
A previously unknown and financially motivated hacking group is impersonating a Russian agency in a phishing campaign targeting entities in Eastern European countries.
The phishing emails pretend to come from the Russian Government’s Federal Bailiffs Service and are written in the Russian language, with the recipients being telecommunication service providers and industrial firms in Lithuania, Estonia, and Russia.
The ultimate goal of the malicious emails is to drop a copy of the DarkWatchman malware onto the victim’s computers, a lightweight, stealthy JavaScript RAT (remote access tool) with a C# keylogger.
DarkWatchman has been linked to Russian threat actors before, focusing primarily on targeting organizations in their own country.
In this campaign, discovered by IBM’s X-Force team, the threat group is identified as Hive0117, and they appear to take advantage of the turbulence in the region, which is currently facing a variety of malicious cyber activities.
Campaign details
In many of the cases seen by X-Force, the phishing emails targeted the owners of companies or at least high-ranking employees.
The sender's address imitates an authentic one from the Russian Ministry of Justice, for example, “mail@r77[.]fssprus[.]ru”, and the email body also features the real emblem.
The subject of the emails is typically something compelling that will convince the recipient to open the attachment, which is a ZIP archive named 'Исполнительный лист XXXXXXX-22' or 'Счет 63711-21 от 30.12.2021.zip'.
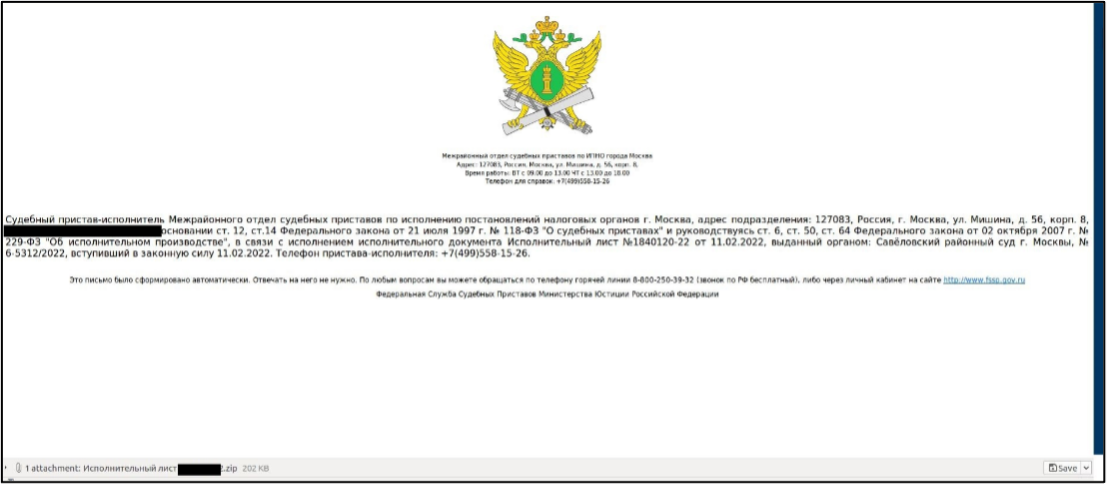
"The contents of the emails feature identical Russian-language text detailing several articles related to enforcement procedures associated with the Kuntsevsky District Court of Moscow, upheld by the 'Bailiff of the Interdistrict Department of Bailiffs for the Execution of Decisions of the Tax Authorities'," explains IBM in their report.
The attached ZIP file attachments contain executables that drop DarkWatchman on the compromised machine, along with a copy of the encrypted keylogger.
In some cases, the threat actors used loader files that fetched two obfuscated payloads from an online resource (domtut[.]site|fun|online), a JavaScript file that is the backdoor, and a PowerShell block that executes a keylogger.
X-Force’s analysis also reveals that the DarkWatchman strain used by Hive0117 employs a domain generation algorithm (DGA) to generate C2 domains, making its infrastructure mapping and take-down harder.
Parallel Activity
IBM's analysts believe Hive0117 isn't affiliated with Russian APTs or part of a state-sponsored cluster that carries out cyber-espionage and cyber-warfare operations.
"While the target list of the phishing campaign attributed to Hive0117 has regional associations with the Russian invasion of Ukraine, the activity predates the invasion, indicating they're separate from any politically charged associations that have spurred recent waves of criminal activity," explains IBM
The threat group appears to be motivated by financial profit, and they're likely targeting entities with a large user base to access their client pool indirectly.
The use of DarkWatchman, a file-less malware, is categorizing Hive0117 as a semi-sophisticated actor, still capable of causing significant damage to organizations in Eastern Europe.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now