
GitHub has announced on Monday that it expanded its code hosting platform's secrets scanning capabilities for GitHub Advanced Security customers to block secret leaks automatically.
Secret scanning is an advanced security option that organizations using GitHub Enterprise Cloud with a GitHub Advanced Security license can enable for additional repository scanning.
It works by matching patterns defined by the organization or provided by partners and service providers. Each match is reported as a security alert in the repos' Security tab or to partners if it matches a partner pattern.
Automatically blocks accidental secrets exposure
The new feature, known as push protection, is designed to prevent accidental exposure of credentials before committing code to remote repositories.
This new capability embeds secret scanning within the developers' workflow, and it works with 69 token types (API keys, authentication tokens, access tokens, management certificates, credentials, private keys, secret keys, and more) detectable with a low "false positive" detection rate.
"With push protection, GitHub will check for high-confidence secrets as developers push code and block the push if a secret is identified," GitHub said.
"To make this possible without disrupting development productivity, push protection only supports token types that can be detected accurately."
If GitHub Enterprise Cloud identifies a secret before pushing the code, the git push is blocked to allow the developers to review and remove the secrets from the code they tried to push to remote repos.
The developers also can tag these security alerts as false positives, test cases, or mark them to be fixed later.
How to enable secret scanning push protection
Organizations with GitHub Advanced Security can enable the secret scanning push protection feature at both repository and organization levels via the API or with just one click from the user interface.
The detailed procedure for enabling push protection for your organization requires you to:
- On GitHub.com, navigate to the main page of the organization.
- Under your organization name, click Settings.
- In the "Security" section of the sidebar, click Code security and analysis.
- Under "Code security and analysis," find "GitHub Advanced Security."
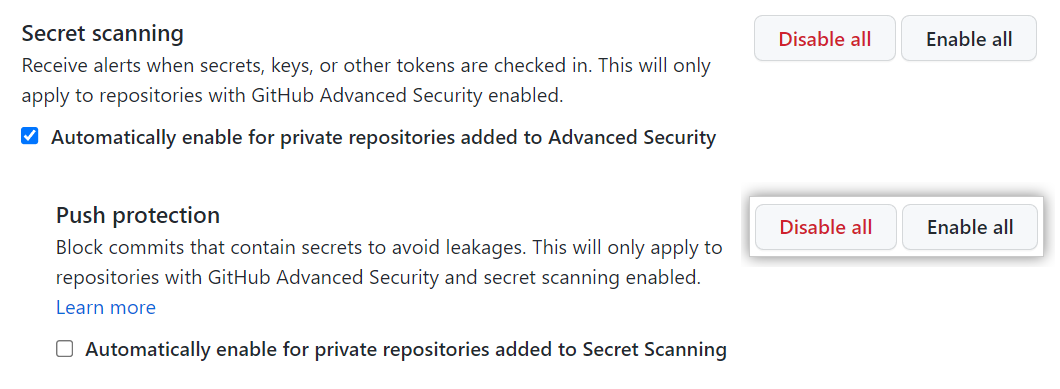
- Under "Secret scanning," under "Push protection," click Enable all.
- Optionally, click "Automatically enable for private repositories added to secret scanning."
You can also enable it for single repositories by toggling it on from the repo's Settings > Security & analysis > GitHub Advanced Security dialog.
You can find more information about the secret scanning capabilities from here and additional details on how to use push protection from the command line or allow some secrets to be pushed from here.
"To date, GitHub has detected more than 700,000 secrets across thousands of private repositories using secret scanning for GitHub Advanced Security; GitHub also scans for our partner patterns across all public repositories (for free)," GitHub added.
"Today, we’re adding the option for GitHub Advanced Security customers to prevent leaks from happening altogether by scanning for secrets before a git push is accepted."
As BleepingComputer previously reported [1, 2, 3], exposed credentials and secrets have led to high-impact breaches.
Therefore, enabling automated secrets scanning before committing your code will take organizations one step closer to safeguarding themselves from accidental leaks and increasing supply-chain security.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now