A new side-channel attack impacting multiple generations of Intel CPUs has been discovered, allowing data to be leaked through the EFLAGS register.
The new attack was discovered by researchers at Tsinghua University, the University of Maryland, and a computer lab (BUPT) run by the Chinese Ministry of Education and is different than most other side-channel attacks.
Instead of relying on the cache system like many other side-channel attacks, this new attack leverages a flaw in transient execution that makes it possible to extract secret data from user memory space through timing analysis.
The attack works as a side channel to Meltdown, a critical security flaw discovered in 2018, impacting many x86-based microprocessors.
Meltdown exploits a performance optimization feature called “speculative execution” to enable attackers to bypass memory isolation mechanisms to access secrets stored in kernel memory like passwords, encryption keys, and other private data.
Meltdown has been largely mitigated through software patches, microcode updates, and hardware redesigns; however, no solution has addressed the problem 100%, and the latest attack method might work even in fully patched systems depending on hardware, software, and patch configurations.
Transient execution timing attack
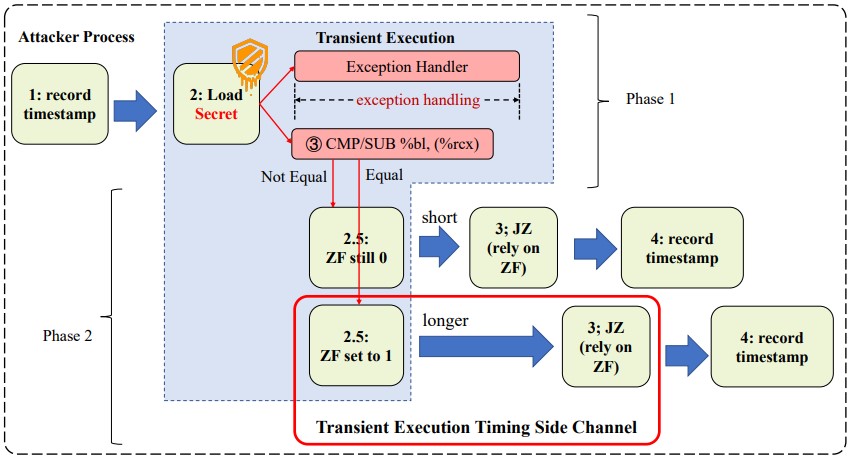
The new side-channel attack presented in a technical paper published on Arxiv.org describes a flaw in the change of the EFLAGS register in transient execution, affecting the timing of JCC (jump on condition code) instructions.
The EFLAGS register is a CPU register that holds various flags related to the processor’s state, while the JCC instruction is a CPU instruction that allows conditional branching based on the content of the EFLAGS register.
The attack is carried out in two phases, the first being to trigger transient execution and encode secret data through the EFLAGS register, and the second is to measure the execution time of the KCC instruction to decode the data.
The experimental data showed that the attack achieved 100% data retrieval (leak) for the Intel i7-6700 and Intel i7-7700 and had some success against the newer Intel i9-10980XE CPU. The experiment was conducted on Ubuntu 22.04 jammy with Linux kernel version 5.15.0.
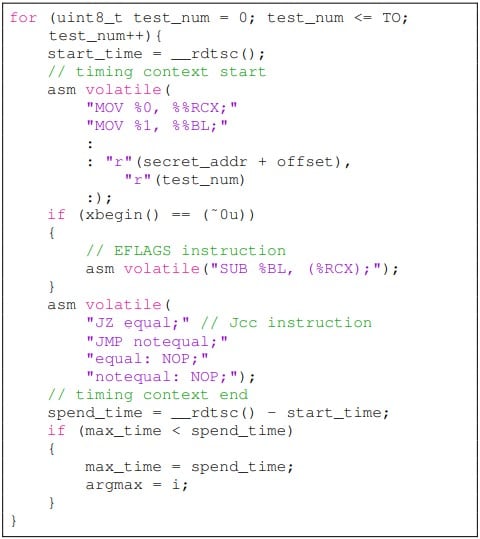
However, the researchers note that this timing attack isn’t as reliable as cache-state side-channel methods, and to get better results in recent chips, the attack would have to be repeated thousands of times.
“In our experiment, we found that the influence of the EFLAGS register on the execution time of Jcc instruction is not as persistent as the cache state,” reads the part about the evaluation of the experimental data.
“For about 6-9 cycles after the transient execute, the Jcc execute time will not be about to construct a side-channel. Empirically, the attack needs to repeat thousands of times for higher accuracy.”
The researchers admit that the root causes of the attack remain elusive and hypothesize that there’s a buffer in the execution unit of the Intel CPU, which needs time to revert if the execution should be withdrawn, a process that causes a stall if the ensuing instruction depends on the target of the buffer.
However, they still propose some non-trivial mitigations, such as changing the implementation of the JCC instruction to make adversarial execution measuring impossible under any condition, or rewriting the EFLAGS after transient execution to reduce its influence over the JCC instruction.
Update 5/4/23 - An Intel spokesperson has sent BleepingComputer the following comment regarding the paper:
Based on our review of the researchers’ report, this does not describe a new vulnerability. Existing mitigations for Meltdown will address the example in the paper.
However, we were not informed of this paper or contacted by the research team prior to publication. As always, we encourage security researchers to participate in coordinated vulnerability disclosure and report issues to us before publishing them so we can take any steps necessary to safeguard the security of customers and end users.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now