
Malicious NPM packages pretending to be Roblox libraries are delivering ransomware and password-stealing trojans on unsuspecting users.
The two NPM packages are named noblox.js-proxy and noblox.js-proxies, and use typo-squatting to pretend to be the legitimate Roblox API wrapper called noblox.js-proxied by changing a single letter in the library's name.
In a new report by open source security firm Sonatype with further analysis by BleepingComputer, these malicious NPMs are infecting victims with an MBRLocker ransomware that impersonates the notorious GoldenEye ransomware, trollware, and a password stealing trojan.
Both of the malicious NPM libraries have since been taken down and are no longer available.
A mess of malicious activity
After the malicious NPM libraries are added to a project and launched, the library will execute a postinstall.js script. This script is normally used to execute legitimate commands after a library is installed, but in this case, it starts a chain of malicious activity on victims' computers.
As you can see below, the postinstall.js script is heavily obfuscated to prevent analysis by security researchers and software.
When executed, the script will launch the heavily obfuscated batch file called 'nobox.bat,' shown below.
This batch file was decoded by Sonatype security researcher Juan Aguirre and will download a variety of malware from Discord and launches them with the help of the fodhelper.exe UAC bypass
The files downloaded by the noblox.bat batch file are listed below in the order they are installed, along with their VirusTotal links and a description of their actions.
- exclude.bat - Adds a Microsoft Defender exclusion not to scan files under the C:\ drive.
- legion.exe - Deploys a password-stealing trojan that steals browser history, cookies, saved passwords, and attempts to record video via the built-in webcam.
- 000.exe - Trollware that modifies the current user's name to 'UR NEXT,' plays videos, changes a user's password, and attempts to lock them out of their system.
- tunamor.exe - Installs an MBRLocker called 'Monster Ransomware,' which impersonates the GoldenEye ransomware.
The Monster ransomware MBRLocker
Of particular interest is the 'tunamor.exe' executable, which installs an MBRLocker calling itself 'Monster Ransomware.'
When executed, the ransomware will perform a forced restart of the computer and then display a fake CHKDSK of the system. During this process, the ransomware is allegedly encrypting the disks on the computer.
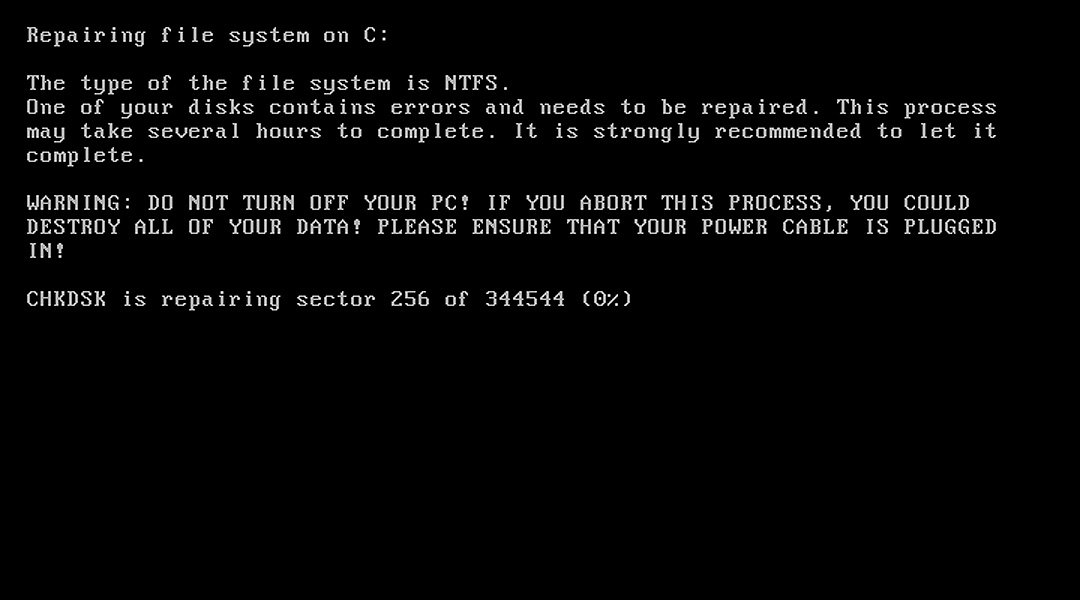
Source: BleepingComputer
When finished, it will reboot the computer and display a skull and crossbones lock screen originally found in the Petya/ GoldenEye ransomware families.
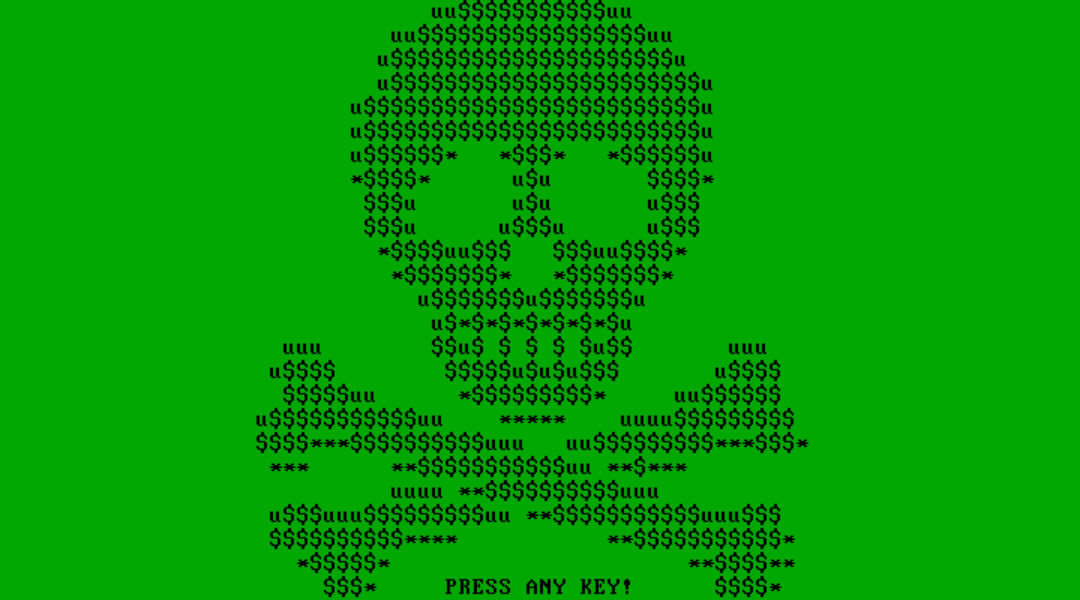
Source: BleepingComputer
After pressing enter, the victim is shown a screen stating that their hard disks are encrypted and that they must visit the http://monste3rxfp2f7g3i.onion/ Tor site, which is now down, to pay a ransom.
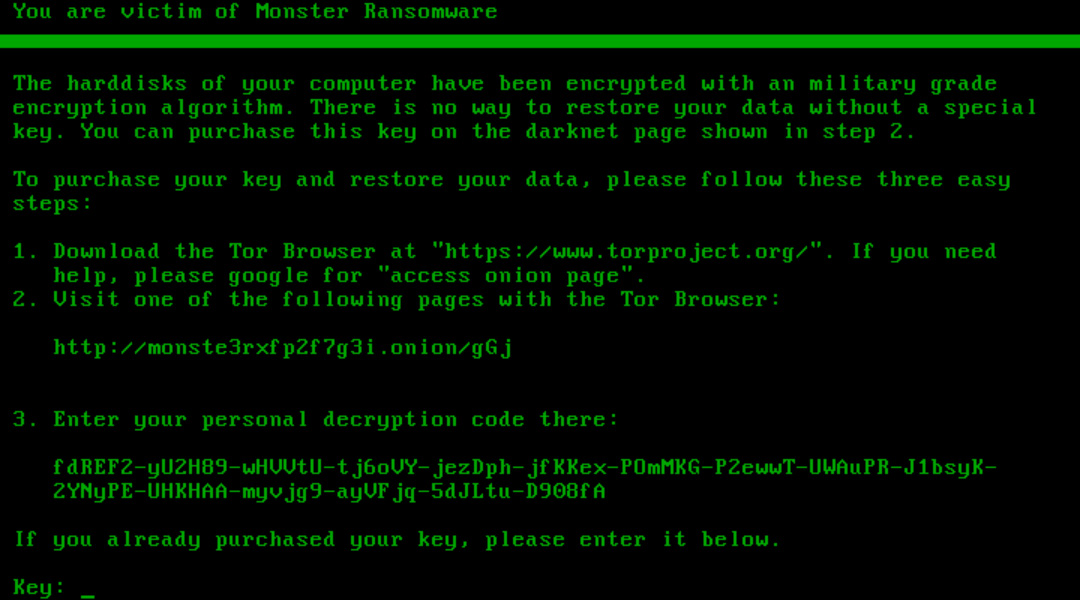
Source: BleepingComputer
BleepingComputer discovered the 'qVwaofRW5NbLa8gj' string, which is accepted as a valid key to decrypt the computer. However, while the key is accepted and the ransomware states it is decrypting the computer, Windows will fail to start afterward.
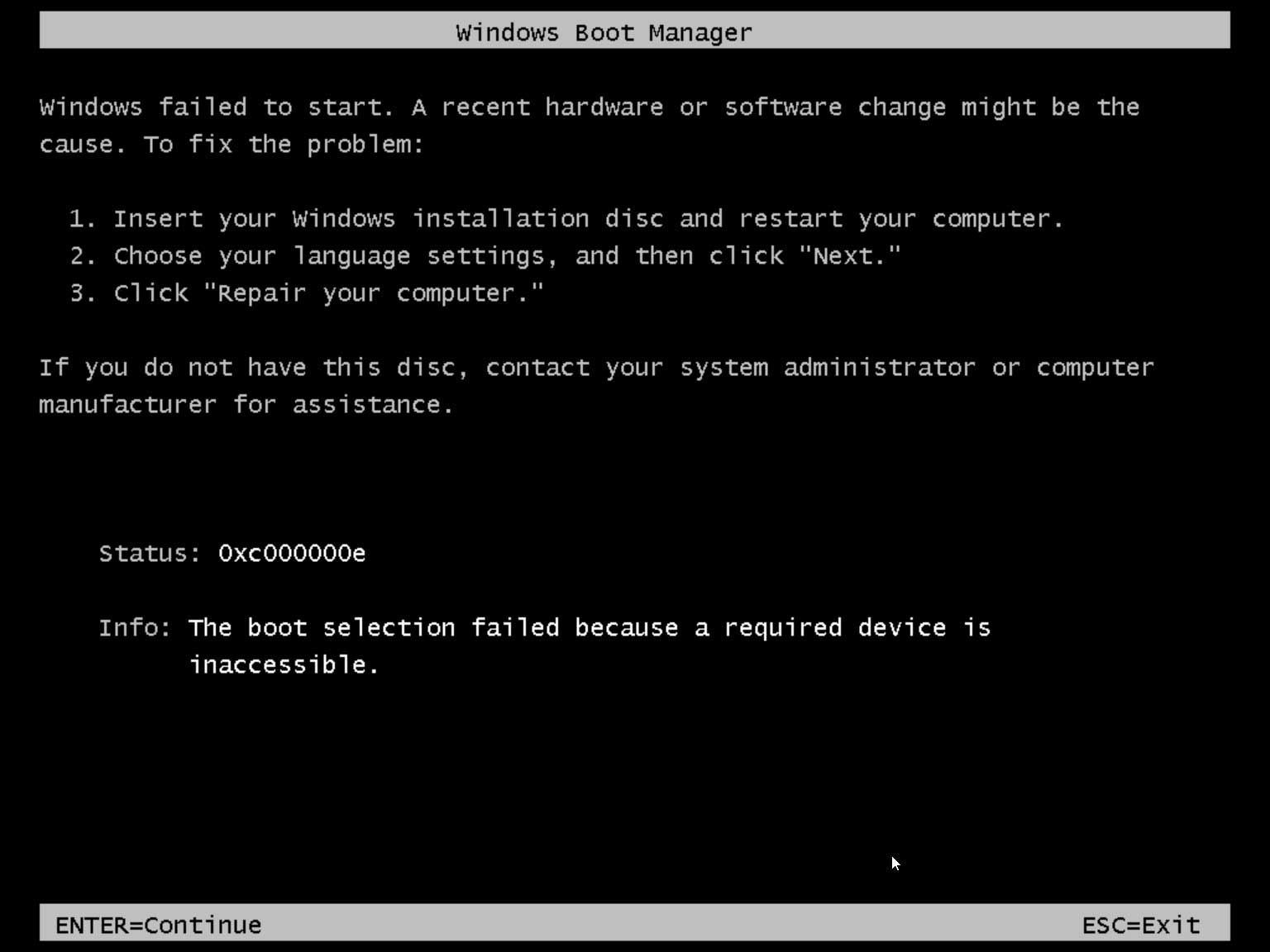
Source: BleepingComputer
It is unclear if an additional string must be added to that key to decrypt the hard disk's drive correctly or if this program is simply a wiper designed to destroy systems.
This ransomware does not appear to be widespread and is only known to be distributed via these NPM packages.
Based on the activity of the 000.exe trollware and the strange behavior of the Monster ransomware, it is likely that these packages are designed to destroy a system rather than generate a ransom demand.
Malicious NPMs used in supply-chain attacks, such as this one, are becoming more common.
Sonatype recently discovered three malicious NPM libraries used to deploy cryptominers on Linux and Windows devices.
Last Friday, the very popular UA-Parser-JS NPM library was hijacked to infect users with miners and password stealing trojans.
IOCS
Exclude.bat
0419582ea749cef904856dd1165cbefe041f822dd3ac9a6a1e925afba30fe591
Legion.exe
a81b7477c70f728a0c3ca14d0cdfd608a0101cf599d31619163cb0be2a152b78
Password stealer
f4fb42c8312a6002a8783e2a1ab4571eb89e92cd192b1a21e8c4582205c37312
000.exe
4a900b344ef765a66f98cf39ac06273d565ca0f5d19f7ea4ca183786155d4a47
tunamor.exe (ransomware)
78972cdde1a038f249b481ea2c4b172cc258aa294440333e9c46dcb3fbed5815



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now