
Security researchers have found four major security vulnerabilities in the BIOSConnect feature of Dell SupportAssist, allowing attackers to remotely execute code within the BIOS of impacted devices.
According to Dell's website, the SupportAssist software is "preinstalled on most Dell devices running Windows operating system," while BIOSConnect provides remote firmware update and OS recovery features.
The chain of flaws discovered by Eclypsium researchers comes with a CVSS base score of 8.3/10 and enables privileged remote attackers to impersonate Dell.com and take control of the target device's boot process to break OS-level security controls.
"Such an attack would enable adversaries to control the device's boot process and subvert the operating system and higher-layer security controls," Eclypsium researchers explain in a report shared in advance with BleepingComputer.
"The issue affects 129 Dell models of consumer and business laptops, desktops, and tablets, including devices protected by Secure Boot and Dell Secured-core PCs," with roughly 30 million individual devices exposed to attacks.
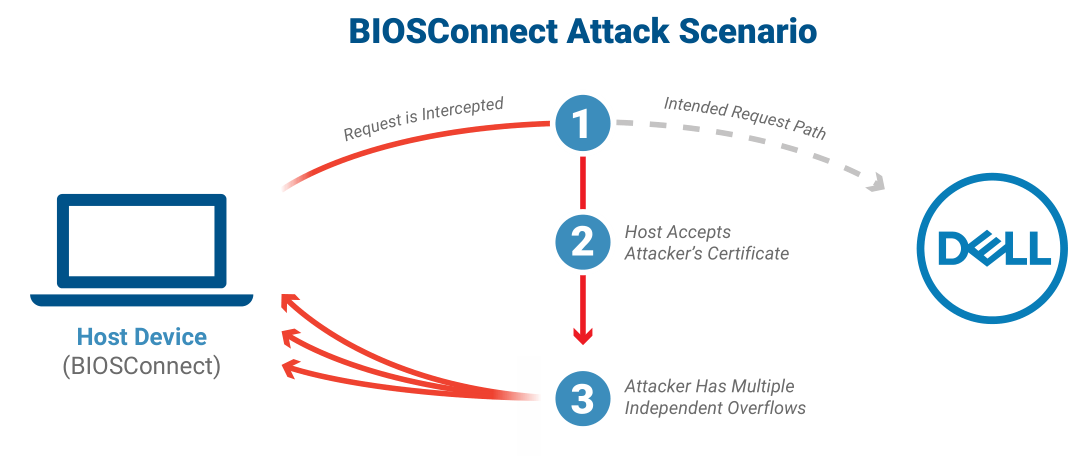
The reasearchers identified one issue leading to an insecure TLS connection from BIOS to Dell (tracked as CVE-2021-21571) and three overflow vulnerabilities (CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574).
Two of the overflow security flaws "affect the OS recovery process, while the other affects the firmware update process," Eclypsium says. "All three vulnerabilities are independent, and each one could lead to arbitrary code execution in BIOS."
Additional info on the vulnerabilities can be found in Eclypsium's report and the complete list of affected device models in Dell's advisory.
Users advised not to use BIOSConnect for updating their BIOS
According to Eclypsium, users will have to update the system BIOS/UEFI for all affected systems. The researchers also recommend using an alternate method other than the SupportAssist's BIOSConnect feature to apply BIOS updates on their devices.
Dell is providing BIOS/UEFI updates for impacted systems and updates to affected executables on Dell.com.
CVE-2021-21573 and CVE-2021-21574 don't require require additional customer action as they were addressed server side on May 28, 2021. However, the CVE-2021-21571 and CVE-2021-21572 vulnerabilities require Dell Client BIOS updates to be fully addressed.
Users who cannot immediately update their systems can disable BIOSConnect from the BIOS setup page or using the Dell Command | Configure (DCC)'s Remote System Management tool.
"The specific vulnerabilities covered here allow an attacker to remotely exploit the UEFI firmware of a host and gain control over the most privileged code on the device," the researchers concluded.
"This combination of remote exploitability and high privileges will likely make remote update functionality an alluring target for attackers in the future, and organizations should make sure to monitor and update their devices accordingly."
Dell software plagued by critical flaws
This is not the first time owners of Dell computers have been exposed to attacks by security vulnerabilities found in the SupportAssist software.
Two years ago, in May 2019, the company patched another high-severity SupportAssist remote code execution (RCE) vulnerability caused by an improper origin validation weakness and reported by security researcher Bill Demirkapi in 2018.
This RCE allowed unauthenticated attackers on the same Network Access layer with targeted systems to remotely execute arbitrary executables on unpatched devices.
Security researcher Tom Forbes found a similar RCE flaw in the Dell System Detect software in 2015, allowing attackers to trigger the buggy program to download and execute arbitrary files without user interaction.
SupportAssist was again patched one year later, in February 2020, to address a security flaw due to a DLL search-order hijacking bug that enabled local attackers to execute arbitrary code with Administrator privileges on vulnerable devices.
Last but not least, last month Dell addressed a flaw making it possible to escalate privileges from non-admin users to kernel privileges, a bug found in the DBUtil driver that ships with tens of millions of Dell devices.
.jpg)

Comments
SleepyDude - 2 years ago
The correct link for the Eclypsium's report is
http://www.eclypsium.com/2021/06/24/biosdisconnect/
The Dell advisory is not available!
serghei - 2 years ago
That’s the link I used and it looks like Dell has now also published their advisory.
SleepyDude - 2 years ago
"That’s the link I used and it looks like Dell has now also published their advisory."
When i checked the link https://eclypsium.com/2021/06/24/biosdisconnect/ didn't work!
Now all the links work fine including the Dell advisor.
Thanks.
catinahat - 2 years ago
According to the Dell advisory there was a BIOS released for this for my XPS 17 9700 on June 9th, which I already updated to on the 10th I think. However I did not know about this issue, so I used the Dell Update utility to both check for updates and install them - BIOS included. This method would have put my machine at risk, which I obviously had no idea of at the time. So now I'm not sure if I have this issue on my machine already (waiting to be triggered through the next BIOS update) as a result of using the Dell app to update, even though the BIOS I updated to supposedly fixes it. Does it still fix it if the remediating BIOS was installed with Dell Update/Dell Support Assist?? Anybody know?
saluqi - 2 years ago
I have a 6 year old Dell desktop (XPS 8700), originally WIn 7 Pro, "legacy" (BIOS) boot mode, BIOS A14 installed 5/31/2019 using Dell SupportAssist, and a 6 year old Dell laptop (Inspiron 15R 5537), original Win 8 Home, UEFI boot mode, Bios A12 installed 5/27/2019 using Dell SupportAssist -- both supposedly still current. Both machines upgraded to Win 10 long ago.
Desktop now running Version 21H1, laptop now running Version 20H2. Had a "feeling" about SupportAssist and stopped using it a couple of months ago.
Question arising: what do I need to do to get back on safe ground? Have not yet received any notification from Dell.
catinahat - 2 years ago
Yes, what the Dell advisory fails to make clear, is whether the remediating BIOS updates simply prevent you from falling victim to this MTM attack if you haven't already, or whether it also protects users whose machines have the exploit on the system just waiting to be triggered (as a result of past BIOS updates with Support Assist or OS recovery back ups made by BIOSConnect). It also fails to provide you with know way of knowing if you've already fallen victim.
strombrg - 2 years ago
Is Linux impacted or not? What models of Dells are impacted?
The days of ignoring Linux should be over. It comes preinstalled on some Dells.
I received two different BIOS updates on my Linux-installed Dell recently. Does that cover it?