
12/14/23 update with information from Ubiquiti added below.
Since yesterday, users of Ubiquiti networking devices, ranging from routers to security cameras, have reported seeing other people’s devices and notifications through the company's UniFi cloud services.
Ubiquiti is a popular networking device manufacturer offering a cloud-based UniFi platform where admins can manage all their devices from a single cloud portal.
The first report of these issues was from yesterday morning at around 8 AM ET when a Ubiquiti customer incorrectly received a notification through UniFi Protect from someone else's security camera.
"I'm reaching out for some advice regarding a peculiar situation we encountered with UniFi Protect. Recently, my wife received a notification from UniFi Protect, which included an image from a security camera," reads a Reddit post.
"However, here's the twist - this camera doesn't belong to us."
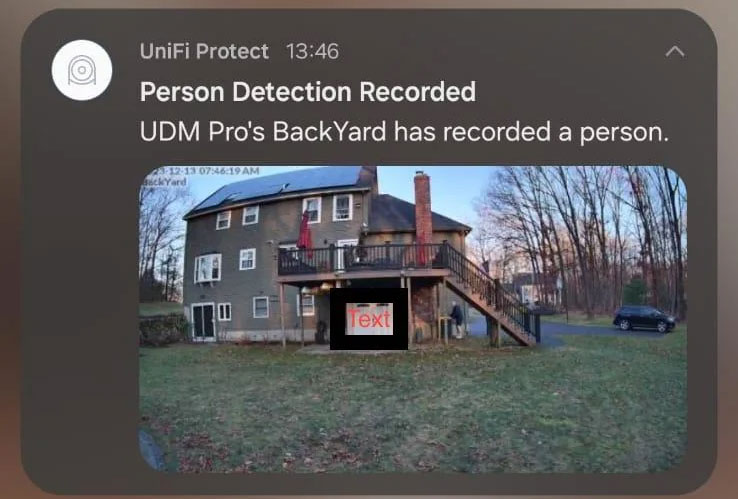
Source: Reddit
To make matters worse, another Ubiquiti customer says that when they logged into the UniFi Site Manager portal to manage their devices, they saw 88 devices from another customer's account.
"However this time I was presented with 88 consoles from another account. I had full access to these consoles, just as I would my own. This was only stopped when I forced a browser refresh, and I was presented again with my consoles," explains the UniFi customer.
"This is somewhat concerning, Has anyone else had this issue?"
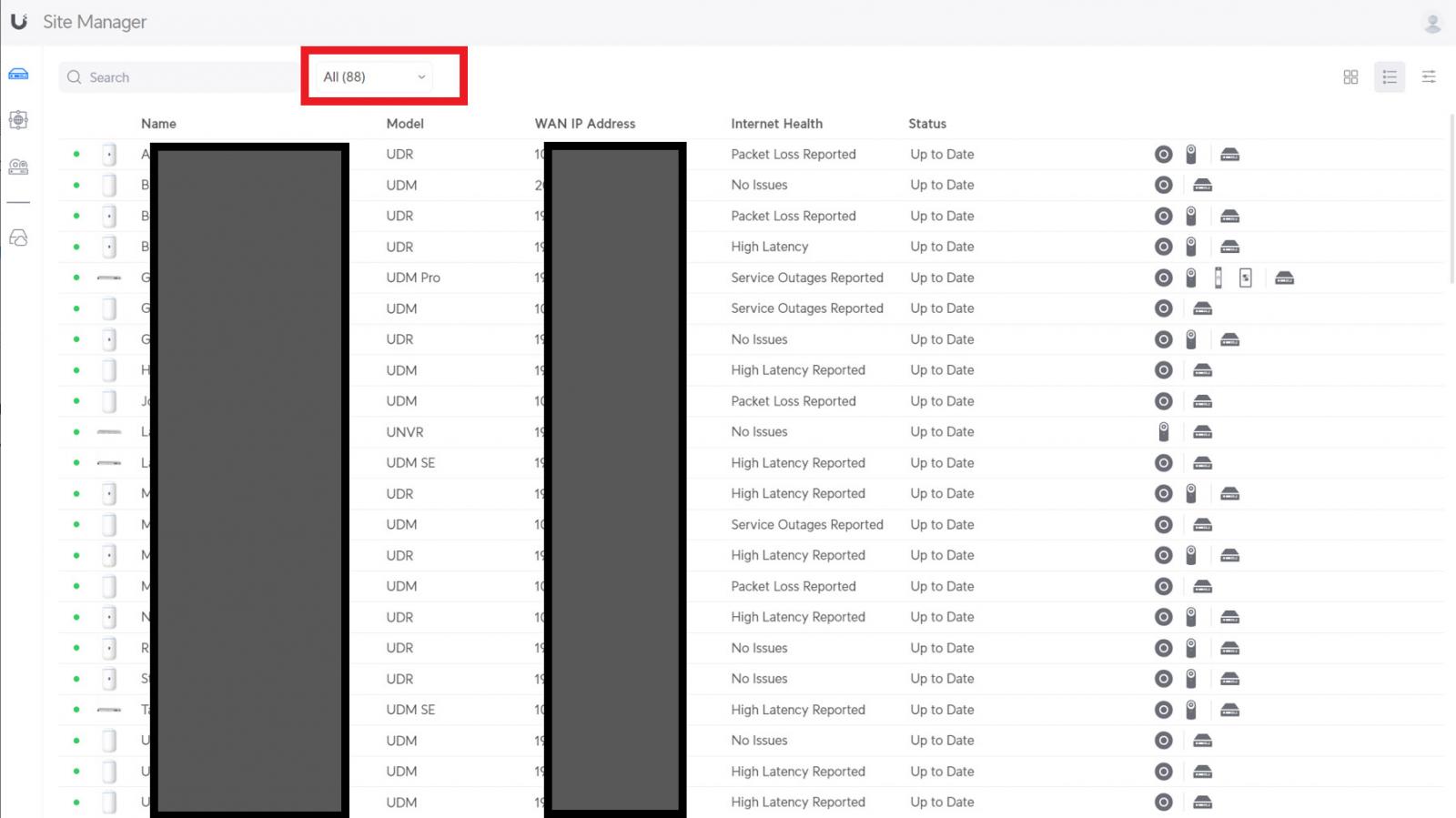
Source: Ubiquiti forums
A similar experience occurred with others on Reddit who says they logged in and had access to someone else's UDM Pro and were able to manage the device and create additional WiFi networks.
In both situations, once the portal web page was refreshed, they were shown the devices usually associated with their accounts.
When BleepingComputer contacted Ubiquiti about these issues, we were told they are currently gathering information to assess what is causing the issues. Ubiquiti says that they will issue a statement after the review is complete.
Employees have already started gathering information on Reddit and the company's forums, reaching out to impacted customers to learn more about what happened.
"This is not expected behavior. We reached out via Reddit Chat to gather more details and have our leads review immediately," reads a comment from an Ubiquiti representative on Reddit
Some customers are skeptical that this is actually happening, saying that Ubiquiti should be given time to investigate the issue.
However, other customers are frustrated that Ubiquiti is not coming forth with a public statement or listing it as a potential issue on the company's network status page, considering that users are reporting that they can modify other's networking configurations.
Caused by UniFi access misconfiguration
Ubiquiti has issued a statement saying that the bug allowing access to other customers' devices was caused by a misconfiguration in an upgrade to the UniFi cloud infrastructure.
The company says that 1,216 Ubiquiti accounts, which they call "Group 1," were associated with a separate group of 1,177 Ubiquiti accounts, known as "Group 2."
This misconfiguration allowed accounts in Group 2 to receive notifications meant for accounts in Group 1. It further allowed Group 2 accounts to see the devices of Group 1 customers when logged into the UniFi cloud management portal.
Ubiquiti says this issue occurred on December 13, between 6:47 AM and 3:45 PM UTC, and has since been fixed.
The company is still investigating the incident but believes that only twelve accounts were improperly accessed by other Ubiquiti customers. Account holders whose accounts were accessed by mistake will be notified via email.



Comments
Jaybee02 - 4 months ago
Meh its Ubiquity cloud, half of those 1200 customers are probably protected from remote access by their cloud key already having crashed/corrupted/failing to restart.
NoneRain - 4 months ago
oof