
Image: Ax Sharma
The University of Manchester finally confirmed that attackers behind a cyberattack disclosed in early June had stolen data belonging to alums and current students.
The university first disclosed the attack on June 9, warning that data was likely stolen but said the incident was unrelated to the MOVEit Transfer data theft attacks.
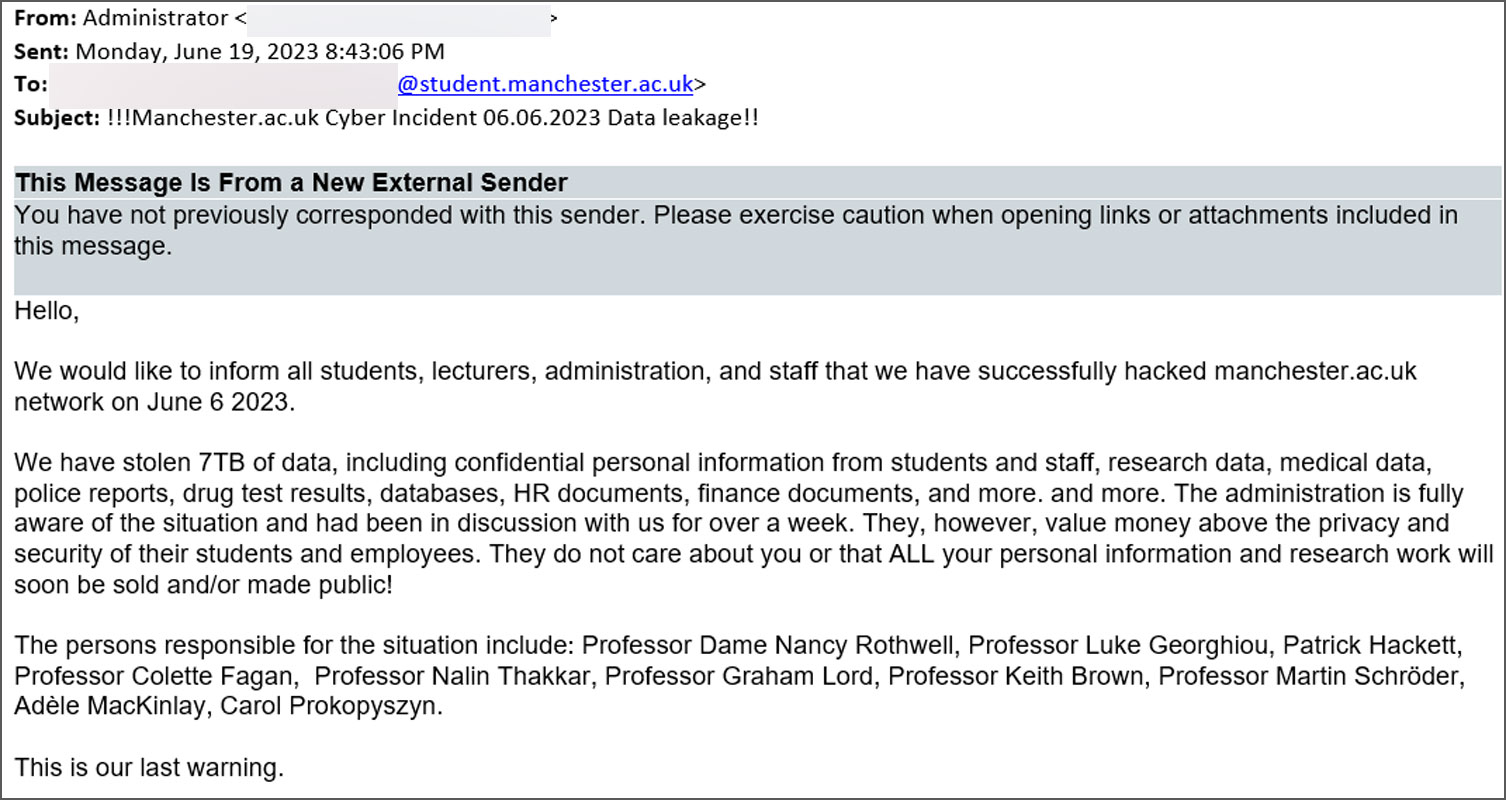
On Tuesday, BleepingComputer first reported that the hackers behind the attack were emailing students claiming to have stolen 7 TB of confidential data belonging to students and staff.
"We would like to inform all students, lecturers, administration, and staff that we have successfully hacked manchester.ac.uk network on June 6 2023," the threat actors said in the email.
"We have stolen 7TB of data, including confidential personal information from students and staff, research data, medical data, police reports, drug test results, databases, HR documents, finance documents, and more. and more."
BleepingComputer contacted the University of Manchester regarding these emails but has yet to receive a response.
However, the University of Manchester has now confirmed that data was indeed stolen in the incident from a system used to help manage students' university accommodation.
"Based on our investigations we believe that a small proportion of data has been copied that relates to some students, and some alumni. We have written directly to those individuals who may have been affected by this," the university said.
"We understand that this will create concern for some, but we would like to assure our community that our internal and external experts are working around the clock to continue to address this and our investigations are continuing."
According to an update to the cyberattack information page, the attackers accessed the following types of sensitive data:
- Names and contact details (address, telephone numbers, and email address)
- University ID numbers
- Dates of birth and gender
- Nationality, domicile, and ethnicity
- UCAS number and fee status
- UCAS disability code (where relevant)
- For some students, the documents also included a summary of key communications or other records relating to their university accommodation.
Some former students also had their names, contact details, University ID numbers, gender, dates of birth, and basic program information.
"We have not identified any unauthorised access to bank account or card payment details – we do not store such information on the above systems," the university said.
"We are asking all staff and students to remain vigilant of any suspicious emails, including those that appear to come from those responsible for this incident. Do not engage with or reply to these emails in any way."
The university said it's collaborating with relevant authorities to investigate the incident, including the Information Commissioner's Office, the National Cyber Security Centre (NCSC), the National Crime Agency, and other regulatory bodies.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now