
Passwords have been a part of IT since the very beginning, more than half a century ago. Given that passwords have had such unprecedented longevity, it would seem that password security best practices would have been refined to the point of perfection and that following commonly recited best practices for password use would be a guaranteed way of keeping passwords safe.
Even so, Specops Software’s first annual Weak Password Report has yielded some interesting results that may cause you to rethink the way that your organization manages passwords.
1. Password Length Does Not Guarantee Password Safety
One of the most long-standing of all password best practices is the idea that passwords need to be at least eight characters in length. This well-intentioned best practice is based on the idea that longer passwords require more computational resources to crack.
The problem with this however, is that leaked password databases have allowed cyber criminals to create lookup tables that can be used to reveal a password based on its hash, without actually having to crack the password, thereby making password length far less of a problem for cyber criminals.
This idea was reflected in the 2022 Weak Password Report which found that 93% of the passwords that were used in brute force attacks included at least eight characters. Similarly, 41% of the passwords used in real world attacks are twelve or more characters in length. These statistics underscore the idea that even long passwords can be leaked.
2. Password Is Often Seasonal or Influenced by Pop Culture
The Weak Password Report found that passwords are often seasonal and that it is also common for passwords to be influenced by pop culture. 42% of seasonal passwords for example, contained the word “summer”.
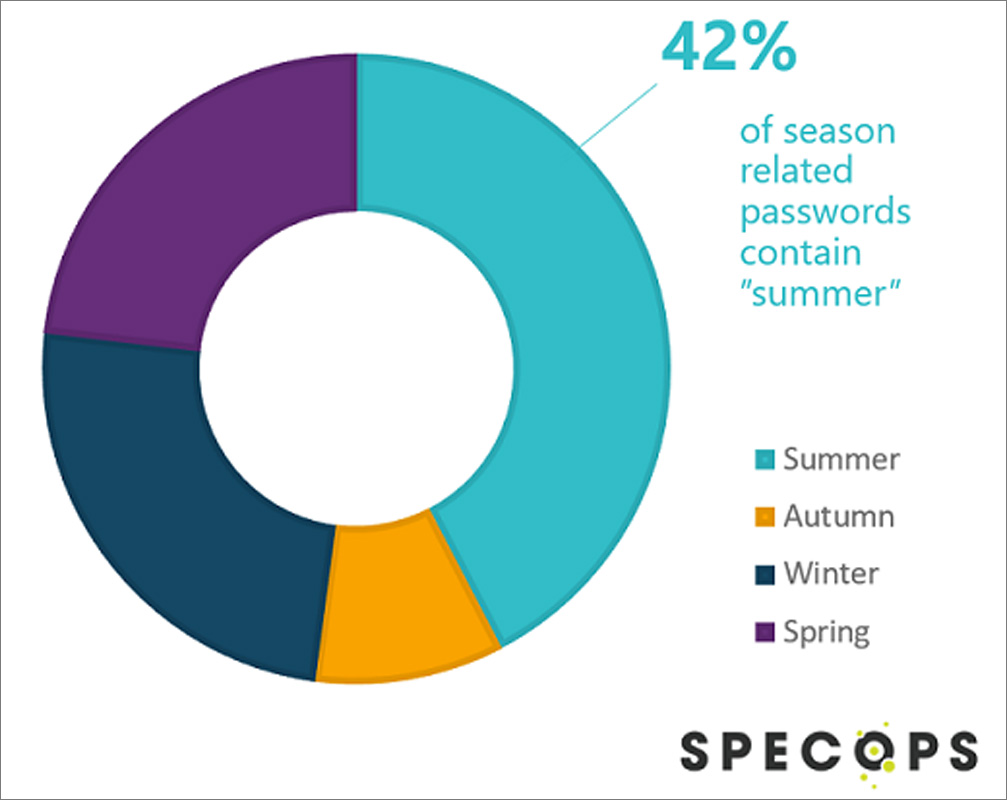
And it isn’t just seasons of the year that seem to influence password use. Baseball season is another type of season and the report found that the Cincinnati Reds appeared within the breached password lists nearly 150,000 times. Similarly, the Los Angeles Angels, Tampa Bay Rays, New York Mets, and Minnesota Twins were also commonly found on lists of leaked passwords.
Not surprisingly, sports teams are far from being the only pop culture reference commonly found in passwords. Best-selling musical artists such as AC/DC, Kiss, and Metallica were commonly included in passwords, as were blockbuster movies such as Star Wars, Spider-Man, and Avatar. For those who may be curious, the movie most commonly referenced within leaked passwords was Rocky, which showed up almost 96,000 times.
Of course, it wasn’t just the movie titles which were referenced within passwords, but also favorite characters from those movies. This was especially true for Star Wars movies and for various superhero movies where fandoms are notoriously dedicated.
3. Password Complexity Does Not Prevent Credential Theft
Another long-standing best practice is to require password complexity. An organization might, for example, require a mixture of upper- and lower-case characters, numbers, and symbols. Even so, the Weak Password Report found that 68% of the passwords used in real attacks included at least two different types of characters. There were over 20 million leaked passwords that included upper and lowercase letters and numbers, while over 1.5 million leaked passwords included upper and lowercase letters, numbers, and special characters.
The fact that there were more than 13 times as many leaked passwords containing only upper- and lower-case letters and numbers than a combination of upper- and lower-case letters, numbers, and symbols might initially suggest that complexity, while not fool proof, does indeed help with password security.
The more likely explanation, however, is that those who use more complex passwords are probably more likely to avoid the types of risky behavior that so often leads to credential theft.
4. Password Overload is a Big Problem
The report also found that password reuse is a major problem. Specops recently surveyed more than 2000 users to find out the role that passwords play in their day to day lives.
48% of the survey respondents indicate that they have 11 or more passwords that they have to remember for work. 71% said that they have 11 or more passwords to remember for personal use. The survey found that 361 of those respondents admitted to using the same or similar password on multiple systems.
This is likely attributed to the fact that users must remember so many different passwords.
5. Organizations Could Be Doing a Lot More to Keep Passwords Safe
The simple fact that there is a leaked password database containing millions of passwords that adhere to long established best practices clearly demonstrates the need for organizations to do more to keep their passwords secure. Even so, the 2022 Weak Password Report found that 54% of organizations do not have a tool for managing work passwords. Additionally, 48% of organizations do not have a user identity verification mechanism in place for their service desk, which exposes the service desk to social engineering risks.
One way that organizations can get a better handle on password use is to download Specops Password Auditor.
This free, read-only tool allows organizations to audit their Active Directory accounts for over 813 million known breached passwords, generate password reports, and to make sure that user’s passwords align with the organization’s requirements.
Sponsored and written by Specops.


Comments
iyanmv - 2 years ago
Or they can use the HIBP API for free ;)
https://haveibeenpwned.com/API/v3
CJatWork - 2 years ago
Pssst! Hey, Specops, it's Tampa Bay Rays; not "Raise".