarios remains to be seen, but for now, they’re exclusively occupied with Monero mining.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now