
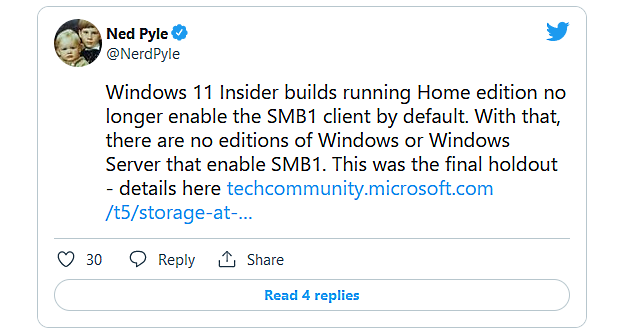
Microsoft announced today that the 30-year-old SMBv1 file-sharing protocol is now disabled by default on Windows systems running the latest Windows 11 Home Dev channel builds, the last editions of Windows or Windows Server that still came with SMBv1 enabled.
Redmond first announced plans to disable SMBv1 in most versions of the Windows operating system in June 2017 after first disabling it for internal builds of Windows 10 Enterprise and Windows Server 2016.
SMBv1 is no longer installed in Microsoft's OS by default since Windows 10 version 1709 and Windows Server version 1709, with newer versions of Windows using SMBv3.
SMBv1 disabled in Windows 11 Home edition Dev builds
"I have a pretty big announcement: we've started the final phase of disabling SMB1 in Windows," said Ned Pyle, Principal Program Manager in the Microsoft Windows Server High Availability and Storage group.
"If you install a Windows Insider Dev channel build in any variant of Home Edition, the SMB1 client isn't installed."
This will also become the default behavior in the next Windows 11 major release after Windows Insiders will be able to test and provide feedback on the new change,
However, as the Microsoft expert further explained, this shift will not affect devices using SMBv1 following in-place upgrades, with admins still allowed to reinstall it.
"I am also announcing that we are going to remove the SMB1 binaries in a future release. Windows and Windows Server will no longer include the drivers and DLLs of SMB1," Pyle added.
"We will provide an out-of-band unsupported install package for organizations or users that still need SMB1 to connect to old factory machinery, medical gear, consumer NAS, etc."
Pyle also shared a list of vendors and products that require SMBv1 so users can avoid them and not get blocked from switching to newer and more secure versions of the SMB protocol.
Those interested in disabling SMBv1 on their servers can check this Microsoft support page for detailed instructions.
SMBv1 warnings
Microsoft has been recommending admins to remove support for SMBv1 on their network since 2016 since it does not feature additional security improvements added to newer versions of the SMB protocol.
These enhancements include pre-authentication integrity checks to prevent man-in-the-middle (MiTM) attacks, encryption, insecure guest authentication blocking, protection against security downgrade attacks, and more.
Two years ago, the Microsoft Exchange Team also urged admins to disable SMBv1 to protect servers from malware attacks.
These warnings came after the 2017 leak of multiple NSA exploits designed to exploit weaknesses in the SMBv1 protocol to execute commands on vulnerable servers with administrative privileges.
Some of these exploits, like EternalBlue and EternalRomance, were later deployed in the wild by TrickBot, Emotet, WannaCry, Retefe, NotPetya, and Olympic Destroyer malware to infect more devices and launch destructive attacks or steal user credentials.



Comments
fromFirefoxToVivaldi - 2 years ago
Finally, one less thing to do after clean install.
povlhp - 2 years ago
They should disable print spooler, or do a complete rewrite. It has been abandonware for so many years, and only gets attention whenever a new exploit is found, and a minimal patch deployed.