
A Chinese-speaking hacking group known as LuoYu is infecting victims WinDealer information stealer malware deployed by switching legitimate app updates with malicious payloads in man-on-the-side attacks.
To do that, the threat actors actively monitor their targets' network traffic for app update requests linked to popular Asian apps such as QQ, WeChat, and WangWang and replace them with WinDealer installers.
Once deployed, WinDealer helps the attackers search for and siphon large amounts of data from compromised Windows systems, install backdoors to maintain persistence, manipulate files, scan for other devices on the network, and run arbitrary commands.
Instead of using the common hard-coded command-and-control (C2) server info, WinDealer will connect to a random ChinaNet (AS4134) IP address from the Xizang and Guizhou provinces out of a pool of 48,000 IP addresses, according to security researchers at Kaspersky who observed this new delivery method.
Since controlling the entirety of these IP ranges is likely impossible, explanations of how LuoYu is capable of this include the use of compromised routers "on the route to (or inside) AS4134," the use of ISP-level law enforcement tools, or "signals intelligence methods unknown to the general public."
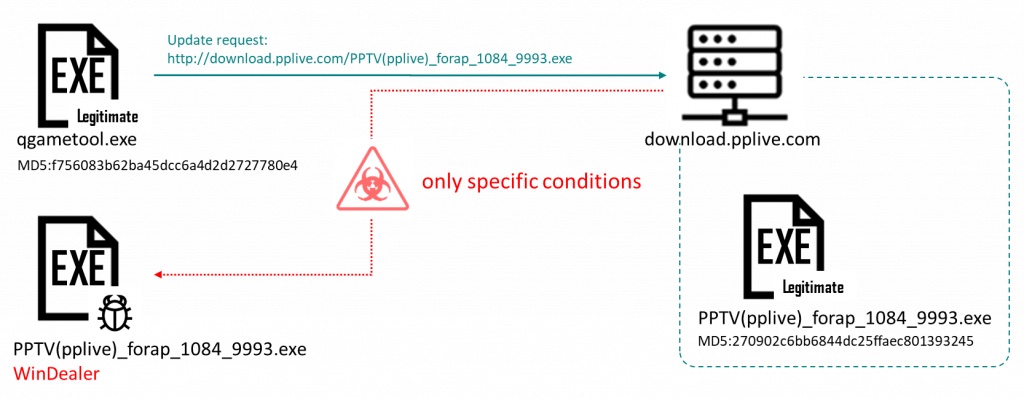
LuoYu has switched to abusing the automatic update mechanism of their victims' apps after previously pushing malware in easier to pull-off watering-hole attacks where they would use compromised local news sites as infection vectors.
"Man-on-the-side-attacks are extremely destructive, as the only condition needed to attack a device is for it to be connected to the internet. Even if the attack fails the first time, attackers can repeat the process over and over again until they succeed," explained Kaspersky senior security researcher Suguru Ishimaru.
"No matter how the attack has been carried out, the only way for potential victims to defend themselves is to remain extremely vigilant and have robust security procedures, such as regular antivirus scans, analysis of outbound network traffic and extensive logging to detect anomalies.”
Targeting Korean and Japanese organizations since at least 2014, LuoYu is also known for attacking foreign diplomatic organizations in China, the academic community, and organizations from multiple industry sectors, including defense and telecommunications.
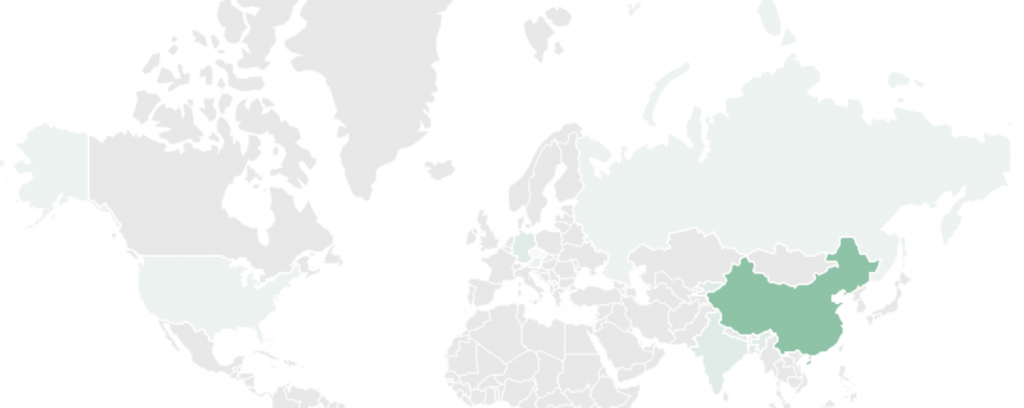
Kaspersky's Global Research and Analysis Team (GReAT) has also spotted occasional infections in other countries such as Germany, Austria, the United States, the Czech Republic, Russia, and India.
Recently, LuoYu has also started going after companies in East Asia and branches located within China.
Besides targeting Windows devices using WinDealer, this lesser-known hacking group has previously been observed attacking macOS, Linux, and Android devices with Demsty (ReverseWindow) and SpyDealer malware.
"LuoYu is an extremely sophisticated threat actor able to leverage functionality available only to the most mature attackers. We can only speculate as to how they were able to develop such capabilities," Ishimaru added.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now