
The GravityRAT remote access trojan is being distributed in the wild again, this time under the guise of an end-to-end encrypted chat application called SoSafe Chat.
This particular RAT (remote access trojan) targets predominately Indian users, being distributed by Pakistani actors.
The telemetry data on the most recent campaign shows that the targeting scope hasn’t changed, and Gravity is still targeting high-profile individuals in India, like officers of the Armed Forces.
Disguised as a secure chat app
In 2020, the malware was targeting people via an Android app named ‘Travel Mate Pro,’ but since the pandemic has slowed down traveling, the actors moved to a new guise.
The app is now called ‘SoSafe Chat’ and is promoted as a secure messaging application that features end-to-end encryption.
The website that likely played a role in the distribution of the app (sosafe.co[.]in) remains online today, but the download link and the registration form are no longer working.
The channel and method of distribution remain unknown, but it was likely by driving traffic to the site through malvertising, social media posts, and instant messages to targets.
Extensive spying abilities
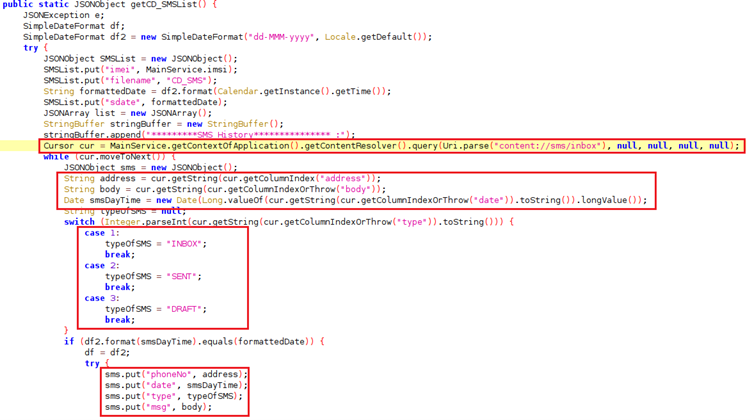
Once installed on a target’s device, the spyware can perform a wide range of malicious behavior, allowing the threat actors to exfiltrate data, spy on the victim, and track their location.
The complete list of malicious behavior includes
- Read SMS, Call Logs, and Contacts data
- Change or modify system settings
- Read current cellular network information, the phone number and the serial number of the victim’s phone, the status of any ongoing calls, and a list of any Phone Accounts registered on the device
- Read or write the files on the device’s external storage
- Record audio
- Gets connected network information
- Get the device’s location
According to researchers at Cyble, the list of permissions that the malware requests for this functionality is naturally quite extensive, but it can still appear justified for an IM app.
.jpg)
Source: Cyble
Compared to the 2020 version, GravityRAT has added the ability to record audio and added mobile-specific features like location fetching and cellular network data exfiltration.
Source: Cyble
Before the 2020 version, GravityRAT would exclusively target Windows machines, not having the ability to infect mobile devices.
As such, the reemergence of the malware in the wild in targeting mobile devices indicates that its authors are actively developing it.


Comments
Oliver55h - 2 years ago
Please I have exactly this type of problem on my galaxy s20, ever since then I could not retrieve my private email account which had access to my blockchain ,
Now this s20 is broke down and become useless, this phone was just new I never enjoyed it , just because I helped a friend by sharing my hotspot, ever since then , I have been buying new phones everyday but those hackers still find their ways
For over 6 months about 5 phones and 2 laptops he been hijeacked by this particular people, almost they use ads , chrome, and google , always making sure that my browser is redirected to a fake site, i which I could help myself but in just a novice on that particular deals .
But firstly they will make my new device loss total internet connection, then they will configure it to be my part. of my service provider.
My speech here might not be all good or not well explained but this is how I understand my situation.
They made me really broke i loss about 5 phones all my business account , emails , partners and friends, i loss all
Now this my iPhone is their next target , they had really made me uncomfortable for the past 5weeks I bought the phone ,
Everything feels dumb and not working, but actually someone has all target and focuse to my business as well as my life , because they also upgrade my device , and all my activities are directly shown to them .
They can also stop my activities, redirect me, has full access to my informations and account , monitor my calls and business .
Please help.