
An ongoing worldwide campaign is pushing new malware dubbed MosaicLoader camouflaged as cracked software via search engine advertising to infect wannabe software pirates' systems.
MosaicLoader is a malware downloader designed by its creators to deploy more second-stage payloads on infected systems, as Bitdefender researchers revealed in a report published today and shared with BleepingComputer last week.
"We named it MosaicLoader because of the intricate internal structure that aims to confuse malware analysts and prevent reverse-engineering," Janos Gergo Szeles, Senior Security Researcher at Bitdefender, revealed.
During their investigation, Bitdefender found that MosaicLoader threat actors used the following tactics to hinder researchers' malware analysis efforts and to increase their attacks' rate of success:
- Mimicking file information that is similar to legitimate software
- Code obfuscation with small chunks and shuffled execution order
- Payload delivery mechanism infecting the victim with several malware strains
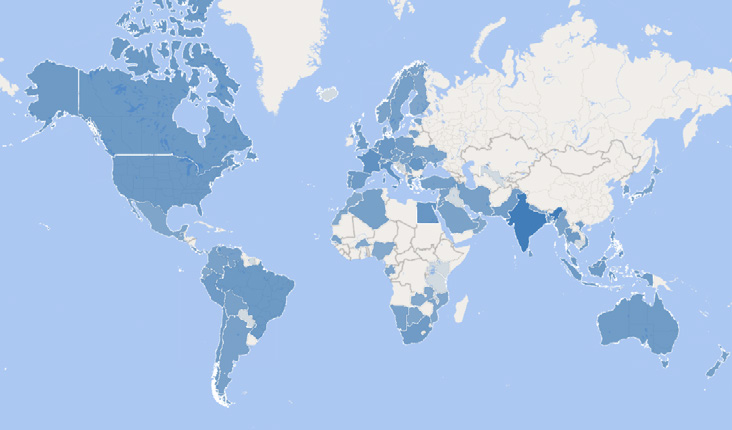
The researcher added that the campaign doesn't target a specific region. Due to its online advertising lures, it will attempt to infect any search engine users looking to download and install cracked software installers on their devices.
The attackers are camouflaging their droppers as executables belonging to legitimate software, using similar icons and including info such as company names and descriptions within the files' metadata info to pass superficial scrutiny.
After being deployed on a victim's system, MosaicLoader downloads additional malware ranging from cryptocurrency miners and cookie stealers to Remote Access Trojans (RATs) and backdoors using "a complex chain of processes."
To add to the danger of getting your system infected with MosaicLoader, the threat actors (or their clients) can harvest sensitive info such as credentials from compromised systems using RATs and similar malware with data theft capabilities.
The stolen info can later be used to hijack victims' online accounts and use the gained access in identity theft scams or blackmail scams.
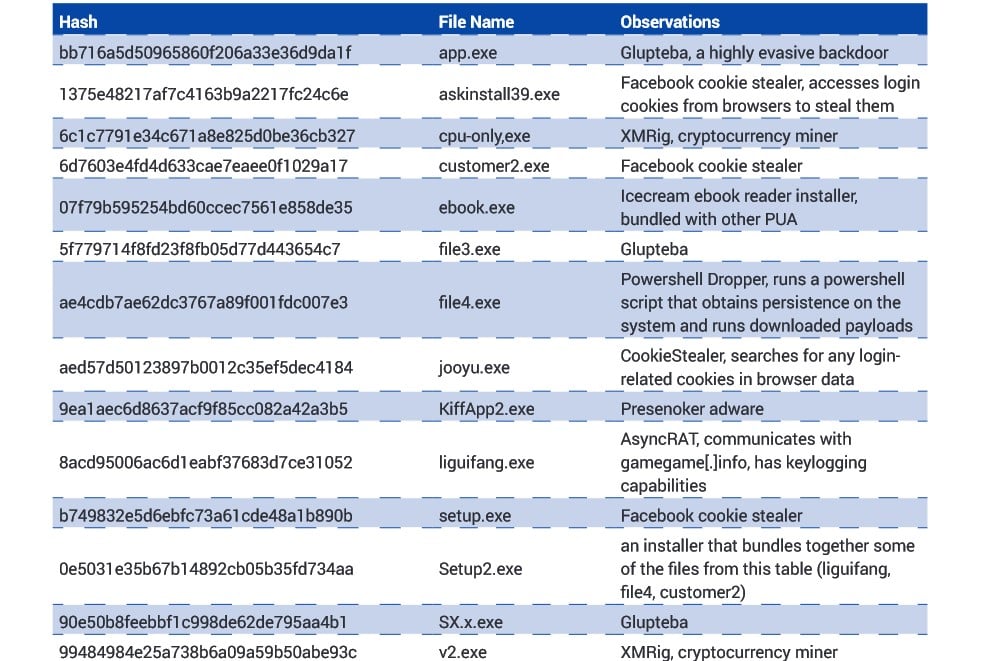
Bitdefender collected and analyzed multiple malware samples delivered by MosaicLoader via a malware sprayer that downloads further payloads from attacker-controlled domains hosting lists of URLs hosting malware (some of them are listed in the table embedded below).
"The best way to defend against MosaicLoader is to avoid downloading cracked software from any source," Szeles concluded.
"Besides being against the law, cybercriminals look to target and exploit users searching for illegal software."
Additional technical info and indicators of compromise, including malware hashes and command-and-control infrastructure info, can be found at the end of Bitdefender's whitepaper.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now