
A spear-phishing campaign likely coordinated by a state-backed threat actor has been targeting European government personnel providing logistics support to Ukrainian refugees.
According to American cybersecurity firm Proofpoint, the attackers use "possibly compromised" email accounts of Ukrainian armed service members to deliver the phishing message.
The researchers said the phishing attacks they observed were targeting only European governmental entities and added that, for now, they couldn't attribute the attacks to a specific state-sponsored hacking group.
"Proofpoint has identified a likely nation-state sponsored phishing campaign using a possibly compromised Ukrainian armed service member’s email account to target European government personnel involved in managing the logistics of refugees fleeing Ukraine," Proofpoint researchers said.
"The email included a malicious macro attachment which attempted to download a Lua-based malware dubbed SunSeed," a malware downloader that can be used to deliver second-stage payloads to compromised devices.
However, based on the infection chain, the researchers said the campaign tracked as Asylum Ambuscade aligns and is likely related to July 2021 phishing attacks linked to the Ghostwriter Belarusian threat group (also tracked as TA445 or UNC1151).
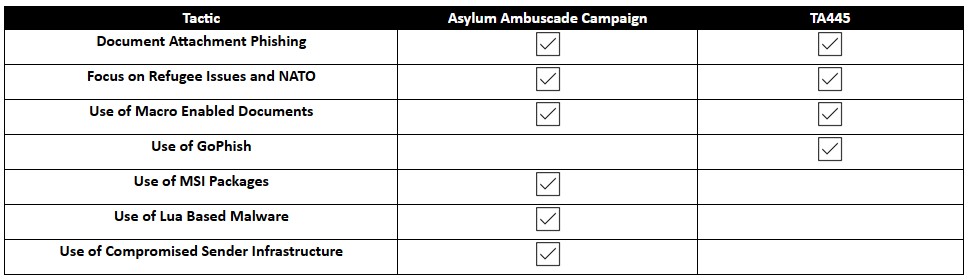
Ghostwriter was linked with high confidence in November 2021 by Mandiant security researchers to the Belarusian government.
Since Russia invaded Ukraine seven days ago, this threat group has already been linked to other attacks against Ukrainians.
For instance, the Computer Emergency Response Team of Ukraine (CERT-UA) warned of Ghostwriter operators attempting to compromise the private email accounts of Ukrainian military personnel and "related individuals" to deliver phishing to their contacts.
On Monday, Facebook also took down accounts used by Ghostwriter to target the accounts of Ukrainian officials and military personnel on its platform. It also added that it blocked phishing domains used to try and compromise the accounts of Ukrainian users.
"This activity, independent of attribution conclusions, represents an effort to target NATO entities with compromised Ukrainian military accounts during an active period of armed conflict between Russia, its proxies, and Ukraine," the Proofpoint researchers concluded.
"Additionally, the possibility of exploiting intelligence around refugee movements in Europe for disinformation purposes is a proven part of Russian and Belarussian-state techniques."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now