
A new ransomware operation has been launched under the name 'Lilith,' and it has already posted its first victim on a data leak site created to support double-extortion attacks.
Lilith is a C/C++ console-based ransomware discovered by JAMESWT and designed for 64-bit versions of Windows. Like most ransomware operations launching today, Lilith performs double-extortions attacks, which is when the threat actors steal data before encrypting devices.
According to a report by researchers at Cyble who analyzed Lilith, the new family doesn't introduce any novelties. However, it's one of the latest threats to watch out for, along with RedAlert and 0mega that also recently emerged.
A look at Lilith
Upon execution, Lilith attempts to terminate processes that match entries on a hardcoded list, including Outlook, SQL, Thunderbird, Steam, PowerPoint, WordPad, Firefox, and more.
This frees up valuable files from applications that may be using them at the moment, thus making them available for encryption.
Before the encryption process is initiated, Lilith creates and drops ransom notes on all the enumerated folders.
The note gives the victims three days to contact the ransomware actors on the provided Tox chat address, or they are threatened with public data exposure.
.png)
The file types excluded from encryption are EXE, DLL, and SYS, while Program Files, web browsers, and the Recycle Bin folders are also bypassed.
Interestingly, Lilith also contains an exclusion for 'ecdh_pub_k.bin,' which stores the local public key of BABUK ransomware infections.
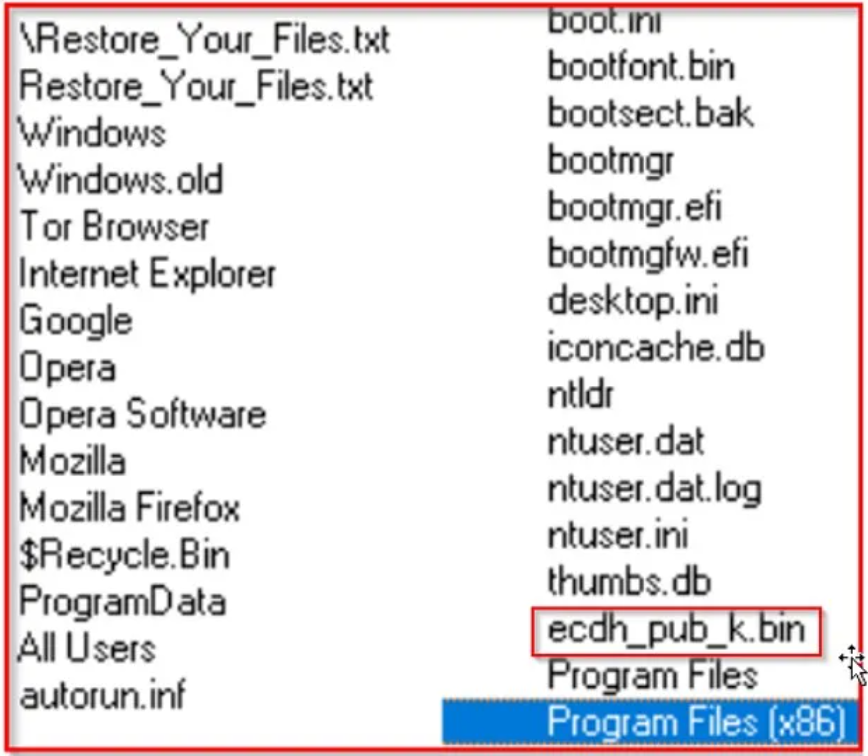
This might be a remnant from copied code, so it could be an indication of a link between the two ransomware strains.
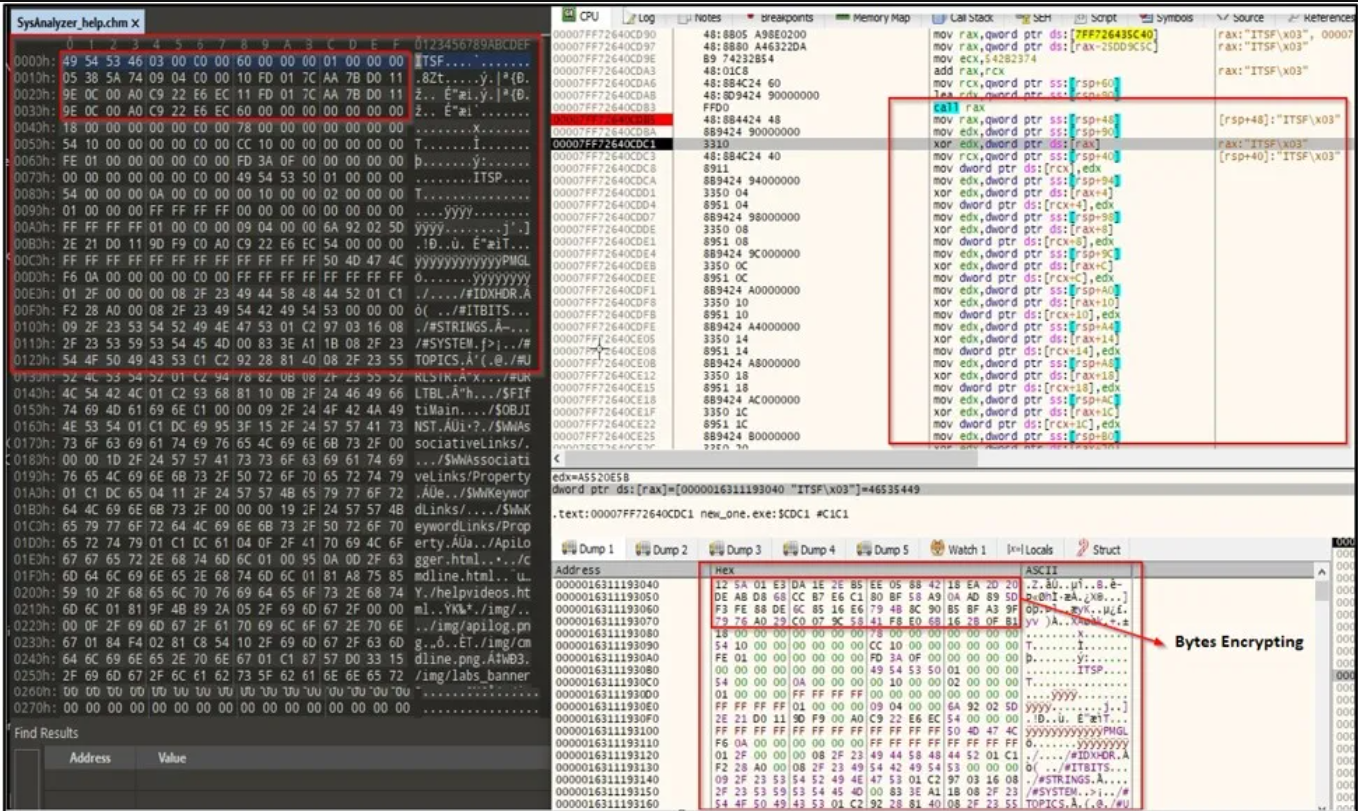
Finally, the encryption takes place using Windows cryptographic API, while the Windows’ CryptGenRandom function generates the random key.
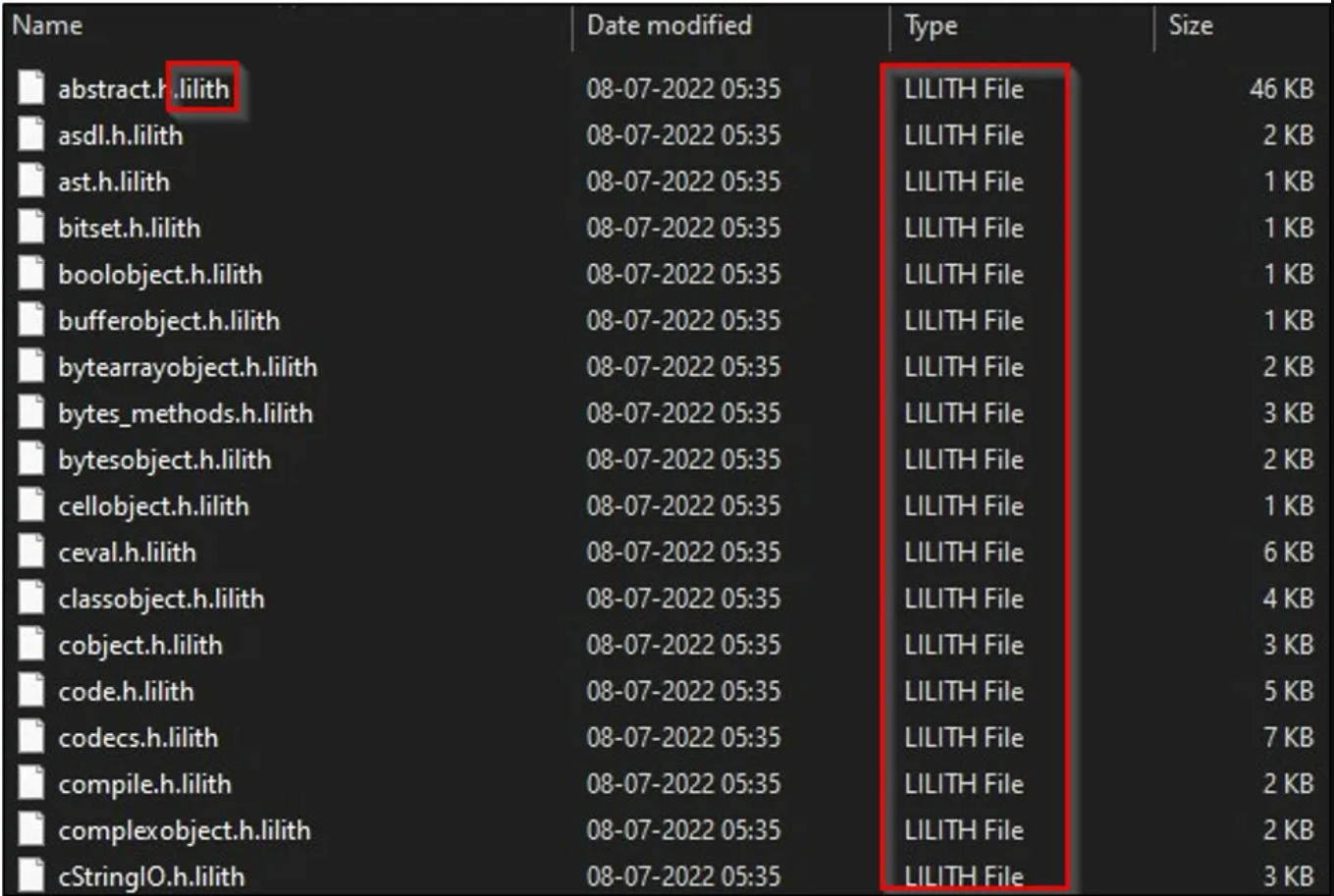
The ransomware appends the ".lilith" file extension when encrypting files, as shown below.
What to expect
While it's too early to tell if Lilith could develop into a large-scale threat or a successful RaaS program, it's something analysts should keep an eye on.
Its first victim, which has been removed from the extortion site at the time of writing this, was a large construction group based in South America.
This is a sign that Lilith might be interested in big-game hunting and that its operators are already aware of the political labyrinths they need to navigate to avoid being targeted by law enforcement.
After all, most of these novel ransomware projects are rebrands of older programs, so their operators typically know the intricacies of the field very well.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now