
The Russian state-sponsored hacking group known as Sandworm tried on Friday to take down a large Ukrainian energy provider by disconnecting its electrical substations with a new variant of the Industroyer malware for industrial control systems (ICS) and a new version of the CaddyWiper data destruction malware.
The threat actor used a version of the Industroyer ICS malware customized for the target high-voltage electrical substations and then tried to erase the traces of the attack by executing CaddyWiper and other data-wiping malware families tracked as Orcshred, Soloshred, and Awfulshred for Linux and Solaris systems.
Researchers at cybersecurity company ESET collaborating with the Ukrainian Computer Emergency Response Team (CERT) to remediate and protect the attacked network say that they do not know how the attacker compromised the environment or how they managed to move from the IT network into the ICS environment.
The image below shows an overview of the data wiping components used in the attack:
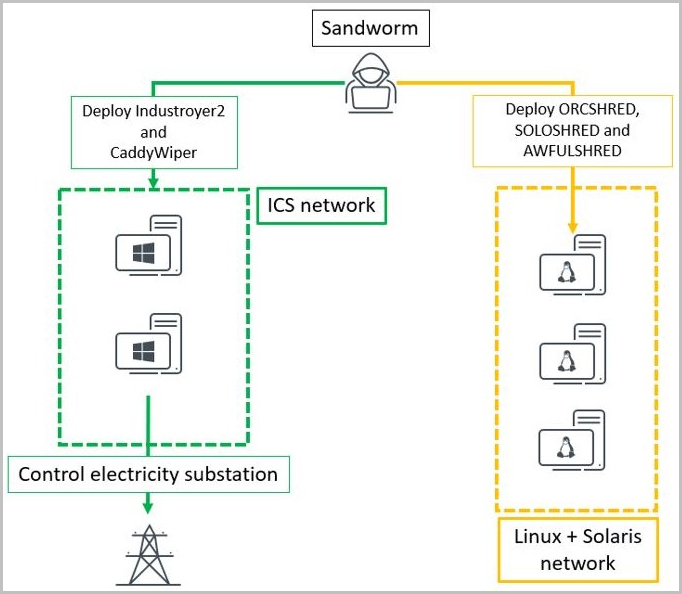
In an announcement today, CERT-UA notes that the threat actor's goal was "decommissioning of several infrastructural elements."
The ICS malware used in the attack is now tracked as Industroyer2 and ESET assesses "whith high confidence" that it was built using the source code of Industroyer used in 2016 to cut the power in Ukraine and attributed to the state-sponsored Russian hacking group Sandworm.
CERT-UA and ESET say that Sandworm planned to start the final stage of the attack on Friday, April 8 (at 14:58 UTC) by deploying malware on the following types of systems:
- Windows computers and automated workstations by deploying the CaddyWiper malware, decrypted, loaded, and executed via the ArgeuPatch and Tailjump tools (at 14:58 UTC)
- Linux servers using the OrcShred, Soloshred, and AwfulShred scripts (at 14:58 UTC)
- high-voltage electrical substations using the INDUSTROYER2 malware, each executable containing a set of unique parameters specified for their respective substation targets. Sandworm operators created a scheduled task at 15:02:22 UTC to launch the malware at 16:10 UTC and cut power in an Ukrainian region
- active network equipment
At 16:20 UTC, the adversary executed CaddyWiper on the machines to erase the tracks of Industroyer2.
CERT-UA says that "the implementation of [Sandworm's] malicious plan has so far been prevented" while ESET notes in a technical report on the malware used in this attack that "Sandworm attackers made an attempt to deploy the Industroyer2 malware against high-voltage electrical substations in Ukraine."
ESET researchers say that Industroyer2 is highly configurable and comes with hardcoded detailed configuration, which requires it to be recompiled for each new victim environment.
"However, given that the Industroyer malware family was only deployed twice, with a five year gap between each version, this is probably not a limitation for Sandworm operators." - ESET
The researchers say that the Portable Executable timestamp of Industroyer2 shows that it was compiled on March 23, which suggests that the attack had been planned for at least two weeks.
Additional tools used in the attack include the PowerGap PowerShell script used to add a Group Policy that downloads payloads and creates scheduled tasks, and Impacket, used for remote command execution.
The worm component in this attack - a Bash script named sc.sh - looks for accessible networks (via ip route or ifconfig) and tries to connect to all available hosts via SSHH (TCP port 22, 2468, 24687, 522) using credentials in a list the adversary added in the script.
New Industroyer version
Industroyer, also known as CrashOverride, was first sampled and analyzed in 2017, with ESET calling it the "biggest threat to industrial control systems since Stuxnet".
The new variant used last week on an Ukrainian energy provider is an evolution of the original malware used in the 2016 power outage attacks in Ukraine.
Industroyer2 only employs the IEC-104 protocol to communicate with industrial equipment, whereas previously, it supported multiple ICS protocols.
It's more configurable than the original strain and the settings, including IOAs, timeouts, and ASDUs, are stored as a string which is passed through the IEC-104 communication routine.
According to ESET's analysis, the recently analyzed sample communicated with eight devices simultaneously.
The exact actions performed by Industroyer2 after its connection to the relays are still being examined, but it has been determined that it terminates the legitimate processes that industrial equipment performs in its standard operation.
Recent Sandworm activities
The recent attack on Friday appears to be a parallel operation from Sandworm, who also focused on targeting WatchGuard firewall appliances and ASUS routers using the Cyclops Blink botnet.
That botnet was severely disrupted last week due to coordinated action of American law enforcement and cyber-intelligence agencies.
CERT-UA placed the initial compromise to February 2022 and identified two distinct attack waves against the victim organization, resulting in some substation disconnections.
This coincides with another operation run in parallel by Sandworm, which was the build-up of the Cyclops Blink botnet that attacked WatchGuard firewall appliances, and later also ASUS routers.
ANSSI, the French national cyber-security agency, blames Sandworm for a campaign starting in 2017 that focused on compromising French IT providers that were using an outdated version of the Centreon network, system, and monitoring tool.
Sandworm is an experienced cyber-espionage threat group that has been associated with the Russian Military Unit 74455 of the Main Intelligence Directorate (GRU).
CERT-UA has shared indicators of compromise (Yara rules, file hashes, hosts, network) to help prevent new attacks from this threat actor.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now