
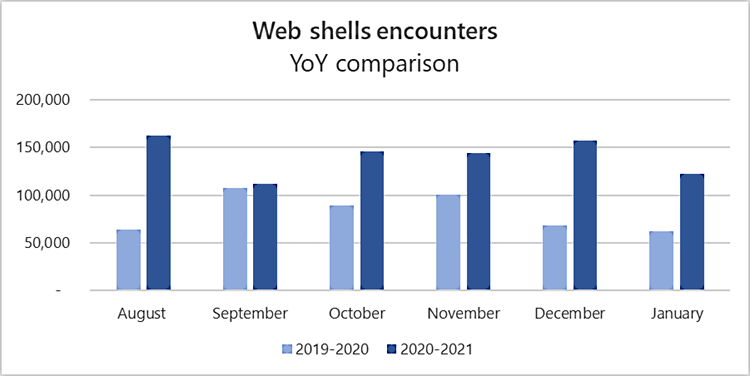
Microsoft says that the number of monthly web shell attacks has almost doubled since last year, with an average of 140,000 such malicious tools being found on compromised servers every month.
Web shells are tools (scripts or programs) that threat actors deploy on hacked servers to gain and/or maintain access, as well as to remotely execute arbitrary code or commands, to move laterally within the network, or to deliver additional malicious payloads.
They can be deployed in a large variety of forms, from app plugins and PHP or ASP code snippets injected within web apps to programs designed to provide web shell features and Perl, Python, Ruby, and Unix shell scripts.
"The latest Microsoft 365 Defender data shows that this trend not only continued, it accelerated: every month from August 2020 to January 2021, we registered an average of 140,000 encounters of these threats on servers," Microsoft said.
In comparison, the Microsoft Defender Advanced Threat Protection (ATP) team said in a report published last year that it was detecting an average of 77,000 web shells each month, based on data collected from roughly 46,000 distinct devices.
Microsoft also provided some tips on how to harden servers against attacks attempting to download and install a web shell.
The list of preventive measures that should prevent web shell attacks include:
- Identify and remediate vulnerabilities or misconfigurations in web applications and web servers. Use Threat and Vulnerability Management to discover and fix these weaknesses. Deploy the latest security updates as soon as they become available.
- Implement proper segmentation of your perimeter network, such that a compromised web server does not lead to the compromise of the enterprise network.
- Enable antivirus protection on web servers. Turn on cloud-delivered protection to get the latest defenses against new and emerging threats. Users should only be able to upload files in directories that can be scanned by antivirus and configured to not allow server-side scripting or execution.
- Audit and review logs from web servers frequently. Be aware of all systems you expose directly to the internet.
- Utilize the Windows Defender Firewall, intrusion prevention devices, and your network firewall to prevent command-and-control server communication among endpoints whenever possible, limiting lateral movement, as well as other attack activities.
- Check your perimeter firewall and proxy to restrict unnecessary access to services, including access to services through non-standard ports.
- Practice good credential hygiene. Limit the use of accounts with local or domain admin level privileges.
Web shell warning from the NSA
The U.S. National Security Agency (NSA) also warned of threat actors escalating their attacks on vulnerable web servers to deploy web shell backdoors in a joint report issued with the Australian Signals Directorate (ASD) in April 2020.
"Malicious cyber actors have increasingly leveraged web shells to gain or maintain access on victim networks," the NSA said.
The NSA has a dedicated GitHub repository with tools that organizations and admins can use to detect and block web shell threats including:
- Scripts for "Known-Good" file comparison
- Scripts, Splunk queries, YARA rules, network and Snort signatures to detect web shells
- Instructions on how to use Endpoint Detection and Response solutions (Microsoft Sysmon, Auditd) to detect web shells on Windows and Linux
- HIPS rules to allow McAfee's Host Based Security Systemto block file system changes


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now