
A new message today from the operators of Babuk ransomware clarifies that the gang has decided to close the affiliate program and move to an extortion model that does not rely on encrypting victim computers.
The explanation comes after yesterday the group posted and deleted two announcements about their plan to close the project and release the source code for the malware.
Data theft extortion
The gang seems to have chosen a road different from the ransomware-as-a-business (RaaS) model, where the hackers steal data before deploying the encryption stage, as leverage in negotiations for the ransom payment.
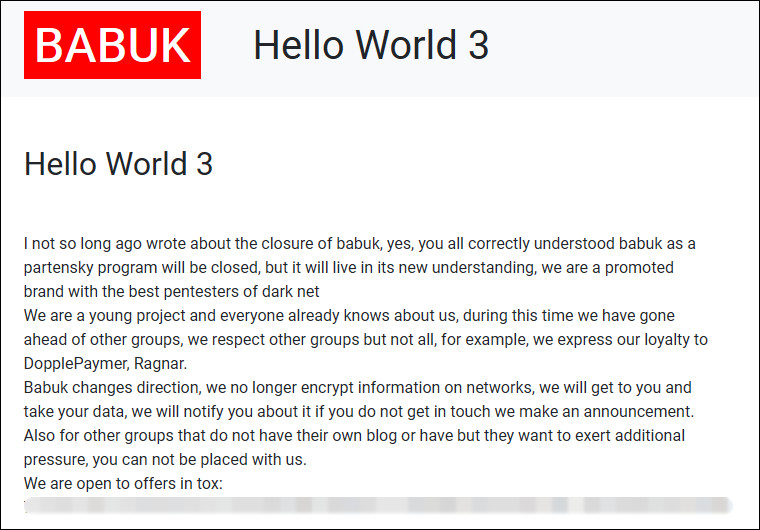
According to a third “Hello World” message posted on their leak site, Babuk’s newly announced model remains almost the same, except the data encryption component.
In essence, the cybercriminals will run an extortion-without-encryption business, demanding a ransom for information stolen from compromised networks.
“Babuk changes direction, we no longer encrypt information on networks, we will get to you and take your data, we will notify you about it if you do not get in touch we make an announcement” - Babuk ransomware
Exfiltrating data for higher ransom demands is a practice that Maze ransomware started in November 2019. It was quickly adopted by all major ransomware operations.
At the beginning of 2021, it became known that Clop ransomware ran a series of data-theft attacks on high-value companies without encrypting systems by exploiting zero-day vulnerabilities in Accellion's File Transfer Appliance.
The gang stole a large number of files and demanded large payments to not leak or trade the data. Multiple victims paid ransoms of tens of millions of dollars.
In today’s message Babuk ransomware says that despite being a new team on the ransomware scene, they already are well-known in the business because they have “the best pentesters of dark net.”
The advantages of this extortion business for Babuk remain unknown at the moment but the gang would need to exfiltrate larger quantities of data than in the case of encryption.
On their leak site, Babuk lists one victim from which they claim to have copied 10 terabytes of data. From Metropolitan Police Department (MPD), their most recent attack, the gang claims to have stolen 250GB of data.
It is also possible that this would drive up the group's profit either from demanding higher ransoms or from selling the data to competition or other interested parties.
RaaS operations have become so big in terms of affiliates that it’s very difficult to control every aspect of it.
Lately, this translated into technical and management changes that led to victims losing data because of poor quality decryption tools or having to deal with repeated attacks from the same gang. This happened with Conti, Lockbit, and REvil.
These issues affected many ransomware gangs that relied on their reputation of a party that respects their end of the deal to demand higher ransoms.



Comments
Amigo-A - 3 years ago
"""The advantages of this extortion business for Babuk remain unknown at the moment but the gang would need to exfiltrate larger quantities of data than in the case of encryption."""
The reason is problems with decrypting files. They cannot decrypt files correctly, and it is easier to take control and download files.