
The widespread malware known as Qbot (aka Qakbot or QuakBot) has recently returned to light-speed attacks, and according to analysts, it only takes around 30 minutes to steal sensitive data after the initial infection.
According to a new report by The DFIR Report, Qbot was performing these quick data-snatching strikes back in October 2021, and it now appears that the threat actors behind it have returned to similar tactics.
More specifically, the analysts report that it takes half an hour for the adversaries to steal browser data and emails from Outlook and 50 minutes before they jump to an adjacent workstation.
The timeline of an attack
As shown in the following diagram from the researcher's report, Qbot moves quickly to perform privilege escalation immediately following an infection, while a full-fledged reconnaissance scan takes place within ten minutes.
.jpg)
Source: The DFIR Report
Initial access for Qbot infections is typically achieved via phishing emails with malicious attacks, such as Excel (XLS) documents that use a macro to drop the DLL loader on the target machine.
Historically, BleepingComputer has seen Qbot phishing campaigns use various malicious document templates. For example, one document template pretends to be a warning from "Windows Defender Antivirus," providing instructions on enabling macros.
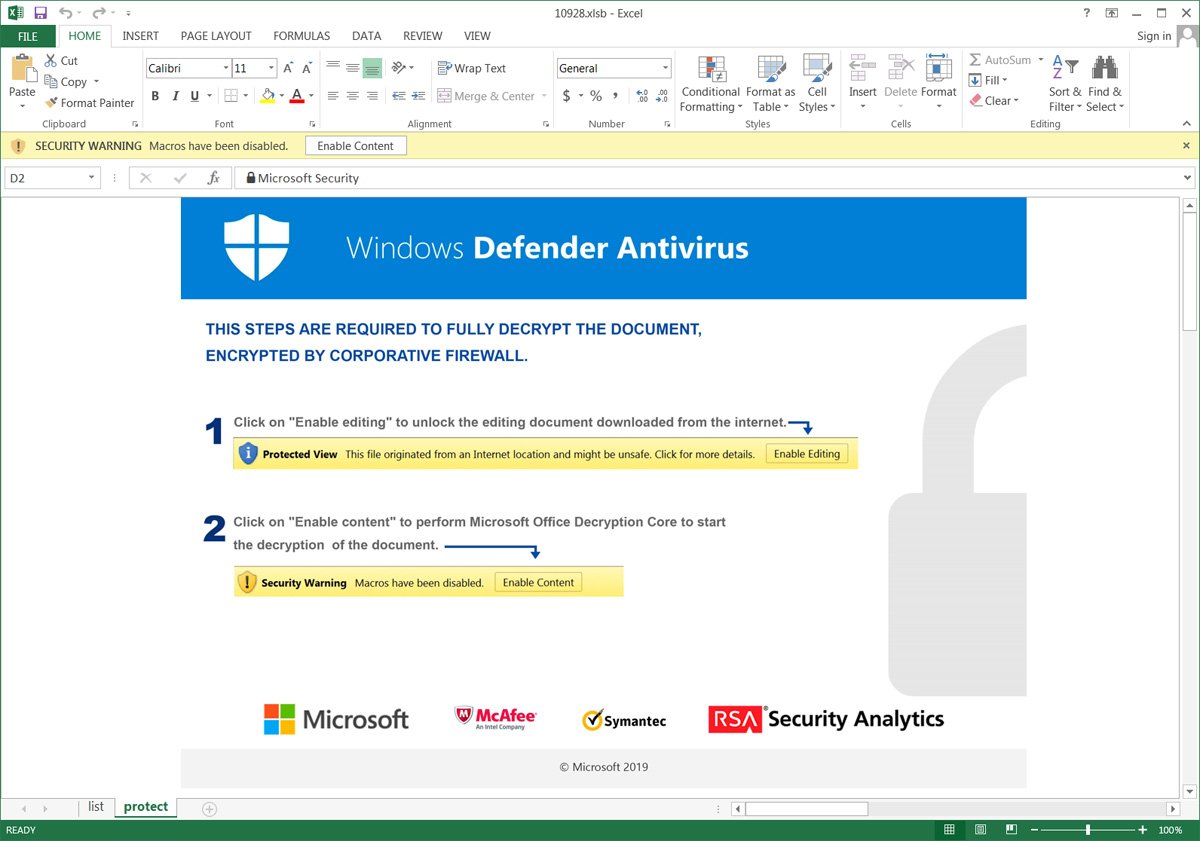
Source: BleepingComputer
When launched, the Qbot DLL payload will be injected and launched into legitimate Windows applications to evade detection, such as MSRA.exe and Mobsync.exe. For example, in The DFIR Report's analysis, Qbot injected into MSRA.exe and then created a scheduled task for privilege elevation.
Additionally, the malware adds the Qbot DLL to Microsoft Defender's exclusion list, so it won't be detected when injection into msra.exe happens.
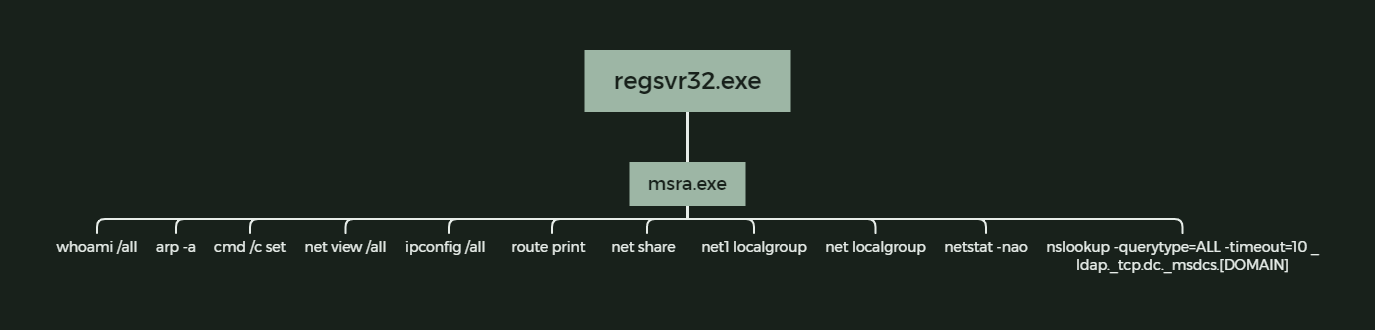
Source: The DFIR Report
The malware steals emails in half an hour after the initial execution, which are then commonly used for future replay-chain phishing attacks.
The researchers note that Qbot will also steal Windows credentials by dumping the memory of the LSASS (Local Security Authority Server Service) process and by stealing from web browsers. These credentials can then be used to spread to other devices on the network laterally.
The DFIR Report states that it only took on average fifty minutes for credentials to be dumped after the malware was first executed.
The lateral movement takes place rapidly, so if there's no network segmentation to protect the workstations, the situation becomes very challenging for defense teams.
The impact of these expeditious attacks isn't limited to data loss, as Qbot has also been observed in the past to drop ransomware payloads onto compromised corporate networks.
Ransomware gangs known to have partnered with Qbot for initial access to corporate networks include REvil, Egregor, ProLock, and MegaCortex.
A versatile infection
A Microsoft report from December 2021 captured the versatility of Qbot attacks, making it harder to evaluate the scope of its infections accurately.
However, no matter how a Qbot infection unfolds precisely, it is essential to keep in mind that almost all begin with an email, so this is the main access point that organizations need to strengthen.
Today's announcement by Microsoft that they will be blocking macros in downloaded documents by default by removing the 'Enable Content' and 'Enable Editing' buttons will go a long way to protecting users from Qbot phishing attacks.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now