
The U.S. District Court for the Eastern District of Virginia has charged three men with money laundering and aggravated identity theft after allegedly conducting a business email compromise (BEC) scheme.
BEC scams use various tactics (including social engineering, malware, hacking, and phishing) to compromise or impersonate business email accounts with the end goal of redirecting pending or future payments to bank accounts under a threat actor's control.
The charged individuals are Onyewuchi Ibeh, 21, of Bowie, Maryland, Jason Joyner, 42, of Washington, D.C., and Mouaaz Elkhebri, 30, of Alexandria, Virginia.
Yesterday's indictment alleges that the three men infiltrated the corporate networks of small and large companies in the United States and across the globe, between January 2018 and March 2020.
The actors accessed email servers and email accounts by means of phishing employee credentials, and also by dropping malware. Then, they spent months intercepting communications and getting to learn about billing systems, style of communication, vendors, clients, people responsible for transactions, etc.
Then, when the timing was right, the scammers allegedly sent bogus emails to an employee, presenting a request for a payment that mirrored a real transaction that was due for payment at the time.
By using all the details of the actual transaction like full invoicing information, the actors managed to divert the payment to their own bank accounts.
One of the case examples in the indictment document seen by Bleeping Computer, mentions a single transaction of $356,954, sent by a victim in Boston to what they thought was the bank account of their business partner.
In this case, the BEC actors registered a domain that was exactly the same as that of the victim’s partner, except for a misspelled character (typo-squatting). The actors used the domains for direct communication with the victim, essentially mimicking the email address of the real partner.
In total, the investigators have connected the particular BEC operation with at least five victims and a total stolen amount of $1.1 million.
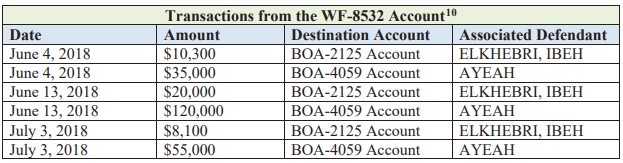
The indictment says that each person had a distinct role in the BEC scheme. Ibeh was managing the money laundering and was wiring the money to the other two.
Elkhebri, being a Bank of America and TD Bank employee between 2015 and 2018, was opening bank accounts under his co-conspirators’ and their victims’ names, and he also falsified bank book entries.
Joyner was withdrawing the stolen funds in ATMs and sent cash to the others.
From the affidavit:
In response to legal process, Bank of America produced personnel records for Elkhebri, who worked as a personal banker and relationship manager there from 2015 until 2017. During his time at Bank of America, Elkhebriopened multiple Conspirator Accounts, including an account that Ibehused in furtherance of the scheme.
In response to legal process, TD Bank also produced personnel records for Elkhebri, who worked there from 2017 until 2018. During his time at TD Bank, Elkhebri opened multiple Conspirator Accounts, including an account that Ayeah used in furtherance of the scheme.
If found guilty, Elkhebri is facing up to 52 years in prison, while the other two could face a maximum of 20 years of imprisonment as the gravity of their acts was less severe. These are maximum penalties, and the actual sentences are expected to be shorter.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now