
Microsoft Defender for Endpoint is currently blocking Office documents from being opened and some executables from launching due to a false positive tagging the files as potentially bundling an Emotet malware payload.
Windows system admins are reporting [1, 2, 3, 4, 5] that this is happening since updating Microsoft's enterprise endpoint security platform (previously known as Microsoft Defender ATP) definitions to version 1.353.1874.0.
When triggered, Defender for Endpoint will block the file from opening and throw an error mentioning suspicious activity linked to Win32/PowEmotet.SB or Win32/PowEmotet.SC.
"We're seeing issues with definition update 1.353.1874.0 detecting printing as Win32/PowEmotet.SB this afternoon," one admin said.
"We are seeing this detected for Excel, any Office app using MSIP.ExecutionHost.exe ( AIP Sensitivity Client ) and splwow64.exe," another added.
A third one confirmed the issues with today's definition updates: "We're seeing the same behavior specifically with v.1.353.1874.0 of the definitions, which was released today, & included a definition for Behavior:Win32/PowEmotet.SB & Behavior:Win32/PowEmotet.SC."
BleepingComputer was able to trigger the false positive on a Windows 10 virtual machine with the latest Microsoft Defender signatures, as shown below.
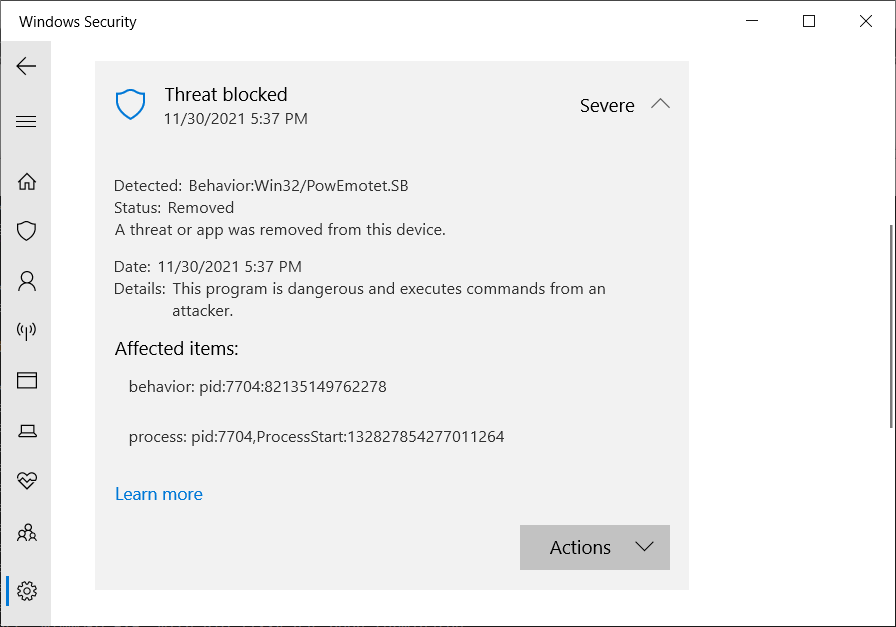
While Microsoft hasn't yet shared any info on what causes this, the most likely reason is that the company has increased the sensitivity for detecting Emotet-like behavior in updates released today, which makes Defender's generic behavioral detection engine too sensitive prone to false positives.
The change was likely prompted by the recent revival of the Emotet botnet from two weeks ago, after Emotet research group Cryptolaemus, GData, and Advanced Intel began seeing TrickBot dropping Emotet loaders on infected devices.
Even though this is almost surely not the real thing, the timing is definitely unfortunate with Emotet coming back and most Windows admins already on their toes.
As some of them have reported, they almost took their data centers offline to stop a possible Emotet infection from spreading before realizing that what they were seeing were likely false positives.
Since October 2020, Windows admins had to deal with other Defender for Endpoint including one that showed network devices infected with Cobalt Strike and another that marked Chrome updates as PHP backdoors.
Microsoft has told BleepingComputer that they have fixed the issue for cloud-connected users and working on a fix for everyone else.
"We are working to resolve an issue where some customers may have experienced a series of false-positive detections. This issue has been resolved for cloud-connected customers." - a Microsoft spokesperson.
Update 11/30/21: Added Microsoft's statement.



Comments
Zurv - 2 years ago
oh.. you got me good today MS.
alerts from SCCM came pouring in.
semi-anonyheath - 2 years ago
Thank you Bleeps! i was kind of scared when i see the defender pop up (along w an unusual printer pop up) and could not find anything online ... other than '5 days ago, definition update includes ....' which did not make me feel better... warned our admin (before found this post), he said 'u prob installed some crap software. good news is windows caught whatever it is' ...
then i follow my ocd and search again using different engines and 'posted 5 mins ago' i see this post!~!! like an angel appearing in the dark! THANK YOU!!! so i create an account here so i can post a big thank you!!!! THANK YOU!!!!
Carnivore - 2 years ago
My personal PC is affected by this. I just wasted an hour trying to print a Word document, then realized each print attempt was being blocked by Defender without producing a pop-up to let me know.
I was also affected by last month's Windows KB5005565 update that borked printing over my home network, and wasted another whole night trying to fix that while I was trying to complete a project with a tight deadline.
Jeez, it really seems like Microsoft doesn't want its customers to be able to print anything any more. Why don't they test these updates before screwing up everyone's lives?
SGvagon - 2 years ago
Thank you! I was scared as hell when I opened clean new Word 2003 document and MSE (Microsoft security essentials) popped out this virus. My question is, what should I do with this in quarantine now? Delete it?
SGvagon - 2 years ago
And I think, that MSE blocking me writing WordArt in office 2003, it immediately crash the app when I try open any WordArt (No, this issue doing new version of Actual Multiple Monitors) :D . Grrr. Too much issues in one day.
SGvagon - 2 years ago
Ok, I solved it by reinstall MSE :-) . Now all is clean and after open any Office document I don't have any alert message about Emotet :) .
romainmeraud - 2 years ago
Thanks for sharing.
New definition update version 1.353.1888.0 solves the problem...
Thanks MS for wasting 3h of my time this morning...
crabis - 2 years ago
not sure they fixed everything in 1888.... or I miss smth (seems like False detection Time > Signature Update Time)
Edit: I mis-guessed what AntivirusSignatureLastUpdated means - it does not mean, as name suggests, when Signature was updated on specific PC, but actually when it was created on Microsoft side. So it could be that fixed signature was applied after false detection happened.
AntivirusSignatureLastUpdated : 2021.12.01 00:17:06
AntivirusSignatureVersion : 1.353.1888.0
ThreatName : Behavior:Win32/PowEmotet.SB
InitialDetectionTime : 2021.12.01 02:09:04
LastThreatStatusChangeTime : 2021.12.01 02:09:05
ProcessName : C:\Program Files (x86)\Microsoft Azure Information Protection\MSIP.ExecutionHost.exe
1Ijax - 2 years ago
what a pain in the ass...i give them credit for at least not going full Mcafee and deleting office executable's.
AlphaJack - 2 years ago
Thank you for clearing this up. I was right in the middle of a client WebEx demo when Windows Defender flagged my Excel file as Win32/PowEmotet.SB malware.
The Excel file was in an AES encrypted zip file. Two threat alerts were blasted across my screen when the zip file was expanded. So far MS Office 365 looks untouched and the Excel file is fully functional.
Got some explaining to do.