
Windows 10 and Windows 11 are vulnerable to a local elevation of privilege vulnerability after discovering that users with low privileges can access sensitive Registry database files.
The Windows Registry acts as the configuration repository for the Windows operating system and contains hashed passwords, user customizations, configuration options for applications, system decryption keys, and more.
The database files associated with the Windows Registry are stored under the C:\Windows\system32\config folder and are broken up into different files such as SYSTEM, SECURITY, SAM, DEFAULT, and SOFTWARE.
As these files contain sensitive information about all user accounts on a device and security tokens used by Windows features, they should be restricted from being viewed by regular users with no elevated privileges.
This is especially true for the Security Account Manager (SAM) file as it contains the hashed passwords for all users on a system, which threat actors can use to assume their identity.
SAM file can be read by anyone
Yesterday, security researcher Jonas Lykkegaard told BleepingComputer he discovered that the Windows 10 and Windows 11 Registry files associated with the Security Account Manager (SAM), and all other Registry databases, are accessible to the 'Users' group that has low privileges on a device.
These low permissions were confirmed by BleepingComputer on a fully patched Windows 10 20H2 device, as shown below.
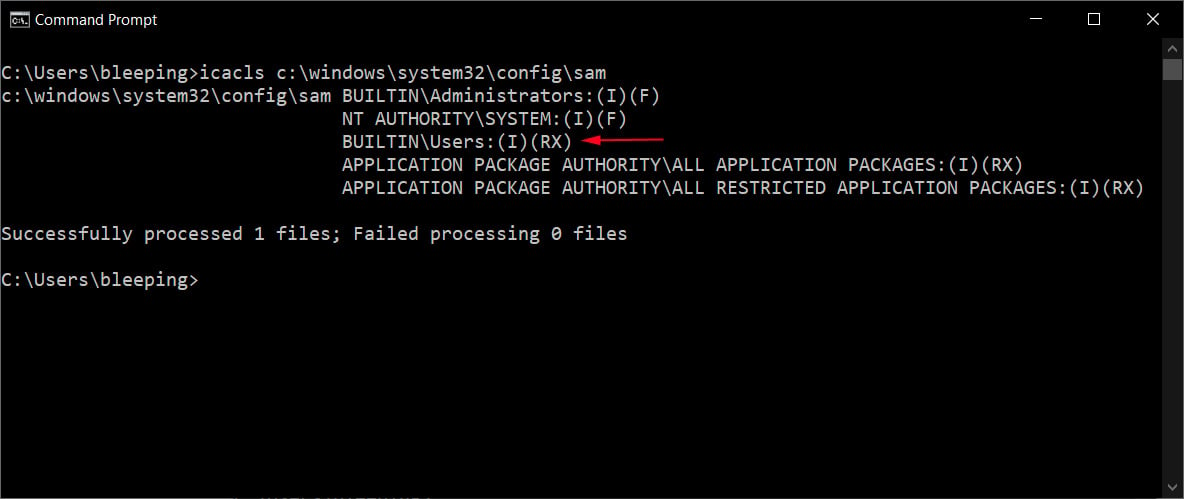
With these low file permissions, a threat actor with limited privileges on a device can extract the NTLM hashed passwords for all accounts on a device and use those hashes in pass-the-hash attacks to gain elevated privileges.
As the Registry files, such as the SAM file, are always in use by the operating system, when you attempt to access the file, you will receive an access violation as the files are open and locked by another program.
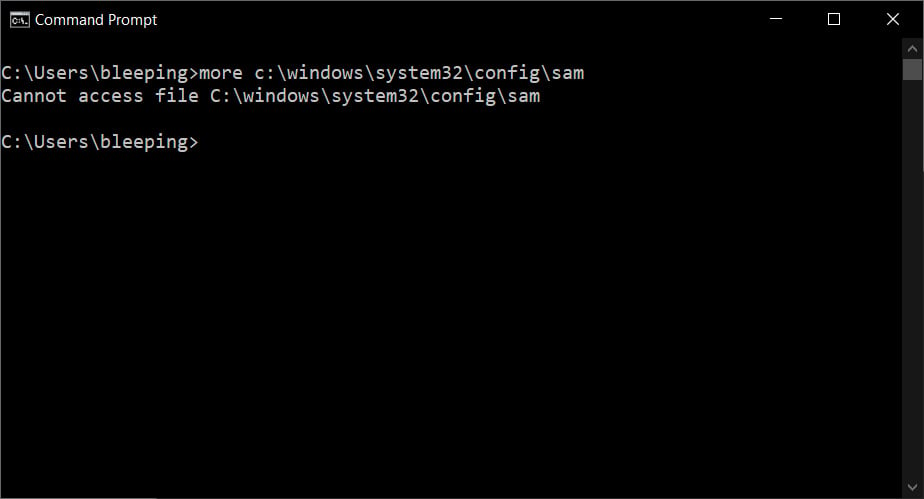
However, as the Registry files, including the SAM, are usually backed up by the Windows shadow volume copies, Lykkegaard says you can access the files through shadow volumes without an access violation.
For example, threat actors can use the following Win32 device namespace path for shadow volume copies below to access the SAM file by any user on the computer.
\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM
Using these low and incorrect file permissions, along with shadow volume copies of the files, Security researcher and Mimikatz creator Benjamin Delpy has told BleepingComputer that you could easily steal an elevated account's NTLM hashed password to gain higher privileges.
This attack is demonstrated in the video below created by Delpy and shared with BleepingComputer that shows Mimikatz using an NTLM hash to gain debug privileges.
In addition to stealing NTLM hashes and elevating privileges, Delpy told BleepingComputer that this low privileged access could allow for further attacks, such as Silver Ticket attacks.
It is unclear why Microsoft changed the permissions on the Registry to allow regular users to read the files.
However, Will Dormann, a vulnerability analyst for CERT/CC, and SANS author Jeff McJunkin, said Microsoft introduced the permission changes in Windows 10 1809.
Strangely, Dormann stated that when installing a fresh version of Windows 10 20H2 from June, the loose permissions were not present.
Therefore, it is not clear if Microsoft fixed the permission issue when performing a clean. installation of Windows but did not fix it when upgrading to new versions.
To check if your Windows 10 or Windows 11 installation is affected, you can open a command prompt and enter the following command:
icacls c:\windows\system32\config\sam
If the output displays the following permission, your Windows installation is affected by the vulnerability.
BUILTIN\Users:(I)(RX)
Thankfully, Microsoft has shared a temporary fix for the vulnerability that is described in the next section,
Microsoft confirms vulnerability
In a security advisory released today, Microsoft has confirmed the vulnerability and is now tracking it as CVE-2021-36934.
"We are investigating and will take appropriate action as needed to help keep customers protected," Microsoft told BleepingComputer.
Security researchers are also =referring to this vulnerability as 'SeriousSAM' or 'HiveNightmare.'
In the advisory, Microsoft has shared mitigations that restrict the permissions on the C:\Windows\system32\config folder.
To block exploitation of this vulnerability temporarily you need to take the following steps:
Restrict access to the contents of %windir%\system32\config:
-
Open Command Prompt or Windows PowerShell as an administrator.
-
Run this command:
icacls %windir%\system32\config\*.* /inheritance:e
Delete Volume Shadow Copy Service (VSS) shadow copies:
-
Delete any System Restore points and Shadow volumes that existed prior to restricting access to %windir%\system32\config.
-
Create a new System Restore point (if desired).
Update 7/20/21 7:15 PM EST: Added Microsoft's statement and the link to the advisory.
Update 7/21/21: Added mitigations.


Comments
Some-Other-Guy - 2 years ago
"It is unclear why Microsoft changed the permissions on the Registry to allow regular users to read the files."
It is quite obvious actually
Microsoft has chosen the "Global Trust Model" as an enabler of plausible deniability
To retain "Zero Trust" for all actors (including Microsoft), simply create a new regkey to enable Zero Trust and change the value from 0 to 1
-------------------------------------------------------------------------------
Disclaimer:
This key and it's value does absolutely nothing, but like all Windows security options.......
It kinda makes you "feel good" doesn't it?
Dominique1 - 2 years ago
When you think that MS has hit the bottom of the barrel, they will always surprise you by digging their grave even deeper. :facepalm:
woody188 - 2 years ago
They are dubbing this one "Summer of SAM" It's going to be a long summer.
TechFA - 2 years ago
This one threw me for a loop... When running (Get-Acl C:\windows\system32\config\sam).Access I did see the BUILTIN\Users permission. I then navigated to C:\windows\system32\config in Windows Explorer to check on the permissions tab there. Normally you have to click a link in the dialog box to get further into the folder with administrative permissions, not taking ownership or anything like that. After which I was surprised to see that there was no Users permissions in there. Scratching my head, I went back and ran the PowerShell command, it was now gone and persists after a reboot. It seems that going into the folder permissions fixed it! In my case, my laptop was built years ago and has gone through the full lifecycle of Win10 updates. Hopefully this helps get to the cause of the issue.
Setiron - 2 years ago
I am not seeing this on my systems, only system and the administrators group have access to the SAM file. Or shadow copies.
newtronic - 2 years ago
I did not try to understand if my system was vulnerable. But in following the instructions for the work around, I did the first part: icacls %windir%\system32\config\*.* /inheritance:e
But then for the second part the instructions turn vague: Delete Volume Shadow Copy Service (VSS) shadow copies
What I did was: vssadmin delete shadows /all
Is that correct?
doriel - 2 years ago
fully patched 1809 Enterprise does not seem to have this vulnerability.
cosuna - 2 years ago
Striker: “Surely you can’t be serious,”
Rumack: “I am serious — and don’t call me Shirley.”
doriel - 2 years ago
:D
lost_bracket - 2 years ago
Why not put detailed instructions in step 2 as well? Not a lot of people know how to delete shadow copy volumes.